- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
security policy source user strange behavior
- LIVEcommunity
- Discussions
- General Topics
- Re: security policy source user strange behavior
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
security policy source user strange behavior
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2020 02:57 AM
Hello
I am using ldap users as source user in security policy.
The policy defines who can access http-service and https-service to the internet.
After the Firewall there are about 500 PCs and about 10% PCs stop to browse the internet every 20-30min, pressing F5 in the browser seems to solve.
The only thing that I understood is that the problem is always in those PC.
Removing the source user limitation this problem disappear.
Any idea on howto debug this ?
thanks very much
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2020 09:27 AM
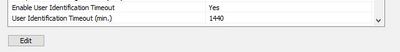
try to increase user identification timeout (min) from default 45 to 8 hours (480)
for debug overide interzone default policy and log session start.
look for traffic with no source user.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2020 04:15 PM
Do you see an intermittent blank 'source user' value on traffic logs (Monitor > Traffic) once it fails?
You may verify this by filtering in traffic logs the following: ( user.src neq 'source-user' ) and ( addr.src in x.x.x.x ).
If that is the case, most likely the User-to-IP mapping is being lost due to Timeout. Ref doc:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClZzCAK
You can either increase the User Identification Timeout or remove the check from the Enable User Identification Timeout.
More information about User Identification Timeout: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PNVyCAO
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-11-2020 01:39 PM
Thank you both for the answers.
at the moment i disabled the user identification in the policies, to keep people work.
I noticed that pc/user with problem are always the same.
And the interruption (i see the empty user in url filtering) is less of the 45min set in the timeout setting.
next week I will set up a little lab where to try to reproduce the problem.
should I look at the user id agent server to find something ?
Giacomo
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-12-2020 12:35 AM
this will be easy to diagnose without a lab.
Just clone your HTTP/HTTPS policy that has no user identification and call it user-test.
add this directly above and allow with source user ID.
This will not block users as they will drop down to the next policy that will allow if no user id is found.
monitor the traffic for http(s) and when a user is using user-test then you know user id is working for them.
If you see a user on the other policy then search for that user on the server agent under "monitoring".
if the search is blank then the ip address associated with that user may have timed out.
please note that the user timeout has nothing to do with timestamps on traffic monitor, it is the time since the ip address was last observed in the security logs by the agent. so a user could be fine at 10:44 and at 10:46 no traffic. this is because they registered their ip address at 10:00 and it has now timed out.
if it applies to a particular set of users then this could be because their domain activity is not as frequent as others.
on the server agent you can increase timeout here under setup.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-15-2020 02:44 AM
I increased the timeout to 600, but when I launch:
show user ip-user-mapping all type UNKNOWN
I always see about 10-15 PCs in the unknown list.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-15-2020 02:51 AM
The new user mapping timeout will only start on the next new mapping, are you monitoring AD security logs.
If so then get user to log out and back in to update security log on AD.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-15-2020 08:39 AM
this will be easy to diagnose without a lab.
Just clone your HTTP/HTTPS policy that has no user identification and call it user-test.
add this directly above and allow with source user ID.
I can see a lot fo empty "source user" in "Monitor/Url Filtering" also without that rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2020 06:59 AM
I tried to add a third User-id Agent.
What's the need of User Identification > User Mapping > server monitoring tab ?
If I press discover my DC's are listed, but with the access denied error.
thanks very much for yours help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2020 07:05 AM - edited 12-17-2020 07:08 AM
have you setup a server monitor account in the agent setup?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2020 03:20 PM
yes it is configured.
I meant, is server monitor only need for wmi probing ?
- 6956 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- port issue / nmapping in Next-Generation Firewall Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- Strange Gateway change issue on network with Prisma Access GP Client in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions