- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption Certifcate GPO Distribution
- LIVEcommunity
- Discussions
- General Topics
- SSL Decryption Certifcate GPO Distribution
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption Certifcate GPO Distribution
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-03-2013 06:41 PM
When exporting a certificate used for inbound ssl decryption which is to be deployed throughout a company through GPO to Internet Explorer, do you have to select Export Private Key or is it okay to just export the certificate?
What is the difference between File Formats PEM and PKCS12?
If a company created their own CA, does this also require the distribution of certificates through GPO? How will the workstations within that company know to trust the internal CA.
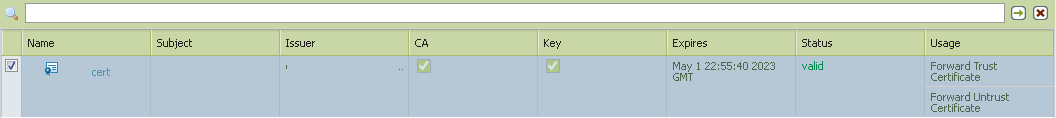

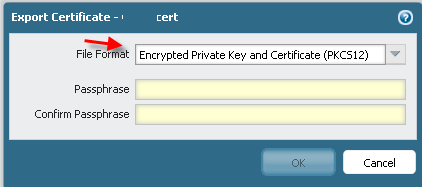
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2013 03:26 PM
1) Do _NOT_ export the private key. The client should _ONLY_ have the public key of the CA being used.
2) In short PEM is the certs/keys in "cleartext" while p12 is a package which can have a passphrase before you can read its content.
3) I would recommend you to setup a dedicated CA to be used for termination. The public key of this CA can be deployed through GPO to the clients. I think there is a technote somewhere around here describing what and how to do the GPO magic.
A thing to consider (performance-wise) is the keylength you wish to use for this CA. 512 bytes is good for performance but often not good enough security-wise. However this cert is only being used on your internal network that is between your PA and your clients which gives that you wont need 16384 bits for this keylength but 4096 or 2048 should be enough (or if possible 512).
The longer the key is the longer it takes for the PA to setup the SSL with the client (or rather for the client to setup the SSL with the PA).
Edit: Here are the SSL-docs I had in mind:
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2013 05:20 PM
"3) I would recommend you to setup a dedicated CA to be used for termination. The public key of this CA can be deployed through GPO to the clients. I think there is a technote somewhere around here describing what and how to do the GPO magic."
Can you help me understand the pros and cons of using a dedicated CA instead of using the CA the PA devices generate? What type of dedicated internal CA would you recommend, Windows? I've been researching the CA types and most Windows CA's seem to require Active Directory, can I setup a Windows CA without Active Directory services in a cluster? Thank you for your response it was very helpful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2013 01:17 AM
If you create the cert within the PA box then this will become your dedicated CA.
In this case I would recommend you do two exports:
1) Public and Private key as p12 (with passphrase) - store this safetly offline. This is a backup of your public/private keypair. If you use HA this export should be imported on the other PA device.
2) Public key as p12 (with passphrase - best practice if you ask me), or as PEM if you like. This one can be stored online and its this public key which you will by GPO "install" on the clients as "Trusted CA" (or manually install on boxes which are not part of your AD).
The point of installing this public key as trusted CA is to avoid getting warnings in your browser that this ssl session cannot be trusted (that is if you didnt install this public key as trusted CA).
Other methods is to use openssl to create this "CA-cert" (or rather selfsigned cert where private and public key is put into the PA device and the public key put into the clients "Trusted CA" container). If you need a GUI then TinyCA2 is a great help:
http://www.ghacks.net/2009/09/16/create-your-own-certificate-authority-with-tinyca/
That is as long as you dont have any corporate policy on how certs that are being used or trusted by your clients should be created (like using an offline HSM setup etc). In this case things like OSCP/CRL is not needed which gives that you wont "need" a PKI environment to generate the CA cert being used for termination - using PA builtin method to create this by the PA box itself is all what you need (function-wise).
- 3786 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SSL Decryption for Outbound Traffic and the Block Private Key Export option in Next-Generation Firewall Discussions
- Understand the "Block Private Key Export" option with three scenarios in Next-Generation Firewall Discussions
- SSH connection drops randomly in General Topics
- SSL Decryption in General Topics
- SSL Descryption Windows 8 in General Topics



