- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Interface Types
- LIVEcommunity
- Discussions
- General Topics
- Interface Types
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Interface Types
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 06:38 AM
When you are creating sub-interfaces, what is the reason why you would create layer 2 sub-interfaces?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 07:09 AM
Those would represent vlans in your trunk, they allow for easily assigning zones to each vlan and keeping packets contained within the same vlan tag
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 08:01 AM
Yes but a layer 2 interface wont have an IP, the only time I make sub-interfaces is when I need more logical layer 3 route points and dont have the physical port capacity.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 09:44 AM
Hello,
Correct, so what I do it create a vlan interface on the PAN that is layer 3 so that traffic can be routed.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 09:48 AM
Yes, but then your interface type is layer 3, not layer 2....
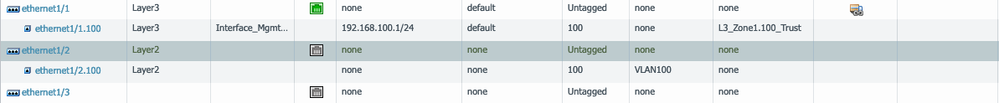
what be the purpose to setup an interface like Ethernet1/2 in the photo? What does a layer 2 sub-interface serve?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 09:52 AM
@reaper wrote:Those would represent vlans in your trunk, they allow for easily assigning zones to each vlan and keeping packets contained within the same vlan tag
Yep, just as Reaper mentioned. Here how it looks in practice.
Then you create the associated VLANs in the VLAN tab with the pertinent info.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 09:52 AM
Hello,
The Vlan interface would be layer 3 but the physical would still remain layer2. The purpose of the layer2 subinterface is what Reaper mentioned, a vlan trunk.
Perhaps I am not fully understanding the end result you are attmetping to accomplish? Would you be able to expand on this?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:00 AM
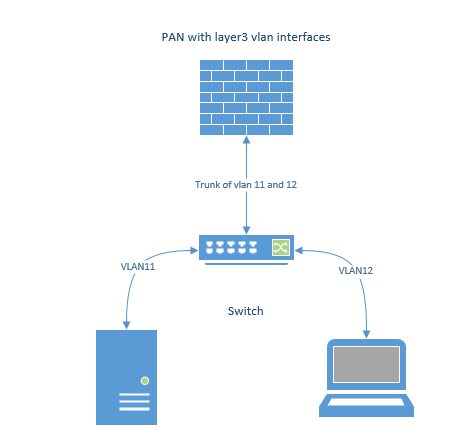
Ok what does a network diagram look like for this?
One switch connected to the PA with hosts on both vlan 11 and vlan 12. So when vlan 11 needs to talk to vlan 12 it NEEDS a layer 3 gateway so where is this? Unless there is another port that connects to a layer 3 router or switch upstream? But what is the design reason for that? Might as well run Layer3 on the PA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:05 AM
@stevenjwilliams83 wrote:Ok what does a network diagram look like for this?
... Might as well run Layer3 on the PA.
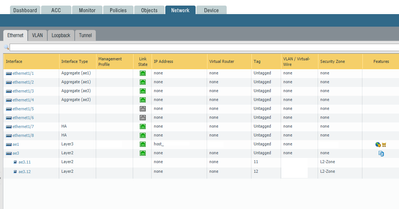
Yes, in my screenshot the FW is the GW for the 2 VLANs. Like @OtakarKlier mentioned we need to understand what you're trying to do.
If all you're trying to do is have your FW participate in a VLAN create a L3 interface (sub or otherwise) and give that interface an IP address in that network. Using routing (routing protocol or static) to tell the FW where to route for the network it's participating in.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:11 AM
Hello,
I would say the reason for it is you want inspection of the traffic between the two clients. The Layer3 interface would either need to be a router somewhere that touches each vlan, or you can created a Layer3 vlan interface on the PAN.
This way the traffic is inspected by the PAN. One reason for this design is to limit and inspect traffic between the two clients on the network.
Configure Layer 2 Interfaces with VLANs when you want Layer 2 switching and traffic separation among VLANs. You can optionally control non-IP protocols between security zones on a Layer 2 interface or between interfaces within a single zone on a Layer 2 VLAN.
Also check out this as to why Zero trust is a good thing and this is one way towards it.
https://www.paloaltonetworks.com/resources/whitepapers/best-practices-for-executing-on-zero-trust
https://www.youtube.com/watch?v=2IGe5zZMlDc
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:22 AM
I am not trying to do anything, I am just trying to understand it. So if my gateways exist on another device other than the PAN, why not run it in vwire between the switch and layer 3 device? Many ways to skin a cat, but trying to see what way others skin it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:24 AM
Totaly understand your viewpoint. From a security perspective the firewall should live in the middle of your network and everything should pass through it for inspection (zero trust). Yes its a bit more work, but more secure in the long run.
That is how I set things up :).
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 01:44 PM
@stevenjwilliams83 wrote:I am not trying to do anything, I am just trying to understand it. So if my gateways exist on another device other than the PAN, why not run it in vwire between the switch and layer 3 device? Many ways to skin a cat, but trying to see what way others skin it.
I think in a good majority of use cases the gateway is the firewall, in the cases where it's not then you're right vwire would also be an appropriate solution.
I've only ever deployed vwire once, in a limited deployment, but it's my understanding there are some things you can't do in vwire. So if you're looking to implement a vwire deployment I would be sure all features you need/want are supported. (I think response pages via vwire for non-decrypted traffic isn't possible.)
- 6321 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- Do Palo Alto VMs support GCP N4 gve driver? in General Topics
- Backup Peer HA1 IP Address ? in Next-Generation Firewall Discussions
- About PAN-303627 in Next-Generation Firewall Discussions
- Reason Why Logs Are Received by SLS but Not Stored in General Topics