- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Error: Certificate failed to load: invalid certificate chain
- LIVEcommunity
- Discussions
- General Topics
- Error: Certificate failed to load: invalid certificate chain
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Error: Certificate failed to load: invalid certificate chain
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2015 02:33 AM
Hi there,
I generated a CSR with PAN-OS 6.1.3 and submitted it to our Microsoft AD CA with subordinate CA template. After uploading the certificate it shows up under the root CA certificate of our domain. But when commiting the changes I get an "Error: Certificate failed to load: invalid certificate chain" error message. What have I done wrong?
The CSR was generated with one main CN as FQDN of both firewalls (leinf-pa-3020-rz.domain.de, it's a HA cluster) and their own management IP adresses and FQDNs for usage as the WebUI certificate.
This is how it looks in the WebUI:
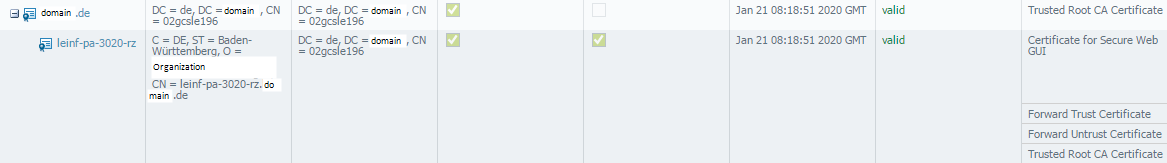
I tried adding the root cert data into the subordinate cert, and when I export it again it is still in there. So why is it complaining about the chain?
Kind Regards
Christian
- Labels:
-
Configuration
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2015 09:16 AM
The error about the Certificate chain is just that.
In order for the chain to be complete, it must have the Root-level CA public cert, the Intermediate-level CA public cert (if any) then the Subordinate CA cert, then the Subordinate CA can be the Certificate Authority and create the certs.
Now, if you do not know the full chain, take the Subordinate CA, and then double click on the .cer or .crt file , then click on the Certificate Chain (last tab) and then click on each one up the chain: and you can save off each one and then import it into the Certificates section to ensure the full path is present.
Does that make any sense? If not, please let me know, and I will try to provide screenshots.
Stay Secure,
Joe
Don't forget to Like items if a post is helpful to you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2015 10:03 PM
The complete chain is shown in the Web GUI screenshot. There is only the Root CA from our AD and then the Sub CA certificate for the devices, no intermediates. Viewing the cer file confirms this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-14-2015 08:49 AM
Here is what you can try,
+++ Separate all the certificates in the chain as jdelio suggested.
+++ Open the FW certificate in a notepad. You will find the complete chain there. Just keep the FW certificate in there and remove the other Intermediate and Root certificates. Save it. Make sure not to have an additional, extra spaces.
You can check the certificates using the following link,
https://www.sslshopper.com/certificate-decoder.html
+++ Once done, import the FW certificate first, then intermediate, then root.
Let me know if this works.
Regards,
Rahul
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-14-2015 11:06 PM
Thanks for all your help, this is what finally did the job:
Remove all certificate functions to another (I had the original selfsigned still on the box) and commit.
Export the new certificates with private keys.
Delete the whole chain of the new certificate and commit.
Add the SubCA and then go up the chain and add the other ones and commit
Add the needed functions back to the SubCA and remove them from the (temporary) selfsigned and commit.
Just replacing the originals seemed to be what didn't work. A complete removal and readding did the trick
Regards,
Christian
- 12414 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal
- XDR Certification - new version in Cortex XDR Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Palo Alto does not support global certificates. Is there a solution? in Next-Generation Firewall Discussions



