- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
FTP weird behaviour
- LIVEcommunity
- Discussions
- General Topics
- FTP weird behaviour
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
FTP weird behaviour
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 03:20 AM
Hi,
We realised that our PA is doing something strange with FTP app
We have create and above rule (Servidores a INET 1). All our FTP connections involved should match this rule but we see connections which are jumping this rule and mathicng in another one below (Servidores a INET ftp)
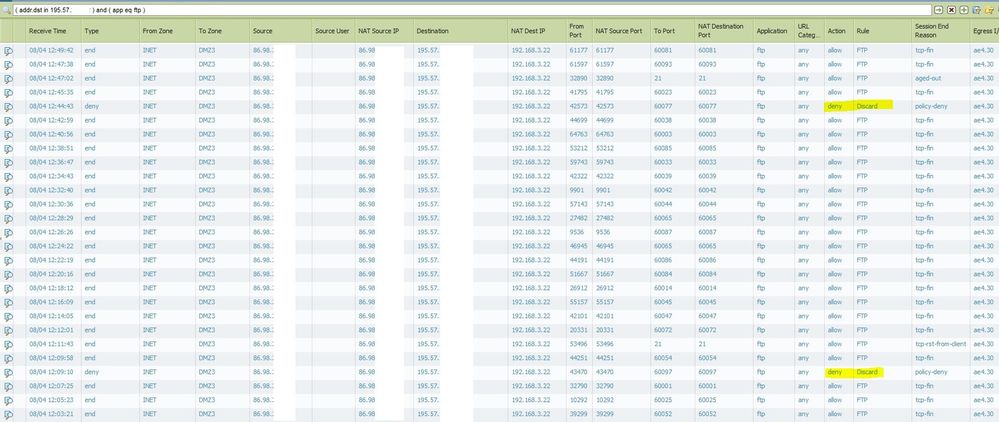
This is the log traffic (source 192.168.53.182) where all FTP connections should match going to INET.
But in another rule below we see FTP matches :S Why do we see matches here not in rule above????
The source/destination/NATs are the same for all connections. Any idea?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 04:13 AM
In the first rule we have allow FTP app, the high ports are dynamic open by FTP connecting. PA should identify this high ports in ftp connection.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 04:22 AM
Correct. It is doing an inspection of the FTP traffic and should allow all dynamic ports agreed between the client and the server for the same session. Could you plz post a "magnifying glass" output for both sessions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 05:16 AM
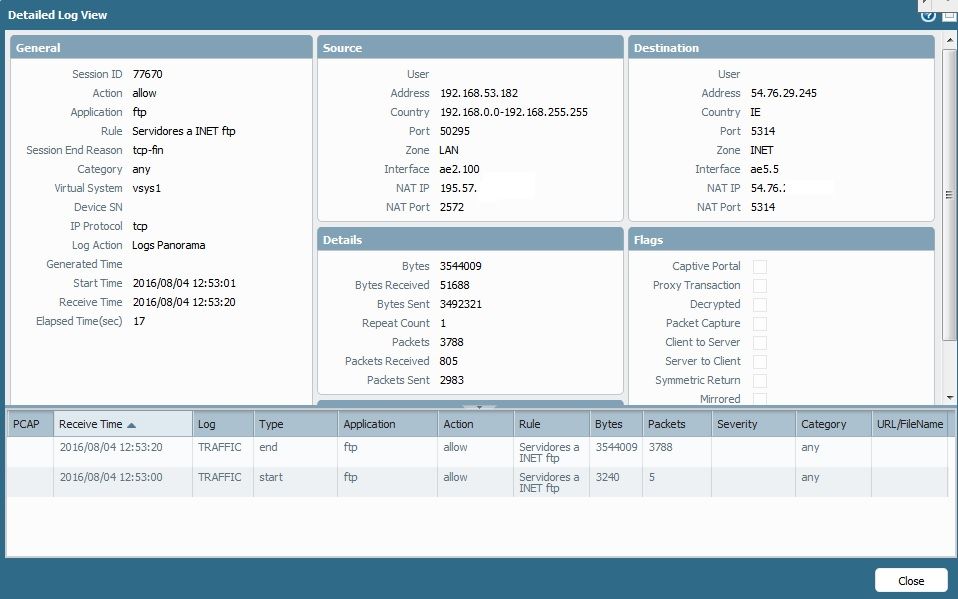
I attach the details connection.
I checked another connections and saw that FW is jumping another rule and appliying the final deny. Its like FTP identify is doing something strange.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 06:16 AM
Hi,
Was it always like that or something is changed and you noticed this behaviour. Is it for all FTP client or just one particular?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 06:24 AM - edited 08-04-2016 06:25 AM
just a thought. is there a way for you to trace one single client-server interaction and lay all connections from that client out so you can see when it hits the right and when it hits the wrong rule ? (specifically so you can see the time information)
there's a lot of dynamic high ports, these are negotiated as part of the initial ftp connection on port 21. when the ports are negotiated, AppID creates a predict session that knows which ports to expect... maybe the initial session is timing out, taking with it the predict session, before the data connection is set up in some of these cases, making the data connection a standalone session (for active ftp there would be 2 or more sessions with 1 being the control link session and 1 being the data link session)
maybe your TCP timeouts are set very agressive or the session is so 'slow' the timers need to be adjusted slightly
> show session info
...
Session timeout
TCP default timeout: 3600 secs
TCP session timeout before SYN-ACK received: 5 secs
TCP session timeout before 3-way handshaking: 10 secs
TCP half-closed session timeout: 120 secs
TCP session timeout in TIME_WAIT: 15 secs
TCP session timeout for unverified RST: 30 secs
UDP default timeout: 30 secs
ICMP default timeout: 6 secs
other IP default timeout: 30 secs
Captive Portal session timeout: 30 secs
Session timeout in discard state:
TCP: 90 secs, UDP: 60 secs, other IP protocols: 60 secs
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 06:42 AM
Hi reaper,
Session paramethers are configured by default. Its weird because its quite randomly. I just opened a PA case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2016 06:52 AM
Hi,
Please let us know the TAC findings/outcome.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2016 08:07 PM
did you get back from TAC on this?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2017 05:45 AM
I am also facing same issue can you share the results
Firewalldog dot com
- 5986 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need help on this XSOAR Weird behavior on preprocessing scripts in General Topics
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- Playbook stuck after upgrade in Cortex XSOAR Discussions
- Strata Cloud Manager UI language and translations in Strata Cloud Manager
- PA-440 won't talk via network in Next-Generation Firewall Discussions