- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption: ERR_HTTP2_INADEQUATE_TRANSPORT_SECURITY
- LIVEcommunity
- Discussions
- General Topics
- SSL Decryption: ERR_HTTP2_INADEQUATE_TRANSPORT_SECURITY
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption: ERR_HTTP2_INADEQUATE_TRANSPORT_SECURITY
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2020 02:48 AM
Hi paloalto community,
we're currently still testing ssl decryption and discovered a new error, which I can't google to find a solution.
If we're visiting the following site, we get an "ERR_HTTP2_INADEQUATE_TRANSPORT_SECURITY" error. Site: https://www.1erforum.de/
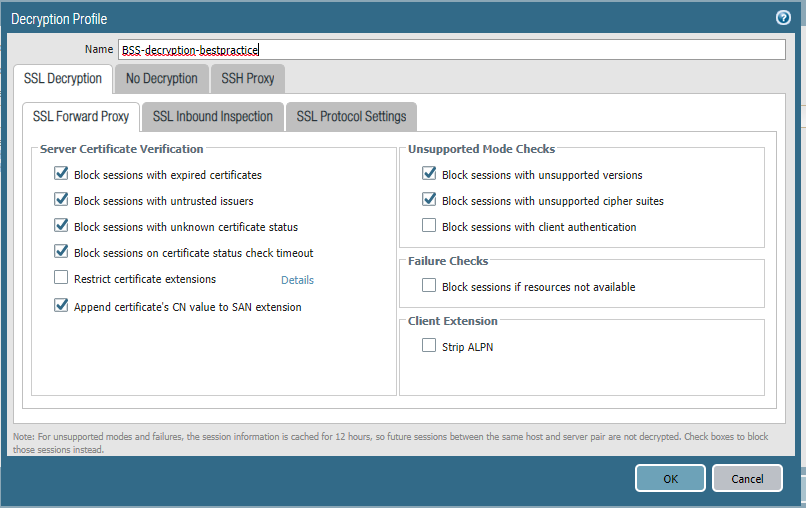
See attached our configuration and ssl information without decryption enabled.
Firmware and Specs:
PA 850 - FW 9.0.5
Settings:
Decryption disabled:
Decryption enabled:
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 12:20 AM
1erforum.de is using:
The connection to this site is encrypted and authenticated using TLS 1.2, ECDHE_RSA with P-256, and AES_128_GCM.
di.fm (same error here too) is using:
The connection to this site is encrypted and authenticated using TLS 1.2, ECDHE_RSA with P-256, and AES_128_GCM.
At this point ssl decryption gets pointless, since a lot of websites are using this combination. Looks like a firmware issue?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 01:43 PM
The reason that I asked what ciphers it's using is simply due to a lot of websites not actually enabling HTTP/2 correctly, but those all check out and should work perfectly fine. I'm not sure that it's actually a firmware issue, I can check to see if I run into the same issue this evening though.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2020 05:21 AM
That would be great. i'm looking forward to hearing from you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2020 04:44 PM
This doesn't appear to be a software bug, the error is present in 9.0.4 and 9.1.0 as well; it also isn't an issue with the cipher suites, we can decrypt other sites perfectly fine using the same ciphers. It does however appear to be very specific to Chromium based browsers (Chrome, new Edge) as Firefox loads the site without issue.
I can't tell how this is loading in Chrome when you attempt to decrypt it, but on Firefox it uses the TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 cipher when you decrypt it when I copy the same decryption profile settings you have listed. Might want to reach out to support and see if they can point you in the right direction, but they might just call this a browser issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2020 04:05 AM
I have the same issue on 9.1.0 VM-50
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2020 04:12 AM
I have firefox 71.0 and have the same issue. The error just appears differently. The only browser is working correctly is an old IE in Win7.
From the firefox:
Your connection is not secure
The website tried to negotiate an inadequate level of security.
www.di.fm uses security technology that is outdated and vulnerable to attack. An attacker could easily reveal information which you thought to be safe. The website administrator will need to fix the server first before you can visit the site.
Error code: NS_ERROR_NET_INADEQUATE_SECURITY
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2020 06:23 AM
I would expect this site to have issues; it defaults to using the TLS_RSA_WITH_AES_256_CBC_SHA cipher which is an inadequate cipher for HTTP/2
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2020 09:11 AM
don't know, it might sound silly, but if IE has managed to negotiate with the site and is able to show its content, why PA can't do the same and use a compatible protocol to show the site content?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2020 12:02 PM
IE doesn't care if you are using a weak cipher suite, which is why it's working in IE but not Firefox or Chrome. The bigger issue is why the decryption process isn't negotiating to the strongest available cipher unless the site has been configured with a cipher preference that makes it utilize the strongest cipher suites by default (such as Chrome). It appears through additional troubleshooting that the firewall is using the first matching cipher, which in the case of these example sites isn't strong enough to meet the requirements of the browser.
In fairness to PAN, the HTTP/2 connection shouldn't be attempting to use a questionable cipher suite such as in the di.fm example. The vast majority of the HTTP/2 enabled websites will work perfectly fine, because the site owner is specifying the preferred order with strong to weak ciphers. In the examples listed so far the server is providing no preference order, which could be causing the firewall to negotiate to one of the weaker cipher suites being offered by the server.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2020 08:55 AM - edited 01-20-2020 08:57 AM
Sounds like a feature which the PA team should consider? For my point of view it's more like a bug. If browsers can view the page, the PA should do it too.
For our users the current state is very bad - they will assume the page (e.g. of a customer) is not working, but instdead we have to whitelist it to exclude it from decryption.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-19-2020 04:08 AM
Hello together,
same issue applies for us (PANOS 9.0.5 & 9.0.6, incl. Prisma Access) and a solution would be very appreciated.
Best regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2020 11:32 PM
The same issues also applies to the site: uebermedien.de
- 61283 Views
- 36 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions