- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using Custom Indicators with MineMeld
- LIVEcommunity
- Features
- Featured Content
- Featured Articles
- Using Custom Indicators with MineMeld
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 11-23-2018 11:51 AM - edited on 12-14-2021 06:04 AM by jforsythe
Note: Palo Alto Networks made an end-of-life announcement about the MineMeld™ application in AutoFocus™ on August 1, 2021. Please read this article to learn about our recommended migration options.
Introduction
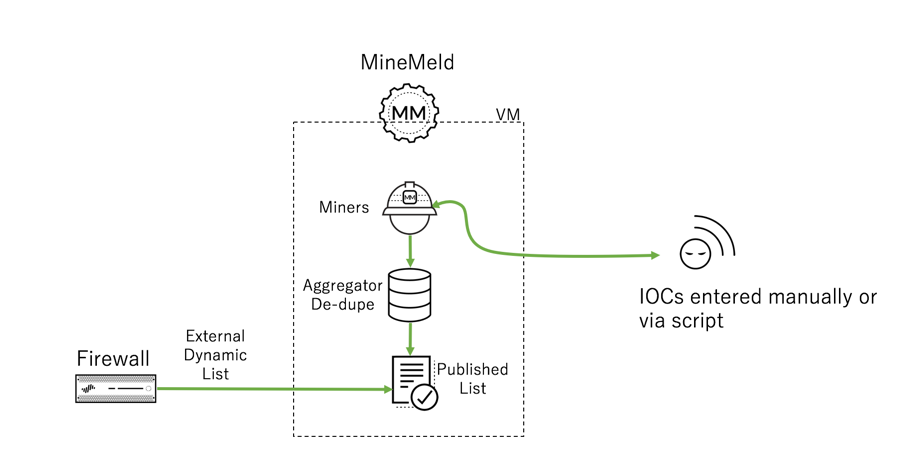
This document provides an example of how to configure a custom miner in MineMeld in order to track custom IoCs. The miner can be configured to track IP addresses, domains, or URLs. The indicators can adapt to the Palo Alto Networks firewall for use within various policies.
Use Case Diagram
Configuration
MineMeld
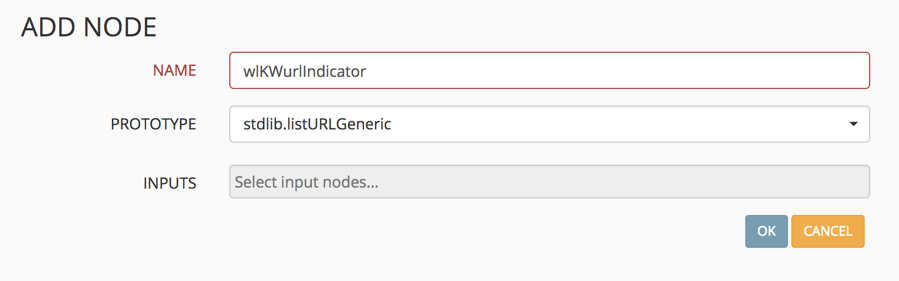
The first step is to create a new miner using the stdlibListURLGeneric protoype.
Go to the CONFIG area.
Click on the “eye” icon in the lower left to change to expert mode. Once in expert mode, a plus icon will appear on the right, allowing you to add a MineMeld node.
Select the plus sign and create a name for the new node. Prepend the name with the letters "wl" (for whitelist – although, the list can be used for positive or negative security purposes). From the PROTOTYPE drop-down, select stdlibListURLGeneric. In this example, I will show you how to create a URL miner to keep track of custom URL-based IoCs.
Select OK to save the new miner node.
You should see the miner in the list.
