- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Fragroute Evasion Attack - how to find source process/application?
- LIVEcommunity
- Discussions
- General Topics
- Fragroute Evasion Attack - how to find source process/application?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Fragroute Evasion Attack - how to find source process/application?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-17-2014 12:28 PM
Hello
Last days one of my computer started generating strange traffic that is blocked by Thread Prevention (ID35111)
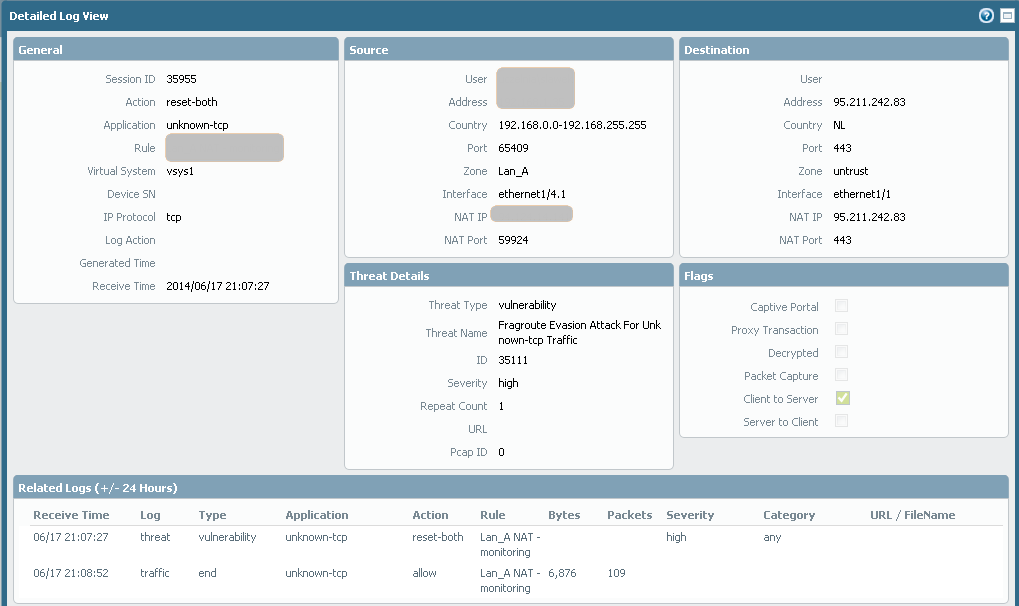
I have access to this computer, but how to find and remove this program that is genrating such traffic?
Regards
Slawek
- Labels:
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2014 01:40 PM
Slawek,
You might start by looking at the netstat output for the workstation with the source port 65409
This article will help for a Windows system - See what process is using a TCP port in Windows Server 2008 - TechRepublic
The SysInternals tools from Microsoft can also help - Windows Sysinternals: Documentation, downloads and additional resources
One issue that may arise is that modern malware tends to hide itself from the built in tools that could be used to identify it.
May your efforts be successful.
James
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2014 12:28 PM
Today I did execption in volnurability profile with pcpap option set.
In Thread log I see:
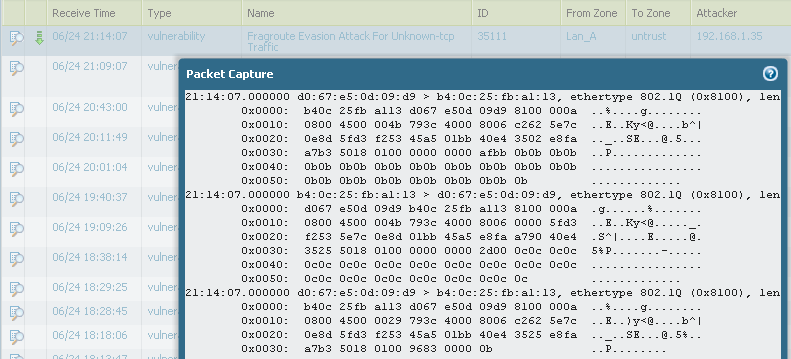
In Monitor>Packe Capture > Captured files there isn't such file.
How to save this information in .pcap format file?
How can I use this information for sending it for further analysis by other vendors?
With regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2014 12:14 AM
Hi slv,
To save the pcap you should use the 'Export' button provided:
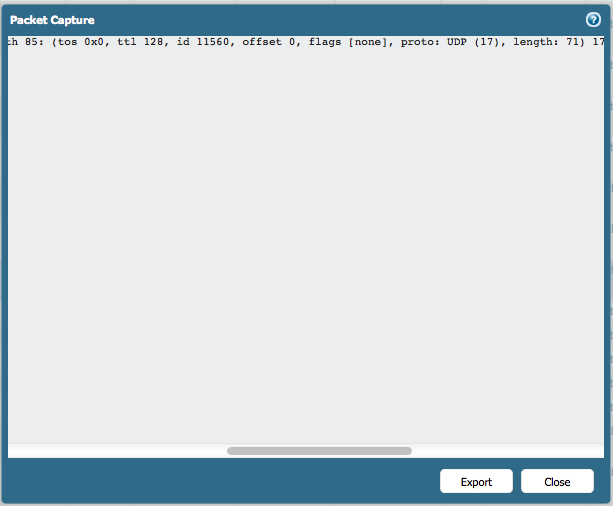
In Monitor>Packet Capture > Captured files you will only find PCAP files which you have grabbed using the filters on that same page or via CLI using the 'debug dataplane packet-diag' command.
Kind regards,
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2014 02:48 AM
Hello Kim
oops I guess I was blind!
Thx
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2014 03:26 AM
FYI
This traffic was generated by AmmyAdmin
Unfortunetelly PAN doesnt detect this traffic as should be. AmmyADmin is well known for PAN OS aplication, but not properly detected on 6.0.2.
Case pending for update.
Slawek
- 9211 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Evasion Technique - 1244315488 in Cortex XDR Discussions
- FTP Evasion Detection (id:30401) in Next-Generation Firewall Discussions
- Does Panorama Forward These Events to External SIEMs via Syslog by Default? in Panorama Discussions
- high priority 'Behavioral Threat' alert for smss.exe (system)? in Cortex XDR Discussions
- Evasion Technique - 3348100960 in Cortex XDR Discussions



