- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Required role to do cli backups
- LIVEcommunity
- Discussions
- General Topics
- Re: Required role to do cli backups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Required role to do cli backups
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 08:17 AM
We have a process to do backups using the cli. I'm going to create a new role restricted to cli for this purpose. What admin role is required to perform backups?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 07:32 PM
from cli, the admin role would be deviceadmin.
I tried deviceadmin-readonly.. and naturally the choices are different
as deviceadmin
testadmin@Cantwell-PA-220#
check Check configuration status
commit Commit current set of changes
copy Copy a statement
delete Delete a data element
edit Edit a sub-element
exit Exit from this level
find Find CLI commands with keyword
load Load configuration from disk
move Move a node within an ordered collection
override Override a template element
quit Quit from this level
rename Rename a statement
revert Revert changes from configuration
run Run an operational-mode command
save Save configuration to disk
The deviceadmin-readonly does not offer the same choice:
testadminro@Cantwell-PA-220#
check Check configuration status
edit Edit a sub-element
exit Exit from this level
find Find CLI commands with keyword
quit Quit from this level
run Run an operational-mode command
show Show a parameter
top Exit to top level of configuration
up Exit one level of configuration
Just remember a deviceadmin from CLI can make whatever changes they want... they ARE a device admin, with full capabilities.
There is NO ability to restrict an account to ONLY allow saves/backups individually.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2020 09:12 AM
What about using a tool like CatTools to capture the output of 'show config running' ? The readonly permissions lets the user run this command.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 05:45 AM
Hi Mike
From a RO account, there is the command "show config running" and the output is in xml format.
testadminro@Cantwell-PA-220> show config running
config {
preferences {
saved-log-query {
traffic {
h323 {
query "( addr.src in 172.17.13.13 ) and ( app neq dns ) and ( app neq dhcp ) and ( app neq ntp ) and ( receive_time geq '2019/01/14 16:59:32' )";
}
}
}
}
}
expedition {
permissions {
role-based {
superuser yes;
}
}
phash ********;
}
fred;
testadmin {
permissions {
role-based {
custom {
So, to summarize, there does not seem a good ability to load a config in "set" notation, but could export with 1000s of lines as XML.
Any other questions I can answer for you?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 09:40 AM
What are you saying here? Are you saying that if the config is exported as XML that there is no ability to restore it?
"So, to summarize, there does not seem a good ability to load a config in "set" notation, but could export with 1000s of lines as XML."
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 01:35 PM
What I was suggesting is that config management is best done via the GUI vs from CLI.
You can properly create a customized role to allow export/import of config file, using WebUI.
But from CLI, you are very/extremely limited in permissions, hence very difficult, almost impossible, for config administration.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 01:59 PM
Do you know if the output of 'show config running' in an xml file can be used to restore the config?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 03:48 PM
Hi Mike.
I think I should clarify my comments, as I would not want to mislead information here.
The original request was that you wanted an admin-role from CLI that could do backups.
My interpretation was that you ONLY wanted the person to do backups and not have any other access.
That is not possible feasible to provide a RO account, with ability to export configs (or upload configs), whether that is a single line, or full config.
It is definitely possible to choose a CLI admin role of "device admin". This will allow the user to do whatever they want from CLI, import/export, look at the config in "set" notation etc. But it also comes with the ability to admin the entire firewall from CLI.
So, if you created a custom admin-role and remove all GUI privileges, then the person would not be able to log into the FW GUI to make changes. On the flip side... by allowing them to be a device-admin from cli, allows them to manipulate the config to give them back permissions that were taken away from the GUI... well, see, that is not right either.
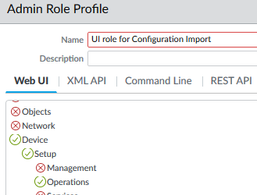
So, as an engineer, what to do. My recommendation is create a GUI role (not from cli) that has access only to the Operations Tab... as such.
Everything (like EVERYTHING is disabled, so when a admin logs in.. only choice they have is the menu options under Operations.
Does this help you out a little more... Don't restrict yourself to CLI only. Learn what the UI can do, and allow UI access.
Much easier and you will keep your hair. 😛
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2020 02:24 PM
The GUI was a limiting factor in this scenario, but thanks for the information. We're after an automated solution, so maybe Panorama or API.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2020 04:06 PM
With API and a small script works perfectly
- 6294 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions
- ION Device AAA - Tacacs+ Attributes in Prisma SD-WAN Discussions
- HA Active‑Passive 3420 Both Nodes Stuck – Suspecting LACP Issue in Next-Generation Firewall Discussions
- Can Prisma Cloud get AWS security findings without integration with Security Hub? in Prisma Cloud Discussions
- API Key Required Permissions for Set a User Role in Cortex XDR Discussions