- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User-ID - wrong user domain
- LIVEcommunity
- Discussions
- General Topics
- Re: User-ID - wrong user domain
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
User-ID - wrong user domain
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2013 05:40 AM
Hi there,
We discovered an issue with our User-ID setup in our BranchOffices. Some times the source user is not recognized as <child-domain>\<user> but as <parent-domain>\<user>. This happens from time to time but only for a short perioid of time (less than 30 seconds).
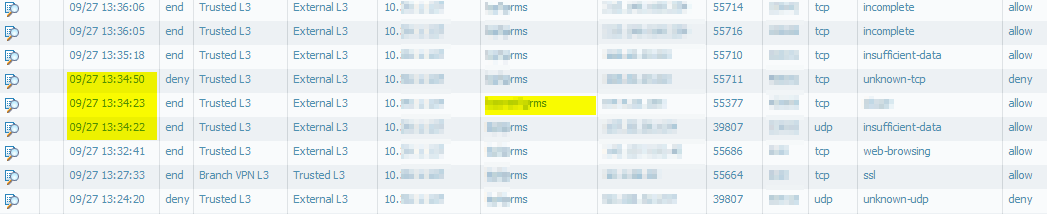
Does anyone have an idea on how we could further troubleshoot this issue?
Here's our setup:
BranchOffice:
- PA-200 (v5.0.7)
- Local Domain Controller (Win2012) --> <child-domain>
- Local PA-200 queries the security log of the local DC every 2 seconds, no WMI probing
- In addition two User-ID agents are configured. The two agents are hosted on servers in the HQ (see below).
Headquarters:
- PA-2050
- Four local Domain Controllers (Win2012) --> <parent-domain>
- One Backup Domain Controller (Win2012) --> <child-domain>
- Two servers with User-ID Agents installed (not installed on DCs directly). The User-ID agents query only local DCs, meaning the four DCs of the parent domain plus the backup DC of the child-domain.
So the local PA-200 has two sources to get user-ip mapping information from:
- The local DC
- The two User-ID agents in the HQ
That user only exists in the child domain but it uses various services hosted in the parent domain (like MS Exchange).
Any help is appreciated.
Thanks,
Oliver
- Labels:
-
Set Up
-
Troubleshooting
-
User-ID
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2013 01:22 PM
When you filter the sessions with different(wrong) domain do you see anyhting common with these sessions ?
How many Ldap profile do you have ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2013 01:57 PM
The PA 200 you said scours the ,local DC logs and so I presume you have an Agentless UserID agent there.
Could you please check to see if this Agentless userID is set for "session read" Device>>UserID>>User Mappinig>> Enable Session (is this checked)?
If so, this means that when a user from the Child Domain uses one of the resources (like MS Exchange / file server), that user is logged and mapped. You stated that "That user only exists in the child domain but it uses various services hosted in the parent domain (like MS Exchange)" At the time that the user goes to one of these resources he/she gets logged with the Parent Domain
If you'd like to NOT see the user with the Parent Domain, disable "Enable session" (Uncheck the box) so when a user does access those MS resources they are not mapped/logged with the Parent domain
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-29-2013 06:31 AM
Thank you both for your hints.
@panos
I prepared a log filter that shows me the entries with the wrong (parent) domain. I don't see any specific pattern so far. Most connections are logged to "External L3" zone but but there are also some that egress on the "Branch VPN L3" or "Branch MPLS L3" zones... Destination IPs and ports didin't reveal any pattern to me. But still a good hint for troubleshooting.
@sjamaluddin
You're right. The local PA-200 uses an agentless setup to query the local domain controller. You're also right that the "Enable Session" option is checked. I just disabled that option. I'll re-check the firewall logs after tomorrow to see if the issue disappeared. I'll keep you posted.
Is it advised to disable that option in a multi-domain environment in general? Should we disable it on the UserID agents in HQ as well?
Thanks a lot!
Oliver
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 06:54 AM
Dear all,
The "wrong domain" issue seems to be gone as of now. At least we didn't see any log entry with the wrong domain so far. Thanks a lot for this hint.
However, we're now facing another issue that seems to be related with this change. Suddenly for some connections the source user isn't detected at all:
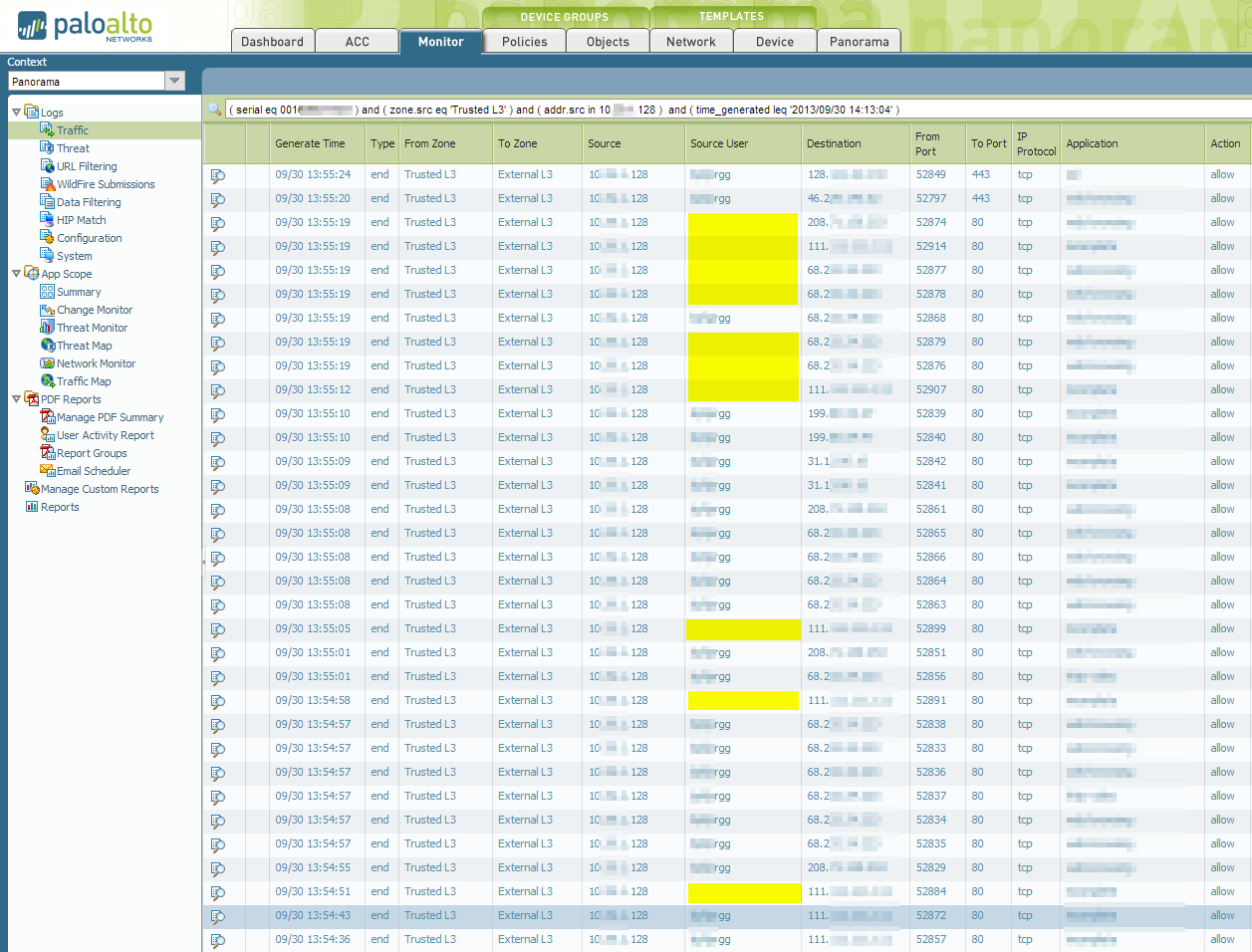
Thank you very much!
Oliver
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2013 01:33 AM
Anyone? I think we need to check this "Enable Session" again as people are already complaining 😞
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2013 10:17 AM
That should not be related to session read, because as I see from logs 2 logs with same source dest. ip and port, and 1 have user and other not.That seems strange to me.
I wonder if you can just use user-id agent and disable completely agentless system or not.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2013 12:36 PM
Hmm, I guess we can try that. But we only have UserID agents installed on servers in the HQ. That would mean these two agents would have to query the remote DC in the branch office over WAN...
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2013 10:49 AM
If there are users that have disappeared completely since disabling Server Session, are you not logging those users through a regular AD log on event? Could you check whether or not there is a log on entry for those users in AD
If Server session is the only way you were logging those users then that may explain why those users have disappeared from your logs (and why they may not be falling in the correct security rules).
Please ensure that the DC has these users' log on events and if not - then that would imply that you are only using server session to map these users in which case you may be forced to re-enable server session.
- 6902 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Name Normalization issue in GlobalProtect Discussions
- UserID periodic empty groups issue in General Topics
- UserID Redistribution Filters working weirdly in Next-Generation Firewall Discussions
- Service Account used for UserID Agent in Next-Generation Firewall Discussions
- Global Protect and User_ID/Group Mapping in GlobalProtect Discussions



