- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SMTP Signature Help
- LIVEcommunity
- Discussions
- Custom Signatures
- SMTP Signature Help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SMTP Signature Help
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2017 01:34 PM
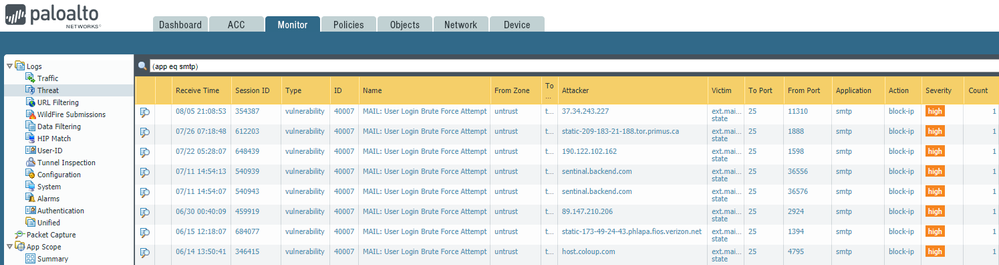
We have been slammed with random Chinese IP addresses attemping to brute-force accounts via SMTP. Amusingly enough, our gateway doesn't even support that feature but the amount of traffic attempting it is consuming all available ports.
I was able to make a signature to catch it when the server responds back with a "502 Unsupported" command but the problem is this alone makes Palo Alto think the attacker is always the server and not the client. So I need to add something to detect the client's traffic first...
The clients are sending an "AUTH LOGIN" command. I can create a rule to detect the AUTH part but the string for "LOGIN" has to be at least 7 characters, which is impossible to meet those requirements. I then tried to create a negate rule but that didn't work and it wouldn't detect the rule at all. So any ideas how to get this to work?
For the time being I just created a DOS resource policy to only allow 5 concurrent source-IP connections. It works but I'd rather have a rule to actually block-IP the attacker for 30 minutes then just let them continue attacking us.
I contacted support and they redirected my case to the threat team. The threat team then sent me here saying they do not offer help on custom signatures and to post any questions in the forums...
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2017 02:07 PM
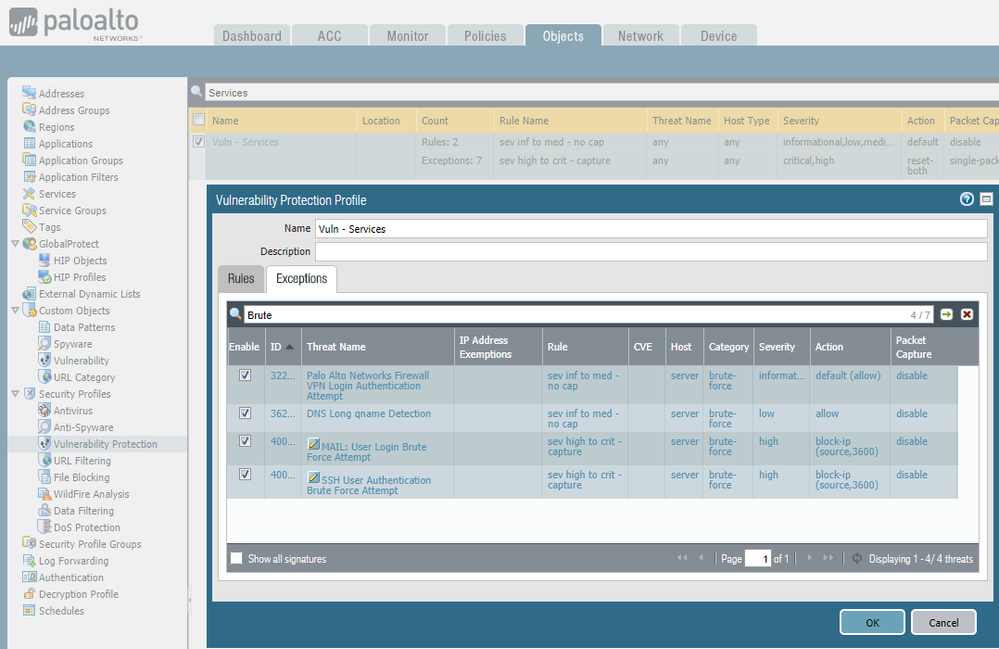
Why are you making a custom signature for this? You can modify the action for the built-in SMTP brute force, assuming it's triggering.
You can make the change in your Vulnerability Protection object, under Exceptions. Add an exception for the SMTP Brute Force and change the action.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2017 02:19 PM
The built-in filter only looks for the 535 response. Our appliance doesn't support the AUTH command so it doesn't respond with a 535, only 502 (Unsupported command).
"If a session has the same source and destination but triggers our child signature, 31709, 10 times in 60 seconds, we call it is a brute force attack.
The child signature, 31709, works on 3 apps, smtp, pop3 and imap.
The trigger condition is found in response code 535 in smtp, "No/bad logon/login failure" pattern in imap and "-ERR" on pop3 PASS command."
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2017 02:46 PM
Can you share a packet capture from one of these events?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-08-2017 06:11 PM
No, but I was able to get the signature to work using the (or) | and adding frivolous text.
Now the issue is when adding a combo signature to include the one I just created, I get an error "Threat 41001 is not known -- cannot be added to this signature." Not sure if this is a bug (Panorama 7.1.11) but even trying to recreate the Wordpress brute-force example document from 2016 just to verify if that works -- I still get the same error. *sigh*
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-08-2017 06:26 PM
Definitely a bug. I was able to create it on the firewall itself without that error coming up, then exported the rule and imported it back into Panorama just fine.
- 6499 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- License Forms in General Topics
- Question about Wildfire signature updates in Palo Alto Active-Passive mode. in Next-Generation Firewall Discussions
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- linux /etc/iproute2/rt_tables filled with 231 pangp.include and 232 pangp.exclude in GlobalProtect Discussions