- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Inbound Decryption Advice to overcome Decrypt error
- LIVEcommunity
- Discussions
- General Topics
- Re: Inbound Decryption Advice to overcome Decrypt error
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Inbound Decryption Advice to overcome Decrypt error
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2017 04:50 AM
I am asking for help to get SSL Inbound decryption working. I have read all the posts and tried everything I can think of but I keep getting the decrypt error status so I may have a basic misunderstanding. If someone has an insight into what I am doing wrong after reading the information below I would be grateful to receive it.
The web server is restricted by group policy to a few encryption algorithms that the Palo Alto firewall supports being:
• TLS_RSA_WITH_AES_128_CBC_SHA256
• TLS_RSA_WITH_AES_256_CBC_SHA256
• TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)
• TLS_RSA_WITH_AES_256_GCM_SHA384 (0x009d)
I have tried a certificate issued by “GoDaddy” and also a certificate issued by my internal CA but I get the same result from each. The clients trust both certificate authorities. When the client connects, one packet appears to be decrypted but the rest produce a Decrypt error. A capture shows no errors.
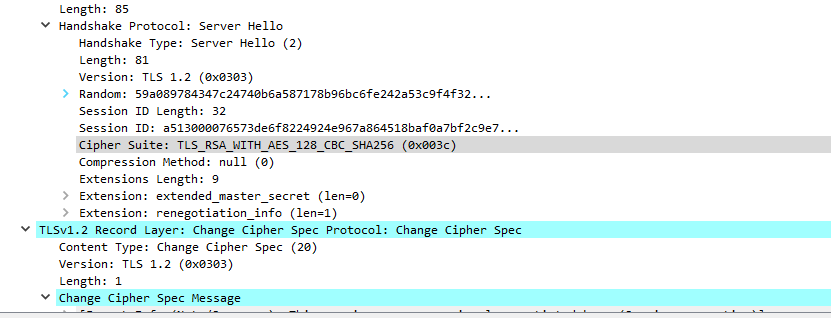
The “Client Hello” appears normal listing its supported encryption algorithms followed by a “Server hello, Change Cipher Spec” which looks like it sets the Encryption algorithm to “TLS_RSA_with_AES_128_CBC_SHA256”. This is followed by a “Change Cipher Spec, Encrypted Handshake Message” which I am unsure what this does. These all appear below.
Client Hello


- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2017 02:49 PM
I kept researching and found a post by Anil Kumar that indicated the issue may be the TLS Extension "Extended Master Secret". If I disable this on the server ad the client, decryption works. Disabling this only on the server seems to be insufficient for decryption to work. The problem now is what to do. Do I downgrade from TLS to SSL or do I forgo decryption. I would be interested in your comment on these options.
Does anyone know if/when Palo Alto will support this Extension for decryption?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-26-2017 03:08 PM
To complete the story: Soon after my post in August I was informed that a flaw in implementing Extended Master Secret would be fixed soon. An update issued soon thereafter fixed the issue.
- 5081 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- stream timeout in General Topics
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- possibility of secure MQTT's decryption at Palo alto firewall in Next-Generation Firewall Discussions