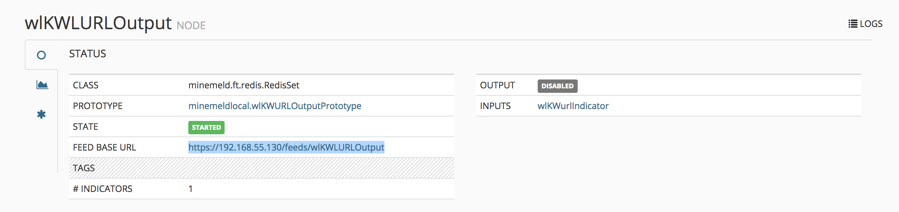
Next, create the Output node. This node will use the miner you just created and publish it to MineMeld’s internal web server, so the firewall can read the list and use it in various policies.
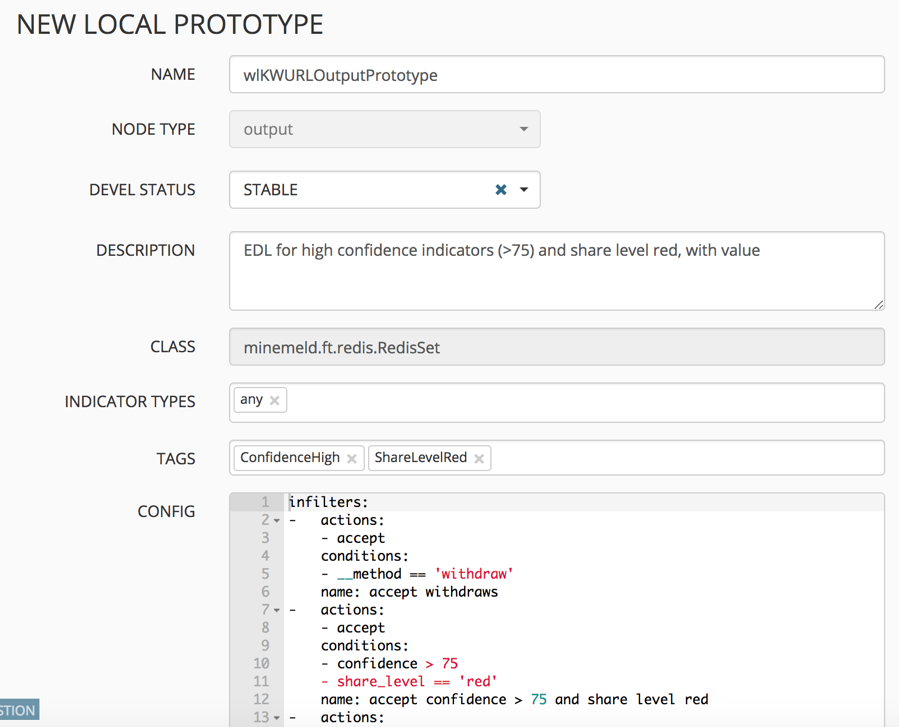
From the CONFIG area, select the icon to see the prototypes. In the search field, look for “OUTPUT.” Find one similar to what you want your output to look like. In this example, I used stdlib.HCREDWithValue. Select the prototype and click “New” to create a new output based on the one selected.
Give it a name, and you may also edit the CONFIG portion.
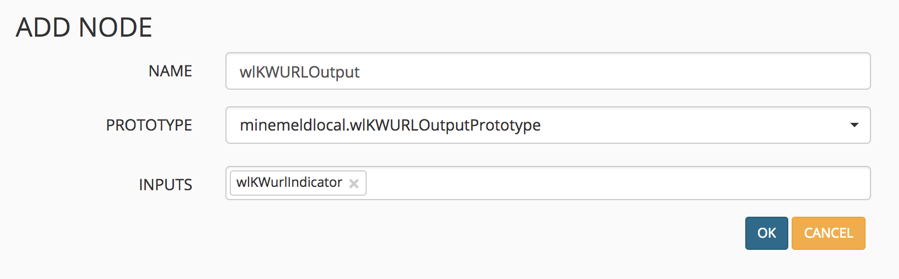
Go back to CONFIG, enter expert mode, and click the plus icon to create a new output node based on the prototype you just created. Give it a name and select the output prototype in the dropdown. For the input, select the custom miner node previously created.
Select OK to save.
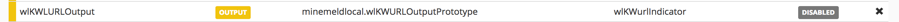
You should see both of the custom nodes created.
When you're ready, select COMMIT in the upper left-hand corner to save the nodes and put them to work. Wait for the relevant services to be stopped and restarted before continuing. Watch the upper right-hand corner for status messages.
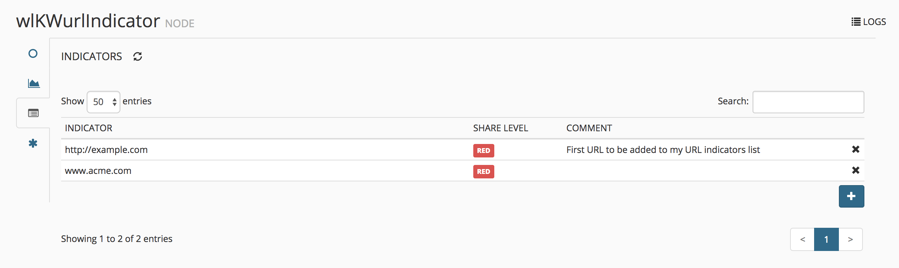
To use the list, go to nodes and select +ADD INDICATOR in the upper right-hand corner.
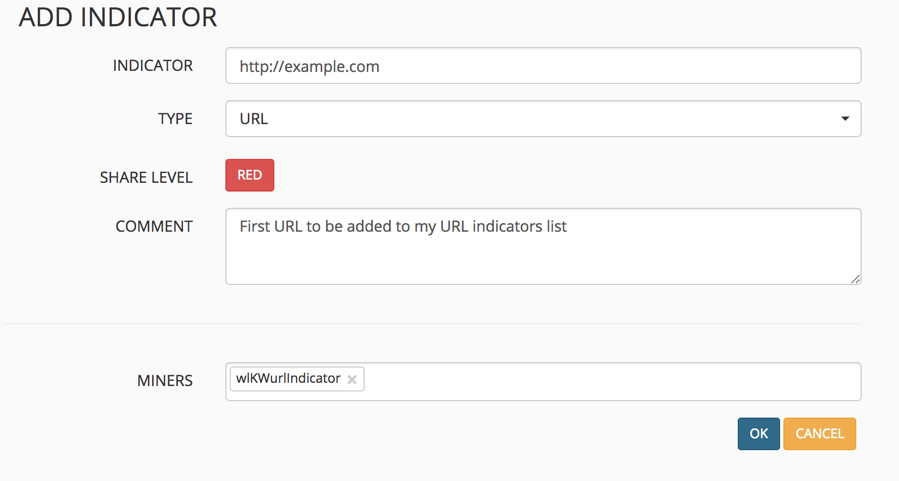
Fill in the fields and click OK. In my case, I am adding the URL indicator, http://example.com. You can change the SHARE LEVEL by clicking the level until the one you want appears. Adding a comment is a helpful reminder as to why the indicator was added.
Click the OUTPUT node you created and notice the FEED BASE URL link. You can open the link to see the published list that the firewall will read.
To manage your custom IoCs, select Nodes and the URL miner created. Click on the INDICATOR icon to see the list. Here, you can delete entries and change the SHARE LEVEL or COMMENTS.
The list is now ready to be consumed by the firewall.
