- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Is it possible and OK to disable user cert caching?
- LIVEcommunity
- Discussions
- General Topics
- Is it possible and OK to disable user cert caching?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Is it possible and OK to disable user cert caching?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-09-2014 10:53 AM
After revoking a cert being for GP, the device is still able to connect. I found that it is cached somehow. So is it possible and OK to disable the caching of user certs for authentication?
> show system setting ssl-decrypt setting
vsys : vsys1
Forward Proxy Ready : yes
Inbound Proxy Ready : yes
Disable ssl : no
Disable ssl-decrypt : no
Notify user : no
Proxy for URL : no
Wait for URL : no
Block revoked Cert : yes
Block timeout Cert : no
Block unknown Cert : no
Cert Status Query Timeout : 5
URL Category Query Timeout : 5
Use Cert Cache : yes
Verify CRL : yes
Verify OCSP : no
CRL Status receive Timeout : 5
OCSP Status receive Timeout : 5
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-09-2014 11:38 AM
Hello czetazate,
Creating a Certificate Profile
Device > Certificate Management > Certificate Profile
Checking the "use CRL" option should be sufficient. The caveats would be, that if the firewall can not get to the CRL imbedded in the certificate, it would be considered valid. Also, if there is no CRL in the certificate, same behavior. You can check your "service routes"(by default the MGMT port), and make sure that the firewall can get to the CRL to check the certificate status
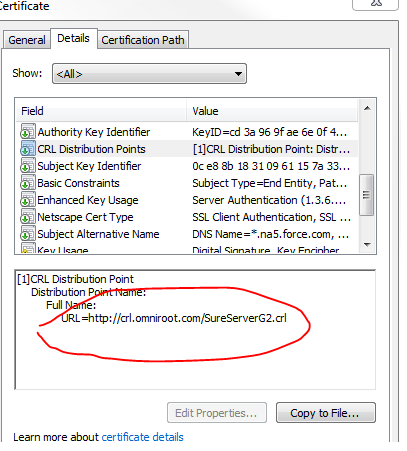
The certificate will usually tell where its corresponding CRL is hosted.
You can find out from the cert where the CRL is hosted as follows:
Ensure there is connectivity to the CRL link (check for general http/https connectivity, inline web proxies etc)
If it is an http link, you can simply pcap on the mgmt interface going to the IP where the CRL is hosted to check if the CRL is being downloaded or not.
> debug sslmgr view crl [CRL URL]
> debug sslmgr statistics
sslmgr statistics Count
------------------------------ -----------
Cert-status request lost 0
Cert-status request received 0
Cert-status request processed 0
Certificates revoked by CRL 0
Certificates revoked by OCSP 0
Certificates confirmed by CRL 0
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-09-2014 11:59 AM
Hi dmaynard, yes I did see the document and confirmed that the CRL is reachable and I can see the CRL that is loaded onto the firewall. The problem is that it stays there unless you run a series of commands. I can't remember exactly the sequence but I had to delete the CRL and then kept trying to connect (which kept succeeding) but eventually I managed to get the client or firewall to check the CRL. So now, I'd like to either disable the caching, adjust the timeout period when the next CRL check is or somehow force the firewall to grab a new CRL.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-09-2014 06:12 PM
I've confirmed that certificates are cached.
The command to show the cache is
show system setting ssl-decrypt certificate-cache
To delete the cache certs then issue.
debug dataplane reset ssl-decrypt certificate-cache
But what I really want is to turn off caching altogether so that if I revoke a cert, the user can't connect anymore.
- 5800 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- Activate ECMP without trafic disruption in Next-Generation Firewall Discussions
- How to create a support case without a TCF file in Next-Generation Firewall Discussions
- stream timeout in General Topics
- How to disable firewall from contacting hawkeye.* in General Topics