- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
failover between sites
- LIVEcommunity
- Discussions
- General Topics
- failover between sites
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
failover between sites
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2022 06:35 AM
Hi,
Hi ,
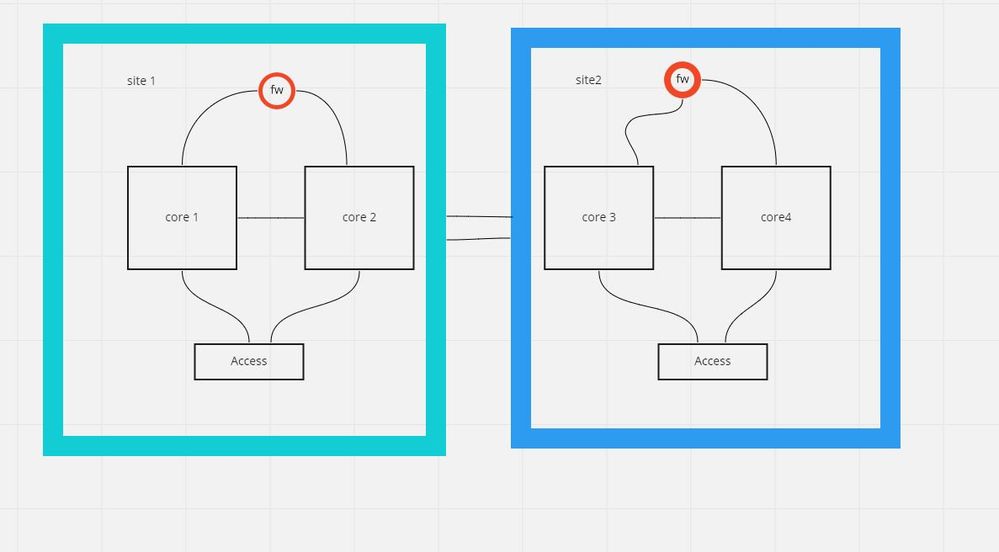
I have two sites , between sites layer 3 connection is there .single firewall deployed in each site .Now I want to make active standby with these firewalls .
How can I do that , does it work without any problem ?
What need to be dome to make it work
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2022 08:06 AM
Hello,
Is this for internal users going out or outside services that are hosted, ie websites?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2022 10:02 AM
Hi,
Internet access for LAN users and hosted services
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2022 12:08 PM
Hello,
Using a dynamic routing protocol such as OSPF should accomplish what you are looking for. It will distribute the routes based on metrics. Make the metrics between the datacenters say 10000, that way the default (internet outbound) routes are always going to point to their respective data center firewalls. And in case of a failure of a firewall, the traffic will be routed via the wan link to the other firewall.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2022 11:44 PM
Hey @simsim ,
- As described in this document https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/ha-concepts/ha-links-and... Control Link (HA1) and Data Link (HA2) can use layer3 and if you route the two networks between sites, the two firewall will should be able to establish HA cluster.
There is one problem: - PAN FWs in Active/Passive cluster are sharing interface addresses, which means you need the networks between FW and core to use the same addressing on both side - you cannot assign different network/addresses on the passive member.
From top of my head, I believe you can achieve what you want, but I wouldn't prefer this approach, lots of complications and confusing setup and it is possible to have some issues with HA traffic.
I would also suggest you to consider @OtakarKlier proposal and use standalone firewalls with dynamic routing. You still can have "active/passive", by always preferring the routes from FW1 and failover to FW2 only when routes from FW1 are unavailable.
The biggest challenge with this approach is that you have to keep the rules consistence between the two firewalls. I would recommend to use Panorama and manage both firewalls with the same device group. Of course if you don't have panorama at the moment your budged may be a problem.
(believe me configuring same rules manually on separate firewall is complete nightmare - I have inherited two similar firewalls and I haven't managed to fix all the mess of missing rules between the two firewalls)
- 3329 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- Backup Peer HA1 IP Address ? in Next-Generation Firewall Discussions
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- User ID mapping works on DC but not/intermittent on branches for Intune internal users. in GlobalProtect Discussions
- Question on PA-440 Failover in General Topics