- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
OS 7.1 blocking telnet over SSL
- LIVEcommunity
- Discussions
- General Topics
- OS 7.1 blocking telnet over SSL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
OS 7.1 blocking telnet over SSL
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 10:31 AM
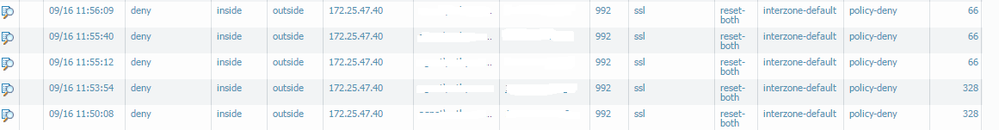
We have in-house software that uses secure-telnet port 992 and that has been blocked after the 7.1.4-h2 upgrade. I've created a rule to pass the traffic to the destenation address with any application any service but never help, the logs said reset both by internzone rule, only changing interzone rule to allow will let the application communicate. Even I did appliaction override on the SSL with destinationa port and address not helped me at all.
Please any clue how to fix this?
Mike
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 10:39 AM
Hi,
What version of PAN-OS you had before?
Can you post screenshot of the policy and deny logs please.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 10:53 AM - edited 09-16-2016 11:29 AM
Hi,
Thanks. So your traffic is denied by default policy cause it does not match any other policy. Can you show me a policy config pls for this particular session? What was your policy before an upgrade? Did you try to create a rule with SSL app and destination port 992. I understand you have tried any any but l had strange behaviour, similar to yours. So when l created rule to be more specific it worked for me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 12:09 PM
I tried specific rule to destenation IP and a service with the port on both UDP and TCP, then tried application SSL then tried unknow-tcp and unknown-udp all togehter nothing works. my default inside to outside rule is any application with default application with profiles.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 12:33 PM - edited 09-16-2016 12:34 PM
Ok. So from what l understood you have a policy inside >outside with application "any" and the service "application-default".
So PAN-OS 7.1 changes the behaviour for the policy with application-default specified. See below:
Your policy will allow any APPs but only on the default ports. From the logs, we can see that you have SSL as an application but 992 as a port. Default inter-zone has any any that is why it is permitting your traffic.
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2016 01:39 PM
I think when I configure the destination by IP only the rules not match as now I put /32 on the destination IP that made the rule match
- 6215 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Stealth Rule Question in Next-Generation Firewall Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions
- Notepad++ block specific hash version in Cortex XDR Discussions
- looking to block google ai mode in Advanced URL Filtering Discussions