- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Block access to sites with invalid SSL cert
- LIVEcommunity
- Discussions
- General Topics
- Block access to sites with invalid SSL cert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Block access to sites with invalid SSL cert
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2012 11:45 PM
Hi,
I could not find a way to block access to sites with invalid (self signed, expired) ssl certifcates. Any Ideas ?
PAN OS 4.1.3.
rgds Roland
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2012 12:26 AM
In Device -> Setup -> Session you can alter some of the SSL settings such as:
CRL Enable
Receive Timeout
OSCP Enable
Receive Timeout
Block Unknown Certificate
Block Timeout Certificate
Certificate Status Timeout
When you setup the SSL-inspection the certificate used can have various options such as:
Forward Trust
This certificate is presented to clients during decryption when the server to which they are connecting is signed by a CA in the firewall’s trusted CA list. If a self-signed certificate is used for forward proxy decryption, you must click the certificate name in the Certificates page and select the Forward Trust Certificate check box.
Forward Untrust
This certificate is presented to clients during decryption when the server to which they are connecting is signed by a CA that is not in the firewall’s trusted CA list.
Trusted Root CA
The certificate is marked as a trusted CA for forward decryption purposes.
When the firewall decrypts traffic, it checks the upstream certificate to see if it is issued by a trusted CA. If not, it uses a special untrusted CA certificate to sign the decryption certificate. In this case, the user sees the usual certificate error page when accessing the firewall and must dismiss the warning to log in.
The firewall has a large list of existing trusted CAs. The trusted root CA certificate is for additional CAs that are trusted for your enterprise but are not part of the pre-installed trusted list.
SSL Exclude
This certificate excludes connections if they are encountered during SSL forward proxy decryption.
Certificate for Secure Web GUI
This certificate authenticates users for access to the firewall web interface. If this check box is selected for a certificate, the firewall will use this certificate for all future web-based management sessions following the next commit operation.
So you can enable "Block Unknown Certificate" and then use a specific CA as "Forward Untrust" which is blacklisted in your clients browsers (like one CA for "Forward trusted" which is added to the list of trusted issuers in the client browser and another CA for "Forward untrusted" and have this CA blacklisted at clientside). Question here is how to block the client from just override the warning that the cert is issued by un untrusted (or blacklisted) CA?
I dont know if just enabling "Forward Trusted" is enough to accomplish this (if im not mistaken this means that untrusted SSLs are just forwarded without inspection to the client which would be really bad).
What I have failed to find out is where to see a list of which Trusted CA's the PAN unit will approve? And how to manually remove one (or many) CA's from this list (this way one would not have to wait for PA to release an update next time Verisign, Globalsign or some other CA gets hacked)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2012 12:52 AM
Hi,
thanks for your input. I already tried what you suggested but it did not work. I don't want to touch the clients certificate store. I am looking for a solution to block access on the firewall level.
I guess I need to file a feature request.
rgds Roland
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2012 01:52 AM
Ok, it's working now at least with IE8. After adding the untrust-cert from the PA firewall to the "Untrusted Publishers" cert store on the client, connections to sites with invalid ssl certs are blocked.
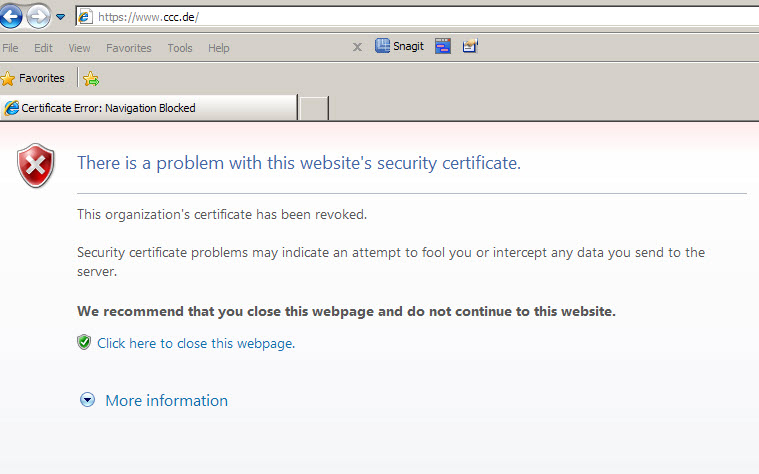
The same is true for Chrome (V 17) which shares the cert store from IE. I was unable to get the same working with FF (V 10).
Again it would be better to have this functionality on a Firewall level and not on an endpoint client browser level.
- 4229 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in General Topics
- On-Boarding of Cisco SDWAN to Prisma in Prisma Access Discussions
- Website Filtering Dillema in General Topics
- Administrator Login using Azure Groups through Cloud Identity Engine in General Topics
- Prisma SD-WAN sites cannot connect to Prisma Access - Error "Inner ip pool usage reach limitation and need update" in Strata Cloud Manager



