- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Detecting a specific Linux binary(ELF) file using a custom signature
- LIVEcommunity
- Discussions
- Custom Signatures
- Re: Detecting a specific Linux binary(ELF) file using a custom signature
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Detecting a specific Linux binary(ELF) file using a custom signature
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-17-2016 12:43 PM - last edited on 06-17-2016 12:52 PM by goku123
DISCLAIMER:
As with all custom signatures on this forum, this signature is being provided by the author as a result of enthusiasm for the product and to share ideas with the Palo Alto Networks security community.
It is:
- Not recommended for deployment in a production network of any kind without internal testing.
- Not a solution to any vulnerability.
- Not an official supported Palo Alto Networks signature
This write up is to help the Palo Alto Networks community with detecting a specific linux ELF sample in this example.
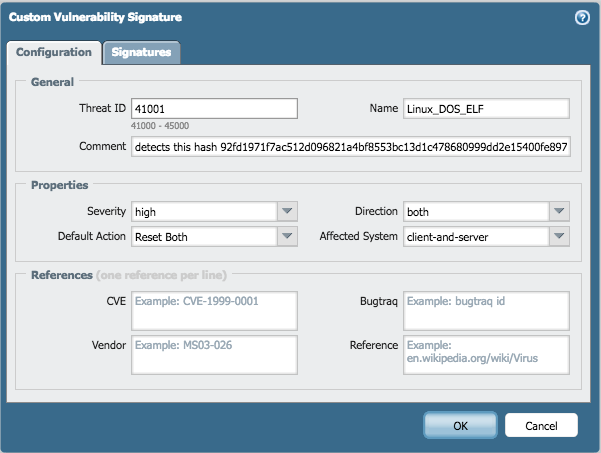
The sample signature was created on PAN OS Version 7.0.x :
Hash256: 92fd1971f7ac512d096821a4bf8553bc13d1c478680999dd2e15400fe8973793
Fill out the appropriate field under the configuration tab
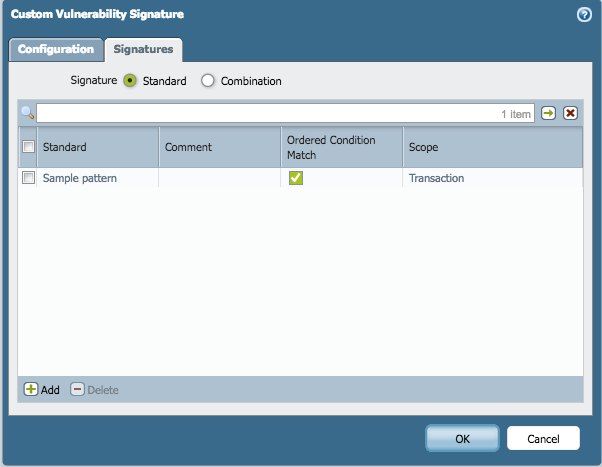
Choose the standard option from the radio button and click on add to create a signature
Since we only have one condition it doesn’t matter if we choose the ‘and’/’or’ condition
Within the ELF file we are looking for a particular pattern on hex values. Make sure to choose the context type as: file-elf-body
Below is a threat log that is being triggered on this signature
Sample xml signature attached to this document.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2016 10:14 PM
What is the significance of the Hash?
Hash256: 92fd1971f7ac512d096821a4bf8553bc13d1c478680999dd2e15400fe8973793
Is there any relationship between the hash and the hex string you are testing for?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 08:55 AM
The hash is mentioned to indicate which sample file was used for this example.
The actual hex pattern in the signature is pulled from this binary's file body.
- 10861 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Wildfire False Positive on Detection of .XLSX extension in General Topics
- XSIAM V3.4 upgrade - anyone having issues? in Cortex XSIAM Discussions
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions
- License Forms in General Topics