- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA inbound decryption
- LIVEcommunity
- Discussions
- General Topics
- PA inbound decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 09:57 AM - edited 03-11-2018 10:09 AM
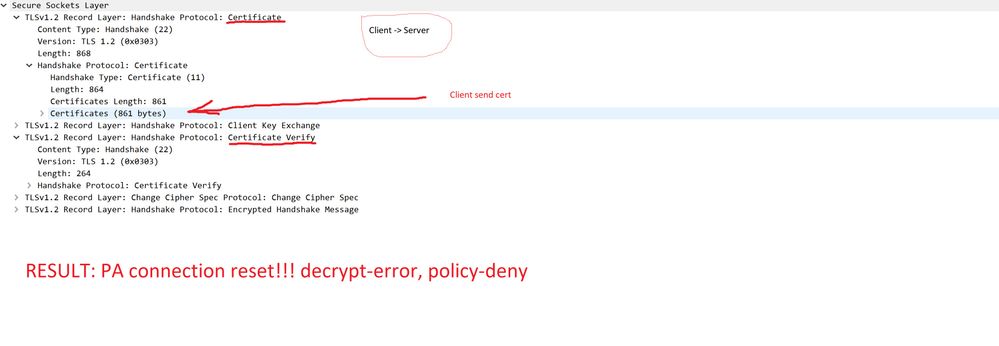
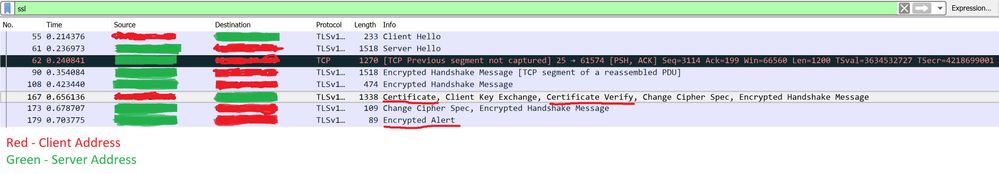
PA drop (decrypt-error, policy-deny) packet when client present a certificate (SMTP STARTTLS).
PAN OS version: 8.1
Test cases
1) Client cert TRUSTED, TLS 1.2 with ECDHE-RSA-AES256-GCM-SHA384
Client send Certificate Verify TLS payload
openssl s_client -starttls smtp -crlf -tls1_2 -cert trusted-cert.pem -key private.key -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
result: Connection reset by PA (decrypt-error, policy-deny)
2) Client cert UN-TRUSTED, TLS 1.2 with ECDHE-RSA-AES256-GCM-SHA384
Client send Certificate Verify TLS payload
openssl s_client -starttls smtp -crlf -tls1_2 -cert un-trusted-cert.pem -key un-private.key -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
result: Connection reset by PA (decrypt-error, policy-deny)
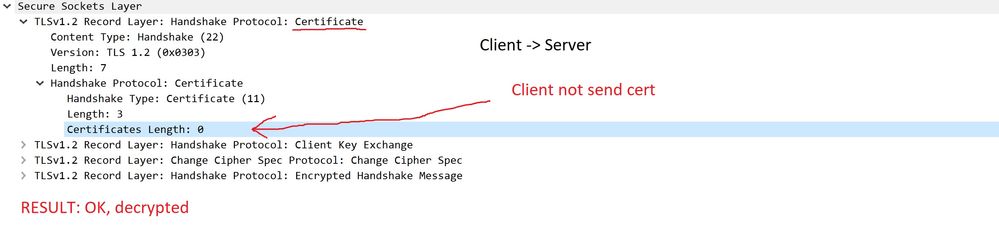
3) Client cert ANONYMOUS, TLS 1.2 with ECDHE-RSA-AES256-GCM-SHA384
Client NOT send Certificate Verify TLS payload
openssl s_client -starttls smtp -crlf -tls1_2 -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
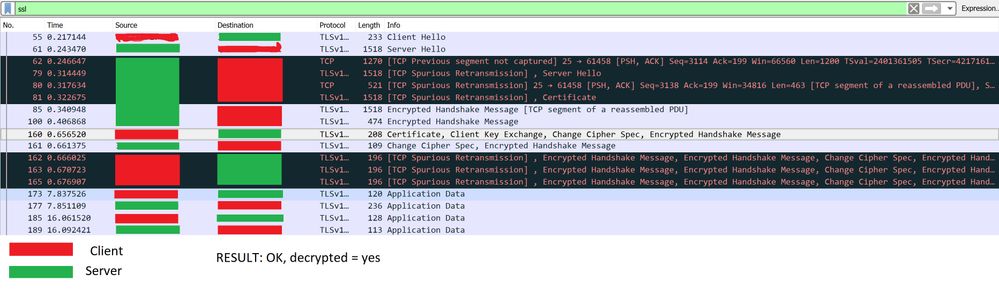
result: IT`s WORK (OK)
================================================================================================
Attached captured packets pictures
Please help, thanks.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2018 10:43 AM
Solved!
Client (google smtp server) send certificate when my smtp server ask. In this case inbound decryption not work!!!
I disable postfix configuration option smtpd_tls_ask_ccert = no, and fine work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 10:23 AM
Hi @blabla
As far as I know, inbound decryption or decryption in general on a paloalto networks firewall does not support connections with client certificates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 12:20 PM
Hi @Remo
This is not client cert based auth. In this case client is google smtp server, wich during sending email over STARTTLS (TLS 1.2 ECDHE-RSA-AES256-GCM-SHA384) for my smtp server, presents his client`s certificate (trusted), that verify my smtp server. The problem is PA drops (policy-deny) packets in this case. In that case inbound decryption does not properly work and does not check incoming smtp traffic. Why?
thanks for answer
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 12:37 PM
Hi @blabla
In that case, when this is not client cert auth, I need to ask you to explain me why you specify a keyfile in the s_client command?
Do you allow connections that cannot be decrypted in the decryption profile attached to the decryption rule? And you wrote that this problem happens with 8.1 - was it working as expected prior to the upgrade?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 01:08 PM
openssl s_client -starttls smtp -crlf -tls1_2 -cert trusted-cert.pem -key private.key -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
This command just simulates behavior of google smtp server when it sends email (over TLS) to my server. In this case trusted-cert.pem file is trusted certificate like as in google smtp server.
========================================================
openssl s_client -starttls smtp -crlf -tls1_2 -cert un-trusted-cert.pem -key un-private.key -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
This command just simulates like previous command but uses untrusted (self signed) certificate (just for experiment).
========================================================
openssl s_client -starttls smtp -crlf -tls1_2 -cipher 'ECDHE-RSA-AES256-GCM-SHA384' -connect SMTP_HOST:25
This command just simulates like previous command but doesnt use cert and key (ANONYMOUS, generated by openssl), in this case openssl doesnt send client certificate and decryption goes right. But google smtp always sends his certificate when sending email (over STARTTLS) to my smtp server.
=======================================
>>Do you allow connections that cannot be decrypted in the decryption profile attached to the decryption rule?
Yes, all policy rules allow, decription profile Min version: SSLv3 Max version: MAX, all block options unchecked, not block.
>>And you wrote that this problem happens with 8.1 - was it working as expected prior to the upgrade?
I had PANOS version 7.1. The problem didnt solve. I upgrated from 7.1 to 8.0 version. The problem didnt solve. Finally, I upgrated from 8.0 to 8.1, but the problem didnt solve.
Thanks for answer.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 01:16 PM
After all upgrades i reimport my server certificate and private key.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2018 02:35 PM
@blablawrote:After all upgrades i reimport my server certificate and private key.
And it still does not work right?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2018 10:43 AM
Solved!
Client (google smtp server) send certificate when my smtp server ask. In this case inbound decryption not work!!!
I disable postfix configuration option smtpd_tls_ask_ccert = no, and fine work.
- 1 accepted solution
- 7922 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions



