- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Blocking WORD docs which contain macros
- LIVEcommunity
- Discussions
- General Topics
- Blocking WORD docs which contain macros
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Blocking WORD docs which contain macros
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2015 09:28 AM
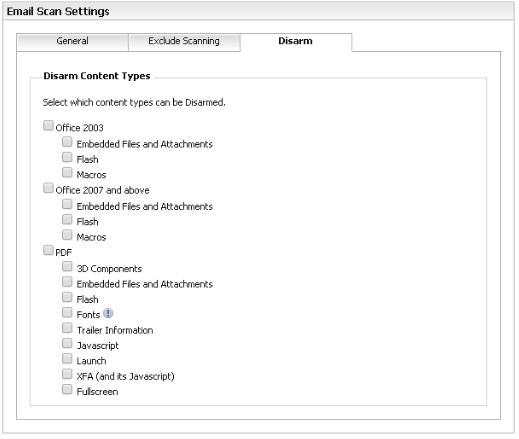
In the course of a regular day, it is not uncommon to receive regular legit word documents from people via email. However, increasingly we are getting documents pretending to be resumes, and the .doc file contains macros. Our version of Word 2013 treats these as protected documents and the macros do not auto open like the malicious user intended. However, the content of the word document tries to trick our end user into clicking the "allow content" button. Even if they do click, our firewall is blocking the attempted EXE download. However, should the next round of word documents get more clever and change the download into something without an extension (possibly renaming during the download?) then I'd like to investigate the option of preventing Word documents with Macros from coming in through the firewall.
Is that possible using a data filter?
Corbett.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2015 12:24 AM
According to PA executable files are not recognised only by extension but by file content so changing extension won't help the attacker. However i agree that blocking word docs with macros from internet could be a useful feature. I don't think there is such feature available yet. But I guess a DLP filter which triggers on typical macro functions and/or calls could work. Or some custom IPS signature maybe.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2015 08:08 AM
The macros inside these malicious word docs are password protected, so I'd have to look for a string blocking all macros, of which I don't know how to do. There is text inside each of these word docs that tries to make the user click the to disable extended security, so maybe I can scan for those words instead of looking for macros.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2016 06:48 AM
This is kind of an older question from 2011 but the whole macro thing especially regarding CryptoLocker spreading rapidly over the EMEA region is highly relevant. Any updates if such a macro blocking/dection (aka. finding active content in MIMEs) feature will be vailable in PAN-OS 8 - Such an extension to the AV/fileblocking database would be very nice. Plenty of e-mail gateways are doing this for the e-mail vector, also from a web vector perspective controlling files entering the company in a more granular would help a lot.
...something like that for the http traffic side:
Thanks
- 3857 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Geo blocking after GP login in GlobalProtect Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Stealth Rule Question in Next-Generation Firewall Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions
- Notepad++ block specific hash version in Cortex XDR Discussions