
Hello everyone,
This week, I would like to talk about VM-Series on NSX.
Because I am a self-proclaimed "car-guy," the first thing that comes to my mind when I hear of NSX is the Acura NSX...but that is not what we're going to talk about today! Far from it, we're going to dive into the VM-Series firewall on VMware NSX—and how it could benefit your environment.
What is NSX?
NSX is VMware's Data Center environment. VM-Series on NSX is Palo Alto Networks' Next Generation Firewall VM-Series running on NSX. Now NSX can come in a couple of different flavors (NSX-T and NSX-V), all depending on the environment.
NSX-T integrates the Palo Alto NGFWs and Panorama with ESXi host servers to provide comprehensive visibility and safe application enablement of all north-south traffic in your NSX-T software-defined datacenter. NSX-V is designed for the software-defined data center (SDDC), offers the ability to deploy the Palo Alto Networks firewall as a service on a cluster of ESXi servers. Please see the deployment guides referenced below for more information on deployment.
Why should I have VM-Series and NSX?
While VMware NSX provides a solid foundation for securing virtualized environments, it only solves a piece of the network security puzzle. VM-Series virtual firewalls help ensure network security and regulatory compliance in VMware NSX environments. This integration offers a series of critical business benefits to organizations that depend on virtualized and hybrid cloud environments to help them stay innovative and competitive.
As virtualized instances, VM-Series deployments help maximize segmentation and micro-segmentation activities by securing traffic that moves between workloads with different levels of trust. This also limits lateral threat movement to halt attacks that migrate from one compromised virtual machine to others in the environment and prevent data exfiltration when traffic moves from a trusted zone to the outside world.
Get the following capabilities with VM-Series on NSX*
- Dynamic Traffic Steering. VMware NSX can intelligently steer traffic to the VM-Series through a simple network policy. This allows the VM-Series to enforce threat prevention policies with the same degree of granularity as NSX, at the individual workload level, without degrading network performance. By deploying the VM-Series, organizations effectively upgrade their threat protection capabilities while simplifying security management.
- Automated Threat Response. Network security architects know the speed of threat response will usually determine the scale of damage. That’s why the VM-Series automates threat response by notifying NSX of the existence of an infected workload, which NSX then tags. The VM-Series uses the NSX tag to enforce a quarantine policy, cutting off the workload’s ability to communicate. This automated response buys network engineers valuable time to mitigate intrusions and update policies to reflect new threat intelligence.
- Automated Policy Provisioning. Tags play a role in another vital VM-Series security capability as well. With developer activities moving quickly, often requiring the creation and destruction of scores of VMs in a short period, many organizations struggle to ensure these VMs are quickly secured with appropriate policies. Because the VM-Series can set policies based on NSX tags, a newly created VM with the appropriate tag automatically inherits a full set of policies without any manual configuration.
*Information reprinted from a Palo Alto Networks whitepaper about VM-Series on NSX.
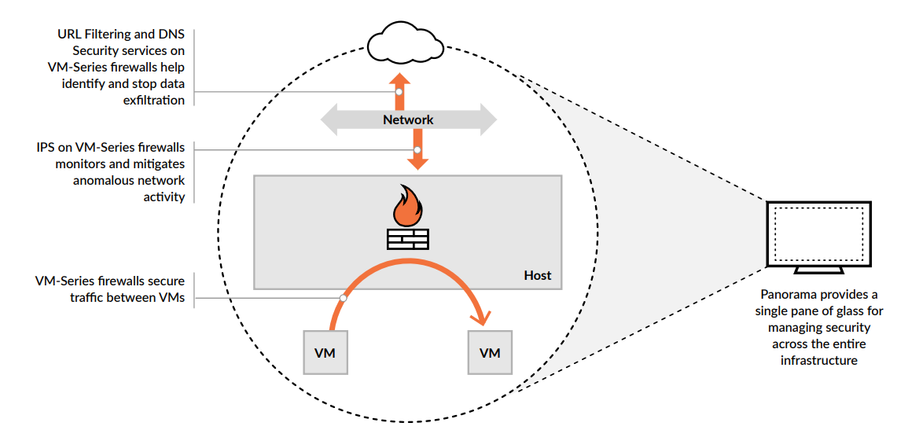
Benefits of Palo Alto Networks in NSX Environments*
The integration of Palo Alto Networks with VMware NSX offers a series of critical business benefits to organizations that depend upon virtualized and hybrid cloud environments to help them stay innovative and competitive.
- Consistent Security for Ongoing Compliance. The VM-Series allows network security teams to manage network security and threat prevention policies for their NSX environments in the same way as they manage their physical and cloud environments. Plus, Panorama provides a centralized management console for the organization’s entire network security posture, spanning on-premises infrastructure, virtualized environments, and public clouds. Panorama simplifies the creation of traffic steering rules within NSX Manager and ensures security configurations are in sync with NSX Manager for consistent security posture.
- Automated Firewall Deployment. VM-Series firewalls integrate seamlessly into VMware NSX for simple, repeatable, and automated firewall deployment with the click of a button. Administrators benefit from a single pane of glass through which to manage security and policies, eliminating the need to jump between interfaces.
- Dynamic Security Policies. As virtualized applications are created, dynamic security policies based on application, content, and user are placed in security groups in NSX Manager as well as recognized by Panorama and the VM-Series. Security groups become the basis of security policies deployed to each VM-Series instance.
- Extended Application Support. The VM-Series provides application visibility across all ports, providing relevant information about the virtualized environment to help security managers make rapid, informed policy decisions. Palo Alto Networks supports more than 3,000 applications, extending the native application support of NSX.
- Compliance. Many regulatory standards, such as PCI DSS, require both segmentation and IPS to secure cardholder information from the rest of the environment. Built-in IPS capabilities of the VM-Series allow network managers to meet these requirements without additional components.
- Multiple Policy Sets. The VM-Series on NSX can be configured to support dedicated security policy sets per cluster. A separate service profile gets assigned to each tenant, leading to duplicate IP address support, isolation of network traffic, and separate security policy and logs per tenant. Secure multitenancy can be implemented across shared and dedicated virtual infrastructure.
*Information reprinted from a Palo Alto Networks whitepaper about VM-Series on NSX.
There are many pieces to the VM-Series network security puzzle that can be seamlessly integrated with VMware NSX to deliver tangible business value in the form of consistent security, dynamic security policies, automated deployment, and more.
More info on VM-Series on NSX:
Thanks for taking time to read my blog.
If you enjoyed this, please hit the Like (thumb up) button, don't forget to subscribe to the LIVEcommunity Blog area.
As always, we welcome all comments and feedback in the comments section below.
Stay Secure,
Joe Delio
End of line





