- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Making server available with NAT doesn't work
- LIVEcommunity
- Discussions
- General Topics
- Making server available with NAT doesn't work
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2014 12:01 PM
Today I tried to configure our PA500 firewall to make a server from our DMZ zone available for Office 365. But first I will explain our network topology.
In our company we have 2 internet lines, one for internet and the other one as backup. After this backup line we have several public IP adresses, so I want to use these IP adressen for publishing my DMZ server.
So I configured the settings, but its not working at all. The server can't get to internet and the internet can't reach the server (like a ping).
In the monitoring I see that the server can send bytes to the internet with the correct NAT IP, but doesn't recieve anything from the internet.
Everything I configured I took a screenshot and loaded it up with this post. Belacom is the backup line. Can someone help me out?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2014 04:37 PM
Hello Zebit,
From your NAT policies, it looks like your primary ISP is on ethernet 1/3 and the secondary is ethernet 1/4. Is this correct?
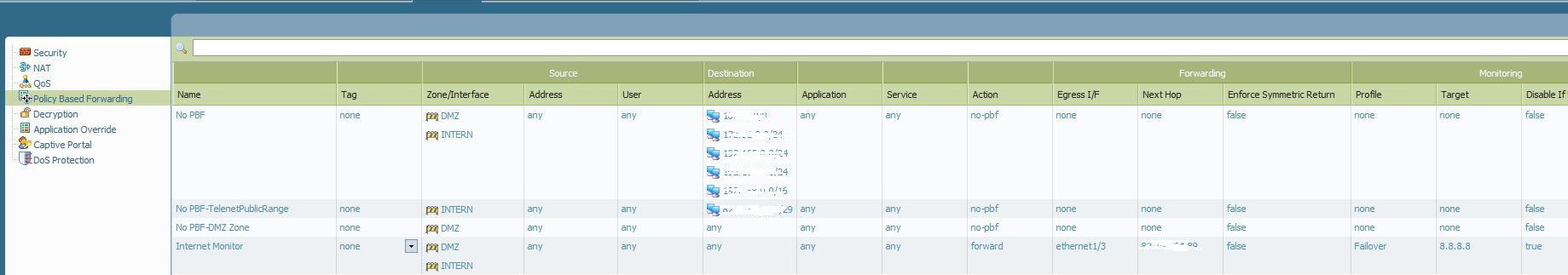
I notice that your PBF policy dictates that all traffic sourced from the INTERN and DMZ zones should be forwarded out of eth1/3.
Based on your description, if you are trying to use a Public IP address given to you by the secondary ISP, then your current configurations would not work.
Problem #1
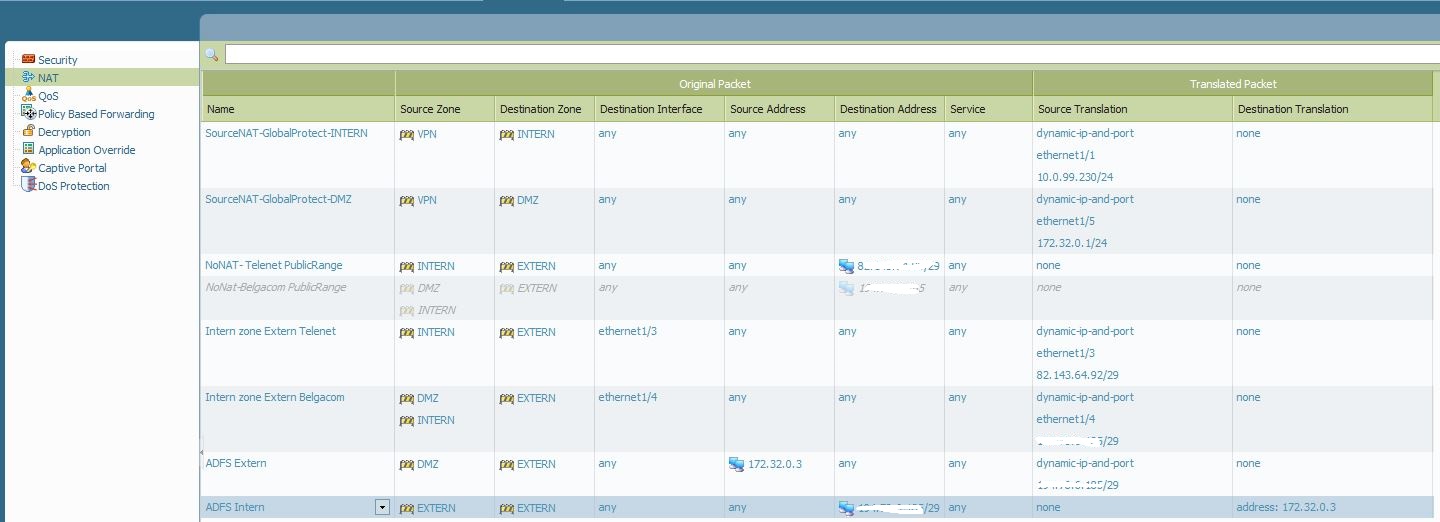
I'm assuming that your Office365 server's IP address is 172.32.0.3 and your ISP_1 public IP is 100.100.100.100 and ISP_2 public_IP is 200.200.200.200.
