- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Block websites when using VPN
- LIVEcommunity
- Discussions
- General Topics
- Re: Block websites when using VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Block websites when using VPN
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2019 11:02 PM
Some users started to use SoftEther VPN client on our company which allows them to bypass URL Filtering policy. How can we allow them to use VPN client but still allow or block access to certain websites. We already implemented SSL decryption rule but it is not working when they are using SoftEther VPN.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 02:08 AM
Hi @nredaj ,
Is decryption working ?
How is the traffic identified by the firewall ?
Cheers,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 02:56 AM
Hi @kiwi ,
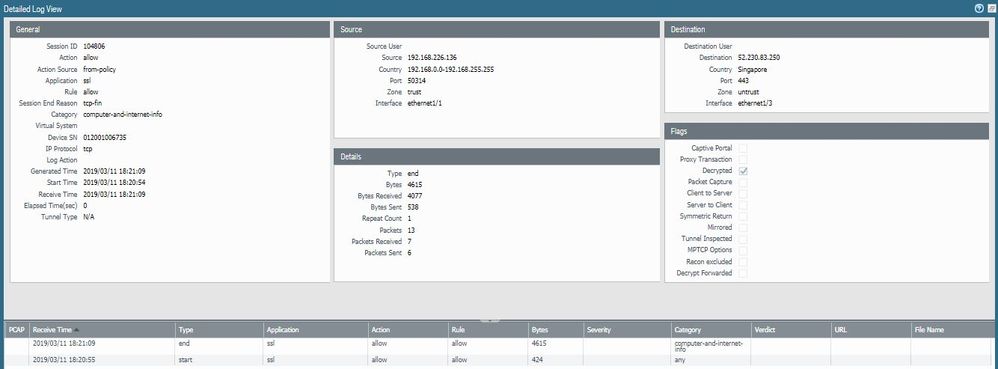
Decyption is working. Based on monitoring logs, when using VPN client, all traffic are identied as:
Application: SSL
IP Protocol: TCP
Port: 443
Category: computer-and-internet-info
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 03:02 AM - edited 03-11-2019 03:11 AM
Hi @nredaj ,
How is decryption working ?
If the application is identified as SSL then decryption isn't working.
Note that on some scenarios decryption is impossible ... for example when unsupported protocols or ciphers are used or with certificate pinning for example.
Cheers,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 03:28 AM - edited 03-11-2019 03:29 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 03:49 AM
Hi @nredaj ,
You might be hitting this which could explain why a decrypted session is still showing up as SSL :
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cle8CAC
Have you checked with support already ?
Cheers !
-Kiwi,
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 09:16 AM
Hmm, I think the ssl decryption here will not be as helpful as usual. you will only decrypt the outer wrapper (the actual tunnel) any ssl packets running through the tunnel will not be decrypted as negotiation for these will have taken place end to end via the tunnel, not the palo.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2019 11:23 AM
I would agree with @Mick_Ball in this case. Decrypting this traffic isn't going to give you much information and won't allow you to actually perform URL FIltering; this is actually the exact reason VPNs are recommended on untrusted networks, the network operator can't decrypt enough of the traffic to actually see anything useful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-12-2019 12:56 AM
I understand that this could be out of Palo Alto's FW scope.
This is a bit frustrating. Configuring static route in client side (windows OS) could have solve this issue but the website they're accessing is going thru CDN which cause IP address to change from time to time. Probable solution may be work out with SoftEther VPN configuration.
Thank you guys for all your inputs.
- 8720 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Geo blocking after GP login in GlobalProtect Discussions
- Custom BIOC Rule won't apply to Prevention Profile in Cortex XDR Discussions
- Create a IOC without incident in Cortex XDR Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions