- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
One Internet line Multiple intefaces
- LIVEcommunity
- Discussions
- General Topics
- One Internet line Multiple intefaces
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
One Internet line Multiple intefaces
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2018 02:37 PM - edited 09-03-2018 02:40 PM
Hi Everyone
In my sinaro i have one internet line 10 MB and i have 5 zones configured in PA my question . and each zone for different purpose for example (IP SEC - Intenet -Email)
1- how i can provide the internet to multiple zones with a multiple services
2- How many Public ip address reqiued for this sinaro
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2018 06:03 PM
@MFayez wrote:
1- how i can provide the internet to multiple zones with a multiple services
With a NAT rule where you configure your internet facing interface as translated source address
@MFayez wrote:2- How many Public ip address reqiued for this sinaro
It depends how many servers you need to make available and even more important what services do the offer. For example if you have the PA as VPN gateway, one emailserver and one webserver then you only need one public IP. In case you have multiple webservers and all expose their websites on port 80 and 443, then you either need one address for each of them or you place a reverse proxy in front of them and then you still only need one IP as the reverse proxy forwards the requests to the apropriate server based on the URL.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2018 10:23 PM
Hi
Thanks for the answer
If I have one PA device for this example this work ....
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 01:04 AM
Why do you need a zone for each service?
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 02:39 AM
I think you have the wrong idea of zones. Zones are collection of interfaces/subnets that we write policies against.
In the policy we specify the specific services and ports not in the zones.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 03:27 AM
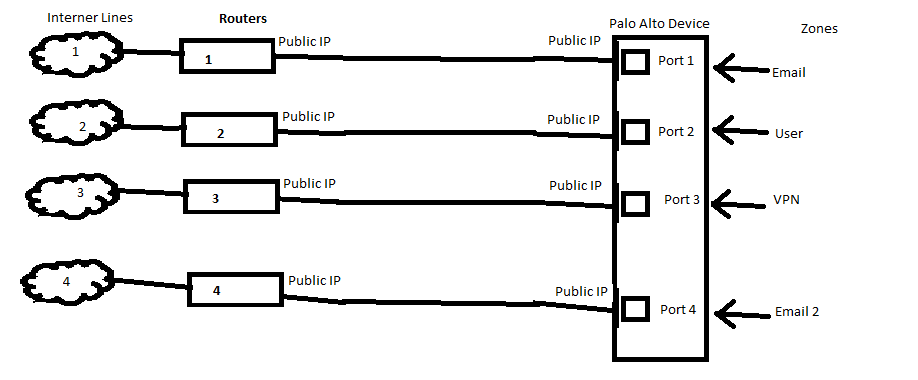

- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 03:32 AM
For the new setup
how many public IP's do we need?
how will natting work for the interfaces?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 04:29 AM
What "IP" service ports are being connected to by each application? if none of them overlap then 1 public IP will do.
You also don't need to use 4 physical connections to the router ( you could tag VLANS into one single port )
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 03:15 PM
Typically this is how you would be looking at your public facing services.
How many different public ip addresses do you need and for what services then add one for the PAN. You request then from your ISP the appropriate subnet sized for that need, in your case looks like you will need either a /29 or /28.
This gets delivered on the ISP device facing your PAN. You use one of these addresses on the PAN.
This is now your untrust zone.
You now organize your publicly facing resources into risk groups and create the muliple zones and private networks to support them or if the risk is similar they can all go into one DMZ zone. These are the inside interface(s) of your PAN with zone assignments.
Now you create your nat rules pointing each ip address from the ISP scope at the matching internal address of the server providing the public service. And write the security policies needed for the inbound and outbound communications for each server.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2019 01:07 AM
this case still is not clear for me i will explain current setup
1- 4 router is connected phiscaly to PA and each router provide defrent services (Email , Internet , VPN)
2- PBF are configer for pass the traffice and NAT
3-One defult routur are configer for untrust zone for all services
Our reqiuerment :
1- Shift to 4 router to 1 Fiber line
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2019 01:21 AM
So -One router.
You no longer need PBF as you only have one route out.
You have 2x incomming SMTP so you need an IP for each on service port [25 & 587]
Everything else does not overlap in terms of service port so can use either of the IP's.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2019 01:32 AM
Okay ...
What about interface is required to create subinterface because i will user on physical line
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2019 01:43 AM - edited 06-18-2019 01:44 AM
No sub interface is necessary.
Have one interface external with the IP you want to be the primary and nat rules..
Then just have an inbound NAT for the second IP. (Untrust->Untrust)
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2019 10:59 PM
Thanks @RobinClayton for your advise
I will got from ISP 6 public ip address
Should added the IP to interface !!
and it can be assigned to Zones
- 9606 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Prisma Access with ECMP in Prisma Access Discussions
- RQL Query Works in Investigate > Search but Fails in Policy Definition (Terraform v1.5.7 Example Included) in Prisma Cloud Discussions
- Is possible to implement Failover Handling Integration (BYOI) in Cortex XSOAR Discussions