You have configured the 200.200.200.200 to be NAT'd to 172.32.0.3 so that when anyone on the internet pings that public IP, it would be sent to the server's private address. (NAT Policy "ADFS Intern").
When that traffic ingresses on eth1/4 for 200.200.200.200, your secondary ISP connection, the return traffic will incorrectly egress out of eth1/3 based on the configured PBF (Internet Monitor).
To fix this, you would need to configure a PBF policy with symmetric return and position it above the "Internet Monitor" policy.
Basically, this would make the firewall send responses out on the same interface that the requests had come in. Here is a document that explains this concept in greater detail:
How to Configure Symmetric Return
Problem #2
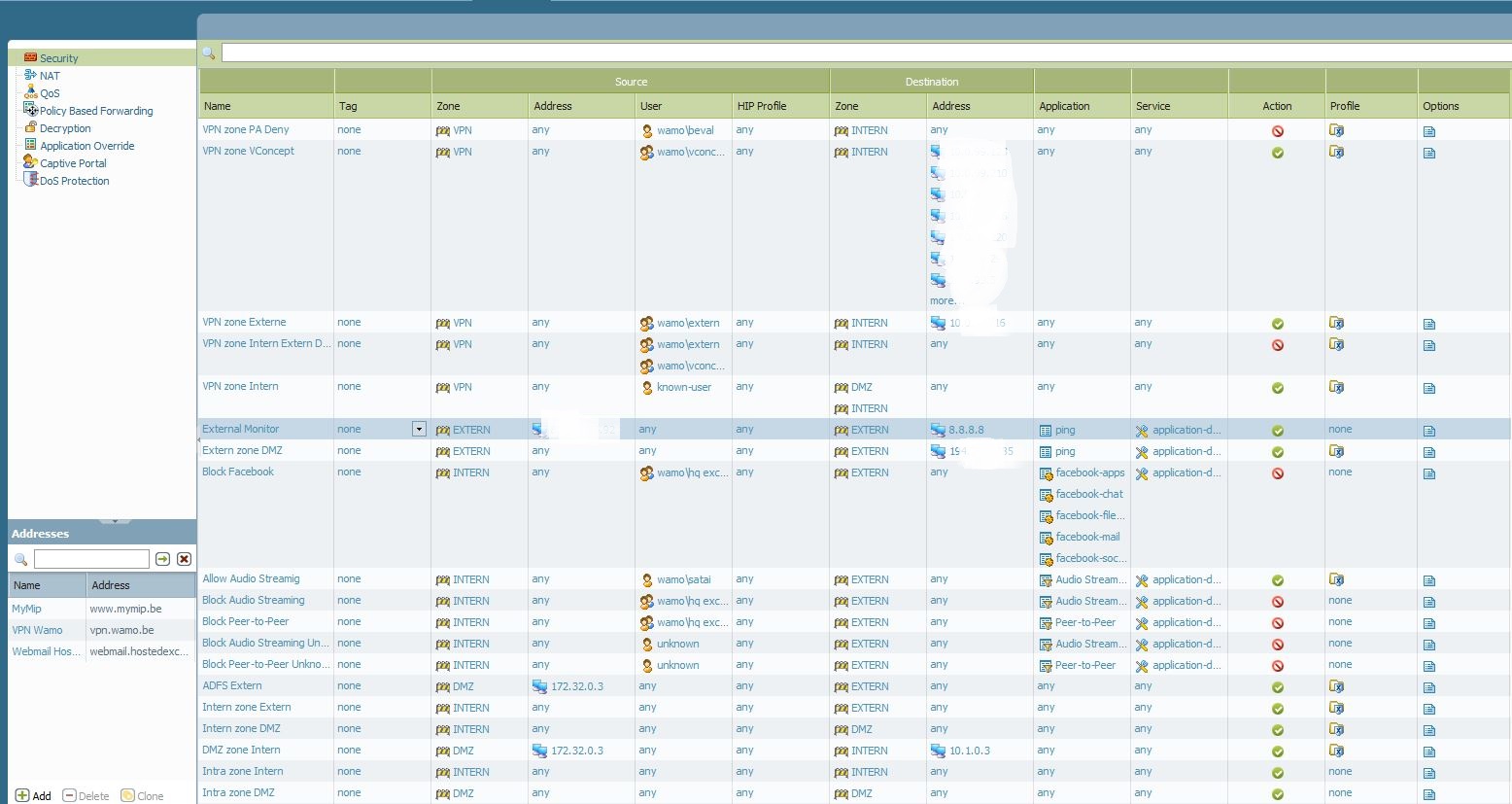
I'm assuming the "Extern zone DMZ" security policy is the one that should permit traffic from the EXTERN zone to the DMZ zone.
If that's the case, you would need to configure the source zone as EXTERN while the destination zone should be DMZ zone.
Pages 15-16 of this document explain this configuration in greater detail as well:
In the future, I'd suggest that you open a case with Support to help resolve this type of issue, but let us know if the recommendations above help to solve the problem.
Regards,
tasonibare
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2014 04:37 PM
Hello Zebit,
From your NAT policies, it looks like your primary ISP is on ethernet 1/3 and the secondary is ethernet 1/4. Is this correct?
I notice that your PBF policy dictates that all traffic sourced from the INTERN and DMZ zones should be forwarded out of eth1/3.
Based on your description, if you are trying to use a Public IP address given to you by the secondary ISP, then your current configurations would not work.
Problem #1
I'm assuming that your Office365 server's IP address is 172.32.0.3 and your ISP_1 public IP is 100.100.100.100 and ISP_2 public_IP is 200.200.200.200.
