
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The proliferation of unsanctioned Post-Quantum Ciphers leads to blind spots in your network visibility, with PANW Firewalls you can now DETECT, LOG and BLOCK unsanctioned ciphers.
The Quantum Threat of a Cryptographically Relevant Quantum Computer’s (CRQC) ability to break existing encryption and break the security and privacy fabric is one of the most significant threats we’ve encountered since cryptography became widely accepted about four decades ago. As a result, the United States White House has issued a mandate for companies to prepare now (!) for a post-quantum world.
On the one hand ‘Harvest Now, Decrypt Later’ attacks are primarily led by nation-states where encrypted sensitive data is stored to be decrypted later by a CRQC, an attack on the rise. In addition, there is increasing adoption of unsanctioned or non-standard ciphers by popular browsers like Google Chrome or CDN proxies like CloudFlare to promote experimentation and migration to a post-quantum secure world.
Combatting harvesting attacks means migrating away from potentially weakened encryption methods, which include DH, RSA and ECC to replace them with Post-Quantum Cryptography (PQC) like the Crystals Lattice-based KEM and DSA. Today’s enterprises are met with an interim threat that can go completely unseen - the insider threat!
We were the first and only to enable this detection back in of April 2023 for all Palo Alto Networks Firewalls, and since then we haven’t yet to see other 3rd party network or traffic monitoring tools in production capture PQCs in use across SSL/TLS traffic. For large enterprises and service providers lack of visibility to PQC-based SSL traffic traversing their network, makes for critical blindspots. All this unobserved & encrypted traffic using PQCs or Hybrid PQCs, are yet to be supported for decrypt-and-inspect by security devices. Without being able to monitor and deep-packet-inspect these experimental PQC-based SSL traffic, enterprise security teams are unable to provide a complete security posture for their corporate users and applications.
End-user browsers, browser plugins, and proprietary point products supporting initiating of PQC-based SSL sessions, and for session termination reverse proxies supporting PQC-based SSL/TLS session offloads, have created an added risk of corporate insiders knowingly or unknowingly leveraging these sessions for malicious activity. Potentially exfiltrating company trade secrets, being victims of spear phishing attacks, or even downloading malware for a more widespread internal attack. These are just a few possibilities of threats that can go undetected merely because of a lack of tracking support for encrypted traffic across your enterprise network infrastructure.
This lack of traffic visibility and traceability of sessions established between a client & server is a top concern Palo Alto Networks heard from our customers back in 2022. To that end, we were the first to respond with signature-based threat detection to identify any use of PQC-based SSL/TLS sessions in corporate networks. In March 2023 we released Threat Signatures through dynamic updates making it available to all our customers globally to start tracking this unseen traffic in their networks.
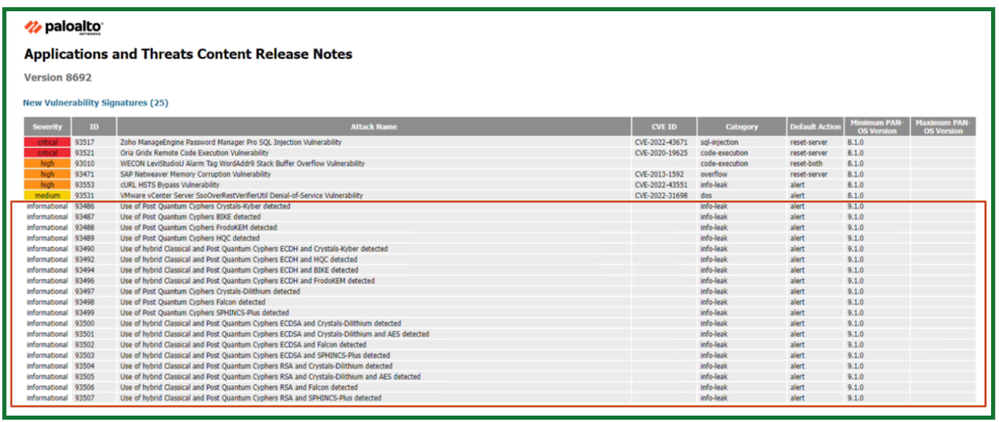
These Threat signatures include PQCs from NIST submissions for Key Exchange and Digital Signatures, as well as Hybrid PQCs i.e. combination of existing ciphers (RSA, ECC) with newer ciphers (PQC). With Threat Logs on any Palo Alto Networks firewall, our customers can receive ALERTs when PQC-based SSL/TLS sessions are established in their network. With the traceability information and the Threat ID, a security engineer is now able to block or audit the user or service if concerned about unexpected insider activity.
