- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User authentication - Global Protect
- LIVEcommunity
- Discussions
- General Topics
- Re: User authentication - Global Protect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 07:20 PM
HI.
I'm pre-staging a couple of PA2020's (active/passive), and am having an issue with getting authentication via AD working for Global Protect through Active Directory.
As far as I can tell, the LDAP configuration is correct - the firewall connects to the agent, and gets a list of users from the groups I have configured to be allowed - but every time I try to login to the portal, it fails, and I get the following log entries
GlobalProtect portal user authentication failed. Login from: XXX.XXX.XXX.XXX, User name: domain\first.last, Reason: Authentication failed: Invalid username or password . | 09/21 12:05:38 |
User 'domain\first.last' failed authentication. Reason: Invalid username/password From: XXX.XXX.XXX.XXX. | 09/21 12:05:38 |
(I've sanitized the actual details, obviously).
I *know* the user is in the AD group which is in the allowed list - a CLI query shows the following output
admin@Gate(active)> show user group name domain\vpn-users
group short name: domain\vpn-users
[11 ] domain\first.last
Can anyone suggest where I might be going wrong? I've tried every possible combination/form of username, and I know I'm using the correct password - is there any way from the CLI to try and verify what is going wrong?
Thanks.
- Labels:
-
Configuration
-
Set Up
-
Troubleshooting
-
User-ID
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2013 01:48 PM
Yeah, I got it right eventually.
It was a rather contorted process, and the documentation I found is somewhat dated and doesn't apply properly to current versions, but with some help from people here I got it working.
It came down to two configuration options I had wrong
In the LDAP server profile, you need to make sure you have your domain in the "Domain" section of the configuration - the documentation indicated I could leave that blank, but this is *not* the case.
In the Authentication profile group list, you need to enter your group in domain\group format, not in DN string format (which the firewall defaults to) - so instead of cn=<group>,dc=<domain>,dc=<suffix> format you need to put domain\group - you will likely need to manually enter this in the correct format.
There's a whole bunch of CLI troubleshooting you can do - if you can't get it working, do a search on discussions started by me with the title "LDAP Authentication not matching user groups", and you should find more hints.
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 07:31 PM
Did you actually create an authentication profile and use this in the gp configuration ? I believe your authentication profile settings might not be correct. You can create an authentication profile as shown for the users like in the below pic and can use the same in the gp config.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 07:42 PM
Yes, I have created an Authentication Profile. Picture shown below
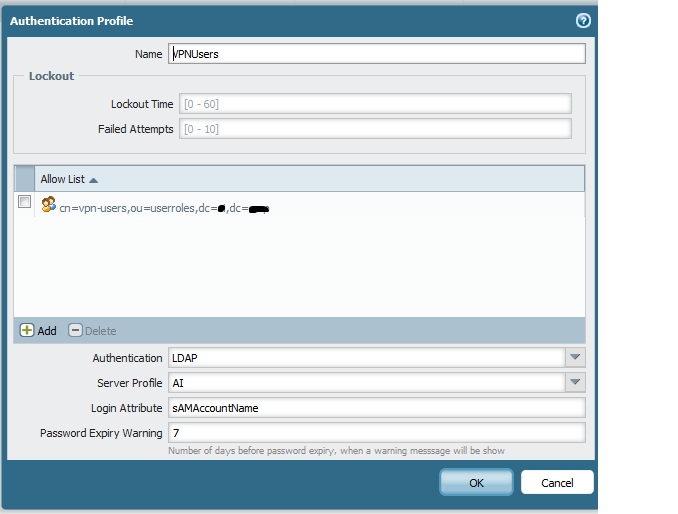
I couldn't commit the GP setup until I had it.