You have configured the 200.200.200.200 to be NAT'd to 172.32.0.3 so that when anyone on the internet pings that public IP, it would be sent to the server's private address. (NAT Policy "ADFS Intern").
When that traffic ingresses on eth1/4 for 200.200.200.200, your secondary ISP connection, the return traffic will incorrectly egress out of eth1/3 based on the configured PBF (Internet Monitor).
To fix this, you would need to configure a PBF policy with symmetric return and position it above the "Internet Monitor" policy.
Basically, this would make the firewall send responses out on the same interface that the requests had come in. Here is a document that explains this concept in greater detail:
How to Configure Symmetric Return
Problem #2
I'm assuming the "Extern zone DMZ" security policy is the one that should permit traffic from the EXTERN zone to the DMZ zone.
If that's the case, you would need to configure the source zone as EXTERN while the destination zone should be DMZ zone.
Pages 15-16 of this document explain this configuration in greater detail as well:
In the future, I'd suggest that you open a case with Support to help resolve this type of issue, but let us know if the recommendations above help to solve the problem.
Regards,
tasonibare
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2014 11:20 PM
Hi Tasonbare,
You understand my issue correct, I will try your sugesstions and come back to you.
- 1 accepted solution
- 2903 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need help on this XSOAR Weird behavior on preprocessing scripts in Cortex XSOAR Discussions
- Badbox malware in General Topics
- Panorama scheduled export path in Panorama Discussions
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions
- Cortex XDR 8.9 Non-Persistent Citrix Servers and Cache Write Issue in Cortex XDR Discussions