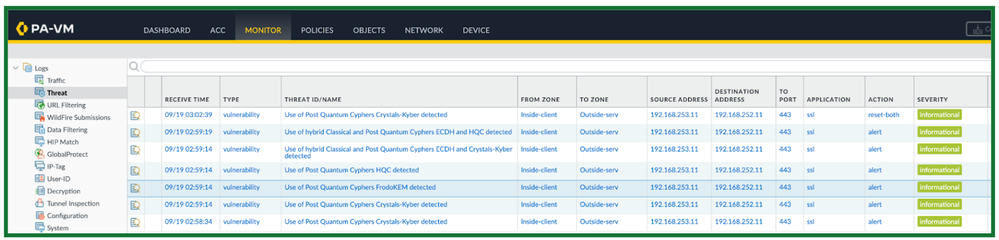
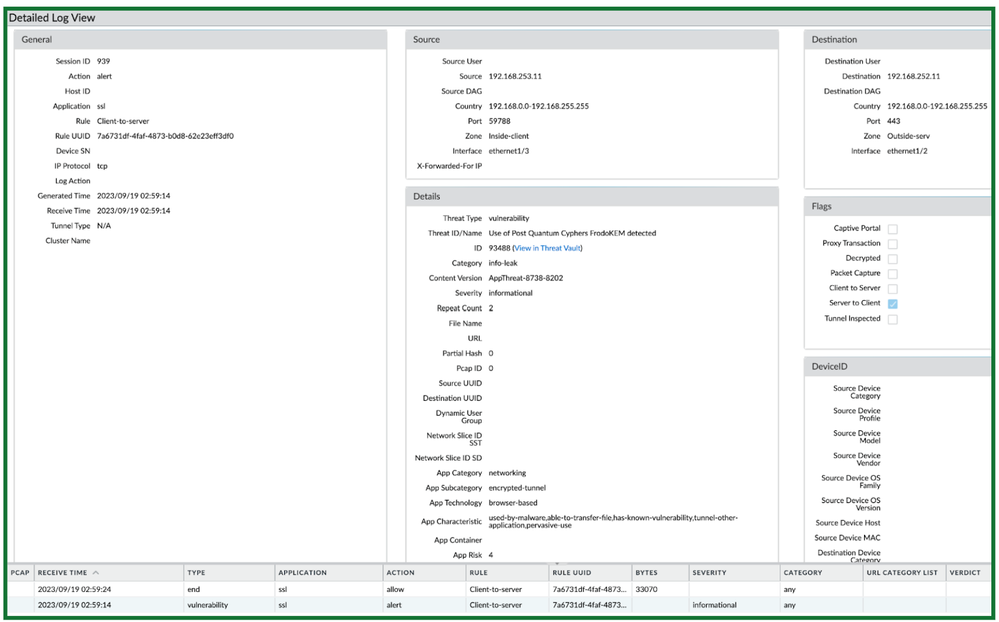
These threat signatures are only phase 1 of detection, we plan to continue to add and detect additional PQCs or newer Hybrid PQCs that will be adopted across the industry, to guarantee to eliminate any blind spots and bring our customers comprehensive traceability to better their security with Palo Networks’ Firewalls. As we approach NIST standardization for Post-Quantum Ciphers and IETF drafts reaching RFC for the implementation of Hybrid of PQCs in TLS 1.3 we will get closer to also supporting break-and-inspect to bring Defense-in-Depth for all our customers to leverage our portfolio of Cloud Delivered Security Services for a complete security posture.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like |




