
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Palo Alto Networks reviews how Cortex XSOAR and SlashNext work together for automated phishing investigation and response. Read how this feature can help your SecOps and threat intel teams.
Cortex XSOAR is the industry's first extended security orchestration, automation, and response platform with native threat intel management that empowers SecOps and threat intel teams with incident response capabilities against threats across the enterprise.
Through integration with SlashNext, Cortex XSOAR and SlashNext users can access SlashNext phishing URL analysis and enrichment from within Cortex XSOAR to get accurate, definitive binary verdicts on suspicious URLs and enable higher level automation and throughput for phishing IR and threat-hunting playbooks.

Once the phishing email is ingested into Cortex XSOAR, the corresponding playbook automatically runs and performs preliminary checks, such as whether the email contains URLs or any file attachments. The playbook task performs several actions such as rasterizing the email body and making it available within XSOAR for viewing. If the phishing email contains urls, then the playbook task automatically investigates the URL with SlashNext integration and adds the details to the context.

The integration with SlashNext provides detailed information that includes URL details, verdict, ScanID, ThreatStatus, ThreatName, ThreatType, FirstSeen, LastSeen, and more. The playbook will test for the reputation of the URL, and, if found Malicious, then the playbook sets the incident severity to high. This further helps SOC teams to prioritize this incident for speedy investigation and closure.
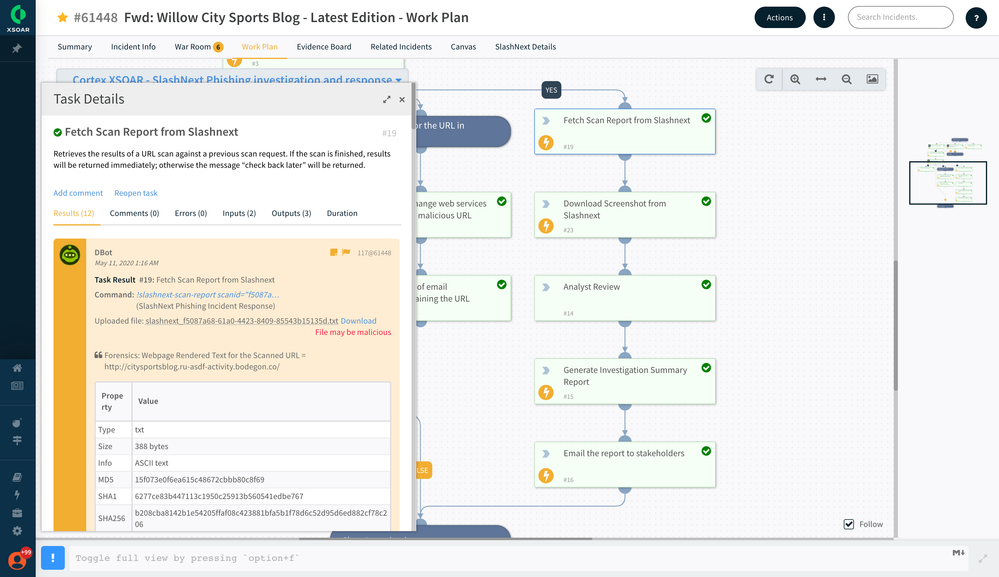
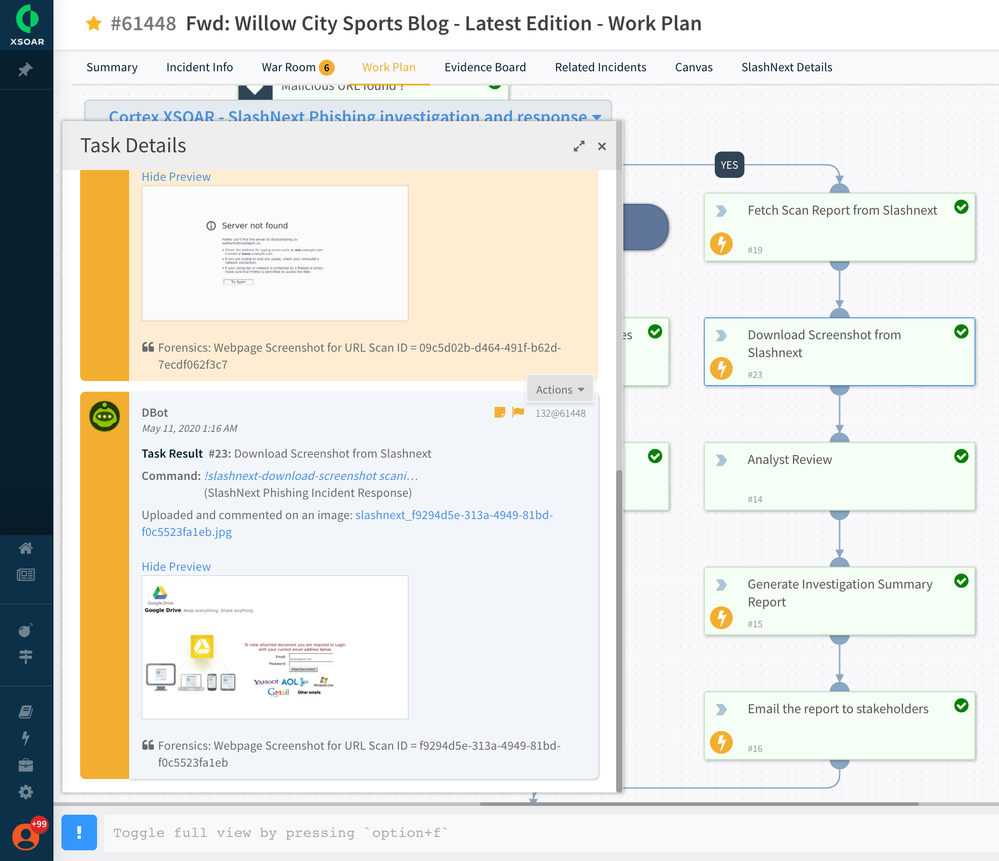
The investigation may require the ability to perform lookups on corporate mailboxes to check if any other employees received emails containing the malicious URL. In this example scenario, Cortex XSOAR playbook automates the look-up action using the integration with Microsoft EWS and retrieves the list of employees who also received such emails.

As a standard best practice, the playbook can be used to automatically notify the lead analyst for a final review, generate a summary report, and email the report to relevant stakeholders before closing the investigation. For retrospective analysis, the SOC team can always view the case management section for the corresponding incident for viewing the investigation and closure details that will be preserved for reference purposes.
For more information about Cortex XSOAR, please visit the Cortex XSOAR page on LIVEcommunity.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like |