Firewall
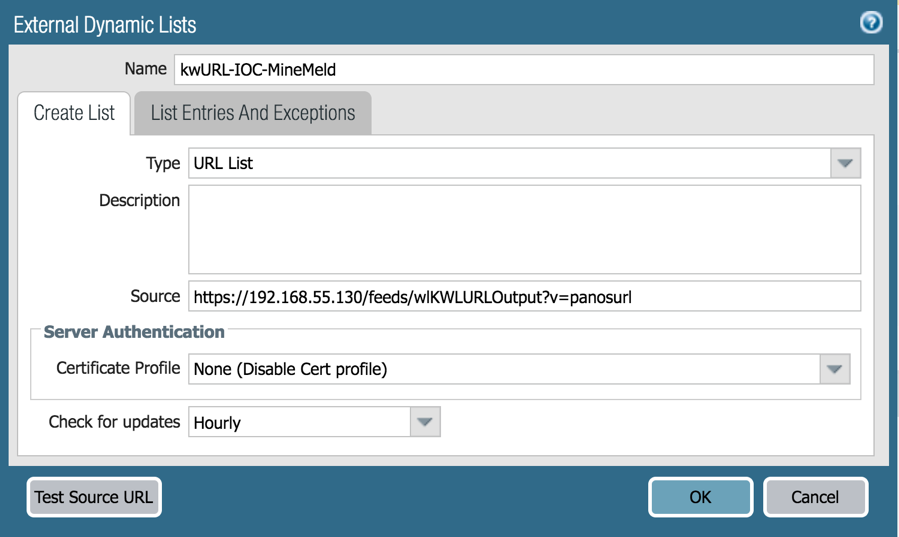
To use the list within your Palo Alto Networks firewall, go to Objects > External Dynamic Lists and select the Add button in the lower left-hand portion of the screen.
For Type, select the appropriate type for the node type created in MineMeld (URL List in this case). Copy the FEED BASE URL from MineMeld and paste it into Source. To test it, click the Test Source URL button.
Notice the additional string “?v=panosurl” at the end of the MineMeld URL. This is a MineMeld option parameter that causes MineMeld to deliver the list in a format that is understandable to the Palo Alto Networks firewall. For example, it will strip out HTTP:// and HTTPS:// for each entry since this type of prepended data is not allowed by the firewall.
See a full list of MineMeld parameters here: https://live.paloaltonetworks.com/t5/MineMeld-Articles/Parameters-for-the-output-feeds/ta-p/146170
Click OK to save.
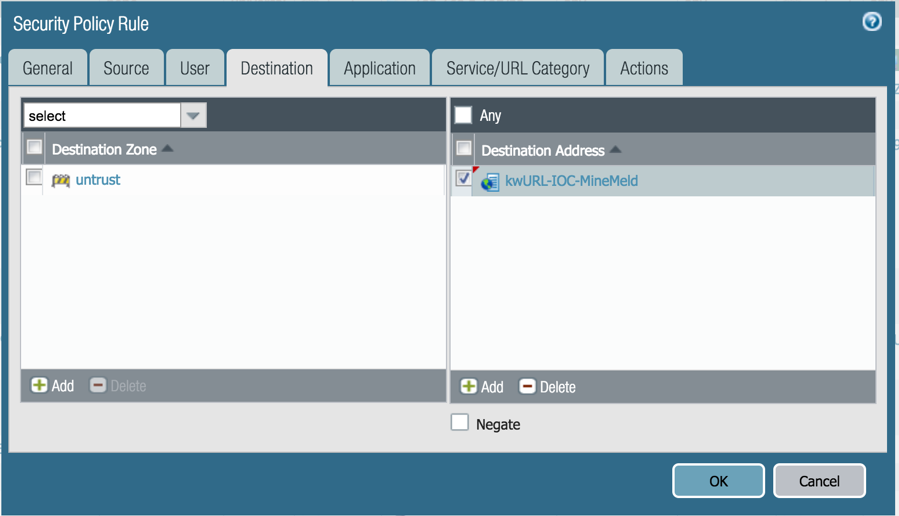
The final step is to use the EDL within a policy. In this example, we can create a Security Policy to block traffic desinated to any site within the list. Go to Policies > Security and add a new rule (or modify an existing rule) where you want the policy to take effect.
In the Destination tab, under Destination Address, click Add and select the EDL you just created. Commit the config to complete the addition.
Other Use Cases
There are other areas within the Palo Alto Networks firewall where External Dynamic Lists may be used.
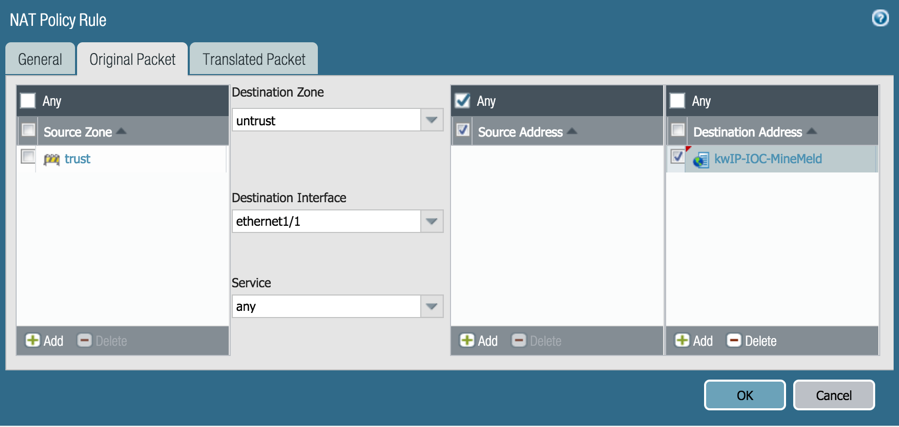
NAT Policies
An EDL may be utilized within NAT policies in either Source or Destination Addresses.
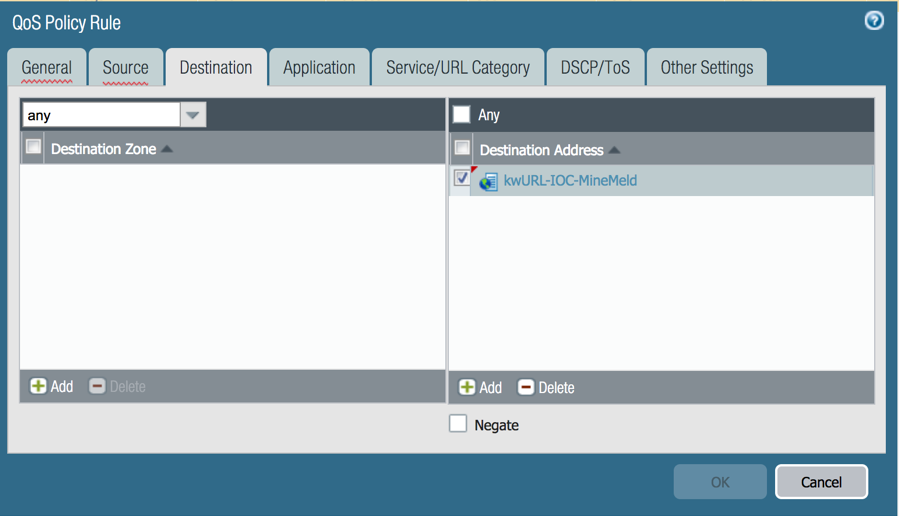
QoS Policies
Use an EDL as a Source or Destination Address within a QoS policy.
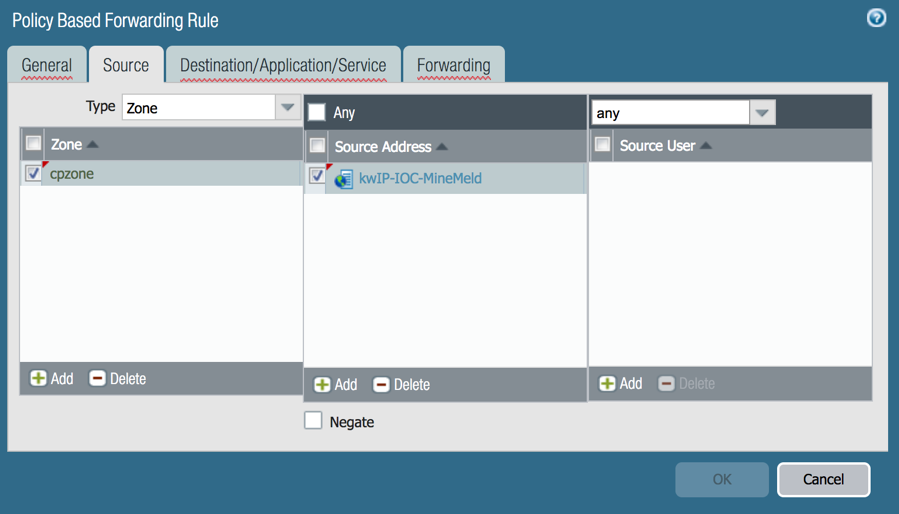
Policy Based Forwarding Rules
Use an EDL as a Source or Destination Address within a Policy Based Forwarding Rule.
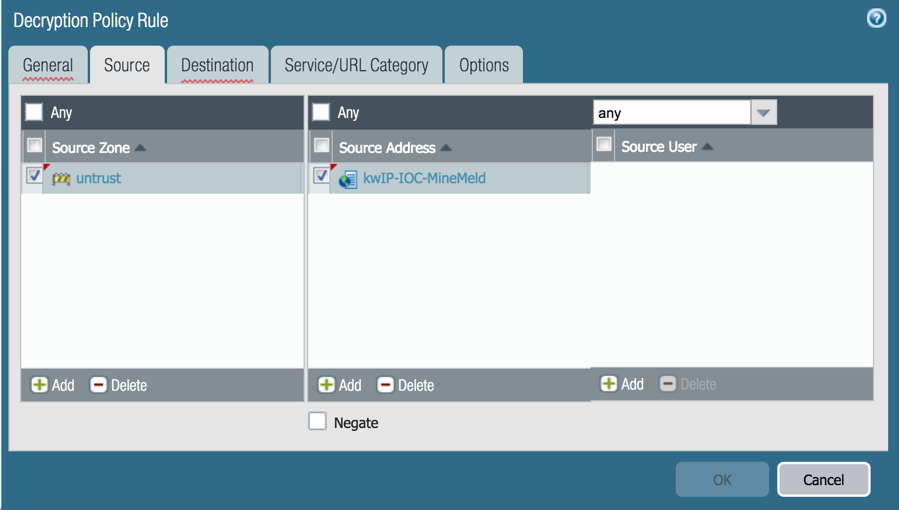
Decryption Policies
Use an EDL as a Source or Destination Address within a Decryption Policy.
Other Policies
Other policies in which an EDL may be used as a Source or Destination (or both) Address:
- Tunnel Inspection
- Application Override
- Authentication
- DoS Protection
Summary
Using MineMeld is a powerful and easy way to maintain your own threat feeds based on IP, URL, and Domain. Using these feeds in your security policy is as easy as pointing the firewall to the published list and referring to the list in one or more policies. There are many use cases for EDLs in both positive and negative enforcement scenarios. See the Live link below for additional ideas on incorporating EDLs with MineMeld into your enterprise security operations.
To learn more about the free MineMeld tool:
https://live.paloaltonetworks.com/t5/MineMeld/ct-p/MineMeld
To learn more about External Dynamic Lists:
If I can use "wl" for the whitelist, is there also an option for a custom blacklist? If I can add URLs or IPs to a custom whitelist, I'd also like the ability to have a custom blacklist as well. Is this possible, like using "bl" instead of "wl"?
- 13252 Views
- 1 comments
- 2 Likes