- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Blocking All Internet Traffic from certain PCs
- LIVEcommunity
- Discussions
- General Topics
- Blocking All Internet Traffic from certain PCs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 06:41 AM
I have several older machines (XP) that are used for special purposes that cannot be be upgraded. Even the hardware cannot be upgraded or replaced (running on old dell dimenion desktops). These machines do not need access to the internet but they are on the same domain and need to be able to communicate with other domain machines. I want to make it where these machines cannot access any internet resources to reduce the change of malware/virus type activities. I was thinking that I can setup a rule/URL filter, that would block access and add these machines IP addresses to the list. Is this the best way to achieve this goal?
Thanks
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 03:51 PM
Hello,
Even a DHCP address with a reservation would be OK, as long as these IP's dont change. You wouldnt have to have a new URL policy, just one that blocks traffic from trust -> untrust. While you could get tricky with the config, I would say simple works best.
Hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 06:18 AM
Hello,
Even in vwire mode you are still able to accomplish this. Each side of the vwire should have its own zone, i.e. trust and untrust (these are just names, can be anmed anything as long as it makes sense to you). Lets say the PC's you want to block internet from are on the trust side. Just create 2 policies such as:
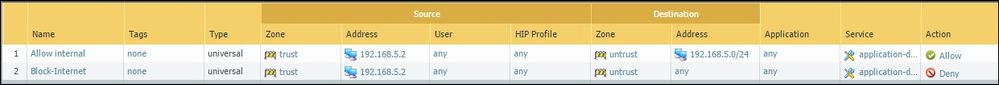
Just like the ASA the PAN reads rules top down left to right. So as long as the rule matches the appropriate action is taken.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 10:03 AM
@jharlow The only native was to do it is via IP (Static or FQDN entry). Or if you've got a list that can be dynamically updated I've explained here how I've deployed a list of dynamically updating machines.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 12:10 PM
I am not sure if I follow you? I have AD connected and use it to filter users for other policies. If you were agreeing with me that a separate policy is the best way to block internet access and add the XP machine via their static IP, then we are on the same page. Guess I wanted to check to see if there was a better way? The URL filtering will allow me to filter by category. Right now I have a policy created that I set BLOCK on all types but not sure if that is best way on going about this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 03:51 PM
Hello,
Even a DHCP address with a reservation would be OK, as long as these IP's dont change. You wouldnt have to have a new URL policy, just one that blocks traffic from trust -> untrust. While you could get tricky with the config, I would say simple works best.
Hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2017 05:58 PM
Sorry...Your original question/statement didn't define all the potential variables so I was answering all of them...Albeit not very clearly.
You have a set of XP machines which you don't want them to access the Internet. (These will have to have their own unique security rule unless you've got one already built which blocks access to the Internet)
I was answering based upon them potentially being a dynamic IP / IP range.
@OtakarKlier 's suggestion is how I'd go. If you were simpling from from "internal" to "Internet" then I wouldn't even bother with a URL filtering policy. A simple L3 security policy with a "deny" action would be the easiest way to go.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 06:03 AM
Gotcha! I dont know if I can use that method as of yet. Our PA is in transparent mode, as the only policies we have in place is for URL filtering and AV/Malware scanning. We have an older Cisco ASA that handles NAT. The goal is to transition over to the PA, but getting there from where we are now ...
Any case, your response helps me understand what I can do. Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 06:18 AM
Hello,
Even in vwire mode you are still able to accomplish this. Each side of the vwire should have its own zone, i.e. trust and untrust (these are just names, can be anmed anything as long as it makes sense to you). Lets say the PC's you want to block internet from are on the trust side. Just create 2 policies such as:

Just like the ASA the PAN reads rules top down left to right. So as long as the rule matches the appropriate action is taken.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 08:18 AM
@OtakarKlierCan we be friends? 🙂 Wow! That was easy enough and does exactly what I needed! Thanks! Curious, is that basically what I need to do to make this a layer 3 device versus vwire, minus NAT rules? Or a different way to ask, is all that is needed is to create the same NAT rules from the ASA on the PA and this is a L3 device or is there more to that?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 08:27 AM
Just glad I could help. I know how new technologies and devices can be a bit frustrating at times. I also came from an ASA world and can say that I wont go back :).
As for converting from vwire to a L3 device, yes there is more that needs to be accomplished. The way I have done it in the past is by having the two devices in parallel and manually entering the settings, NAT's and policies, from the ASA to the PAN. I do it this way so I can weed out the NAT's/Policies that are no longer needed. Also this helps me learn the new platform, in this case the PAN.
There is a migration tool available that many on this forum have used successfully (I have not). I would say the decision is yours based on not only NAT's/Policies but also objects and other configs you want to migrate over. I would say start a new post if you are looking for assistance with the Migration tool and someone who has used it will help you out.
Migration tool: https://live.paloaltonetworks.com/t5/Migration-Tool-Articles/Download-the-Migration-Tool/ta-p/56582
User guide: https://live.paloaltonetworks.com/t5/Migration-Tool-Articles/Migration-Tool-3-Info-and-Guide/ta-p/55...
Best practices: https://live.paloaltonetworks.com/t5/Migration-Tool-Articles/Migration-Tool-Best-Practices/ta-p/5665...
BTW welcome to the PAN world :).
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 08:57 AM
Yeah, I would do it manually as well. The issue I have and I am assuming this; is making the change from vwire to L3 would require resetting the device (lossing all of my custom settings I have now; aka URL filtering rules.) Is that correct?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 09:05 AM
Nope, you wont have to. all that stays...The changes come in with the Zones, Virtual Routers, Interface configurations etc.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2017 02:31 PM
Any chance, this process is documented somewhere ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-17-2017 08:28 AM
Hello,
Oviously these are just guides and each environment is different so caution is recommended.
There is not just one answer for this however.
Regards,
- 2 accepted solutions
- 9294 Views
- 13 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Pre-processing script is not be able to get result from SearchIncidentsV2 command in General Topics
- Geo blocking after GP login in GlobalProtect Discussions
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Stealth Rule Question in Next-Generation Firewall Discussions



