- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
admin auth failed
- LIVEcommunity
- Discussions
- General Topics
- admin auth failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
admin auth failed
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2010 12:18 AM
Hi Support team,
I tried to authenticate admin with RADIUS, but failed.
The following message appeared in System logs:
- User 'komure' failed authentication. Reason: User is not in allowlist
What does it mean?
device : PA-500
PANOS : 3.1.0
Regards,
Tomoyuki Komure
- Labels:
-
Management
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2010 08:37 AM
I add the same error but with ldap and ssl, and i switch the authentication profile (that i add LDAP) and switch to authentication none. I add to include the group where the users belongs to. In radius you can check the user group that the user belongs.
And worked for me.
Thks.
Helder Teixeira
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2010 09:37 AM
last update i´ve got some users working with; (DOMAIN\username) and others with (DOMAIN\\username) give it and try.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2010 08:12 AM
If you are using RADIUS for authentication, it's going to be two parts. First, you must allow the RADIUS authentication. I would pick a global group like "Authenticated Users" or "Domain Users" in your RADIUS policy.
Then you have to allow the user in either the Administrators list under the Device tab, or the Authentication Profile you are using for your SSL VPN.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2010 09:15 AM
Could some one please post a working example of administrator authentication via LDAP?
I have many non-Palo devices working like a treat but I can't seem to get the Palo to work!
I can't even find anything in the log and doing a debug ldap-server stats shows the server as not running!
If there a better way to test? Some log that may indicate as to why it is not making a connection e.g. invalid bind DN etc?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2010 01:14 PM
I believe you can only use RADUIS if you want to authenticate an administrative user to the PAN Device. I see two options when configuring a new administrative user, Local DB and RADIUS.
You can use the PAN Agent to authenticate users using LDAP if you want to setup security policies with source users.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2010 03:46 PM
Starting in version 3.1.x, you can define authentication profile which uses local DB, Radius, or LDAP. The administrators can be authenticated to the profile of your choosing and admin auth can use local DB, Radius, or LDAP.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2010 07:03 AM
Thank you for the write-up and sharing with all of us!!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-30-2010 10:02 AM
Thank you. This helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2011 08:13 AM
I'm still struggling trying to authenticate a group of users as Palo Alto admins. These users are not in any one particular group. I get the error 'Authentication profile not found for the user' . I just want to create a list of ids for Palo Alto to query AD for using LDAP. Is the problem that PA will only search for groups or at a particular search base DN ? It cant search nested groups.
I also am lost on how to turn debugging on just for this process. It would be good to see what the PA queries for.
A 'test authentication' applet in the GUI might be a good thing to add.
Any help would be appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2011 08:35 AM
You can define an Authentication Profile, use LDAP for the auth method, and type in 'all' for the allow user. The 'all' means any users in your AD/LDAP will valid username/password will be permit as an admin. I use this to for testing only. NOTE: 'all' is really all without the quotes.
Once that works, you then permit specific users or groups to be admins by replacing the 'all' with actual AD usernames/groups.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2011 10:54 AM
That's correct - for LDAP, you also need to add the user here:
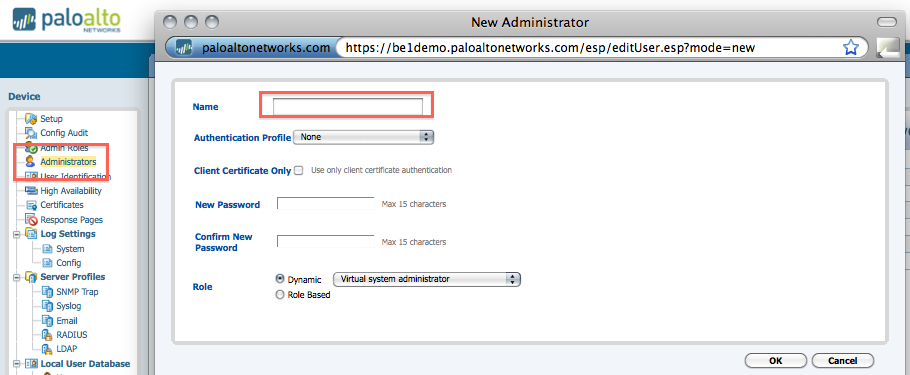
This is why RADIUS can be more scaleable if you have a high number of admins:
https://live.paloaltonetworks.com/docs/DOC-1701
Thanks
James
- 19378 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Assistance with LDAP Authentication in General Topics
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Issues with SSH and Telnet access only on the passive firewall. GUI access is working fine. in Next-Generation Firewall Discussions
- Authentication Error occurring creating new Super User in Next-Generation Firewall Discussions