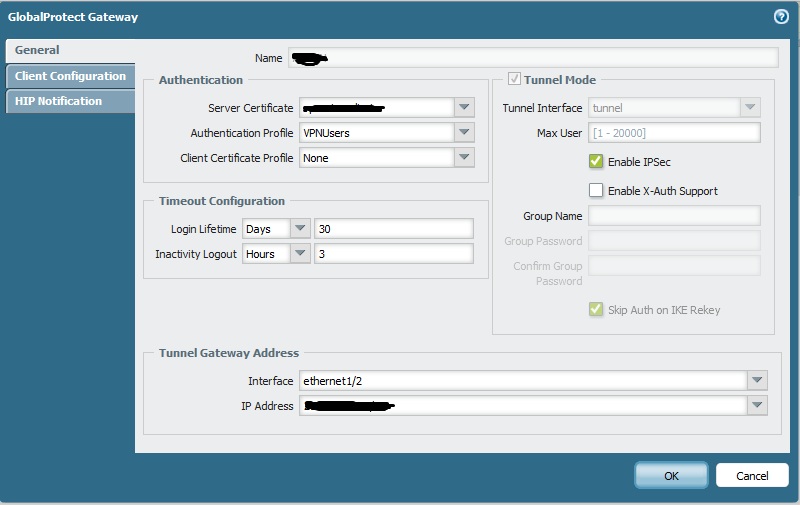
The GP is setup as follows
Gateway Config
Portal config
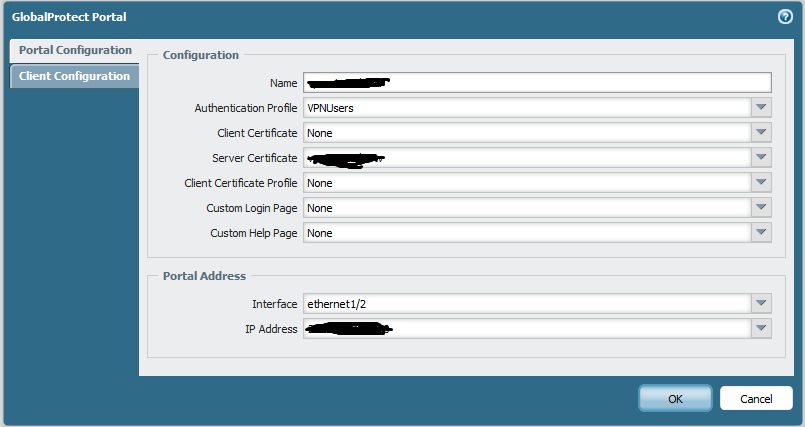
I'm open to other suggestions.
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 07:50 PM
If you believe the configuration is correct. From the CLI you can verify the whole authentication process from the logs. While you are trying to connect via gp and doing authentication, please open a cli session run the below command and look for the information in this log.
"tail follow yes mp-log authd.log"
You can actually look the firewall sending the authentication requests to LDAP server for the gp users and LDAP server replying back with the results.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 08:40 PM
OK, I did that, and got the following output.
Sep 21 13:37:48 pan_authd_service_req(pan_authd.c:2604): Authd:Trying to remote authenticate user: domain\darren.gibbs
Sep 21 13:37:48 pan_authd_service_auth_req(pan_authd.c:1115): AUTH Request <'vsys1','VPNUsers','domain\darren.gibbs'>
Sep 21 13:37:48 Error: pan_authd_get_sysd_multivsys(pan_authd.c:3527): failed to fetch: NO_MATCHES
Sep 21 13:37:48 pan_authd_common_authenticate(pan_authd.c:1511): Authenticating user using service /etc/pam.d/pan_ldap_vsys1_:v:p:n:users_0,username domain\darren.gibbs
Sep 21 13:37:48 pan_authd_authenticate_service(pan_authd.c:663): authentication failed (6)
Sep 21 13:37:48 pan_authd_common_authenticate(pan_authd.c:1531): Authenticating user using service /etc/pam.d/pan_ldap_vsys1_:v:p:n:users_0,username domain\darren.gibbs failed - trying other hosts
Sep 21 13:37:48 pan_authd_common_authenticate(pan_authd.c:1506): Skipping LDAP server due to missing Auth-Profile: pan_ldap_vsys1_:v:p:n:users_1
Sep 21 13:37:48 pan_authd_common_authenticate(pan_authd.c:1506): Skipping LDAP
Now, the errors tell me there's obviously something wrong - but I can't figure out what. I'm sure it's something simple, but I'm stuffed if I know what.
Any ideas will be tried.
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 08:55 PM
I just had a thought.
What path are these authentication requests passed through? The management interface, or the actual dataplane interface? I have the management interface connected and able to talk to the domain controller, but the dataplane interfaces are only connected to dummy ports on a stand-alone switch (to bring them up), they're not actually connected to the live network.
Could this be causing the problem, or would the authentication be handled over the management interface?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 09:10 PM
The authentication requests to domain controller are passed through the mgmt interface. Just curious, you said you have the data plane interfaces connected to dummy interfaces ? then how are the gp clients connecting to the firewall ? ![]()
From the previous logs I see that the actual user information is being sent to the LDAP server and it seems like the server is not able to match the user info.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2012 09:13 PM
There are no "clients" - there is one "client" - me. 🙂 I've plugged my laptop direct into the "outside" interface and assigned it my Internet router's IP address, so it's "pretending" to be the Internet.
The source packet is coming from an external address, so the firewall just sees the client as another outside IP.
I don't know how the server is not matching the username - I can list the users in the group from the CLI, and the username I'm entering is in the group.
Is there some way to debug the agent on the server which might shed some light?
Message was edited by: Darren Gibbs
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2012 12:39 AM
We can try these things and see if it helps
1) One the LDAP server you can go to security events of the server and look out for the login auth tickets and see if the server is actually getting the LDAP queries from the firewall, if so the reason for the denial of the user.
In the below document you can the actual event IDs for logon/log off events on the windows server.
https://live.paloaltonetworks.com/docs/DOC-1262
2) We can try removing the LDAP filter for users in the authentication profile and allow all users temporarily and authenticate see if that works.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2012 01:32 PM
Well, I know the LDAP server is working because if I add individual users into the "allow" list one at a time, they authenticate properly.
It just won't enumerate the group members.
I can work around it, but I'd really like to know WHY I can't use an AD group membership for authentication.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2013 05:46 AM
We have a comparable issue.
What I see is that when i login to global protect using a domain user domain\user and then look at the traffic logs I only see user
When I use rules from the globalprotect zone to the network using domain\group names they do not work. If i add user they work. In other zones adding user does not work because I have to add domain\user.
Did you ever get this sorted out ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2013 01:48 PM
Yeah, I got it right eventually.
It was a rather contorted process, and the documentation I found is somewhat dated and doesn't apply properly to current versions, but with some help from people here I got it working.
It came down to two configuration options I had wrong
In the LDAP server profile, you need to make sure you have your domain in the "Domain" section of the configuration - the documentation indicated I could leave that blank, but this is *not* the case.
In the Authentication profile group list, you need to enter your group in domain\group format, not in DN string format (which the firewall defaults to) - so instead of cn=<group>,dc=<domain>,dc=<suffix> format you need to put domain\group - you will likely need to manually enter this in the correct format.
There's a whole bunch of CLI troubleshooting you can do - if you can't get it working, do a search on discussions started by me with the title "LDAP Authentication not matching user groups", and you should find more hints.
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2021 11:48 AM
I'm also facing same issue. When I have call specific user group in authentication profile and after that called in global protect portal and gateway but at time of login in gp then showing invalid user name and password showing logs login failed,But If i called all user in authentication profile then login successful showing.
I have use user id tefreash group mapping all command then check users in group showing my 45 users in group.
Please suggest me solution
- 1 accepted solution
- 33796 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Pre-Populate Multipule Portal Addresses in GlobalProtect Discussions
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Can you configure clientless VPN in SCM ? in GlobalProtect Discussions
- global protect connection failed authentication failed !!! in GlobalProtect Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager



