- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL decryption using incorrect security policy
- LIVEcommunity
- Discussions
- General Topics
- SSL decryption using incorrect security policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-31-2015 11:21 AM
Hello all,
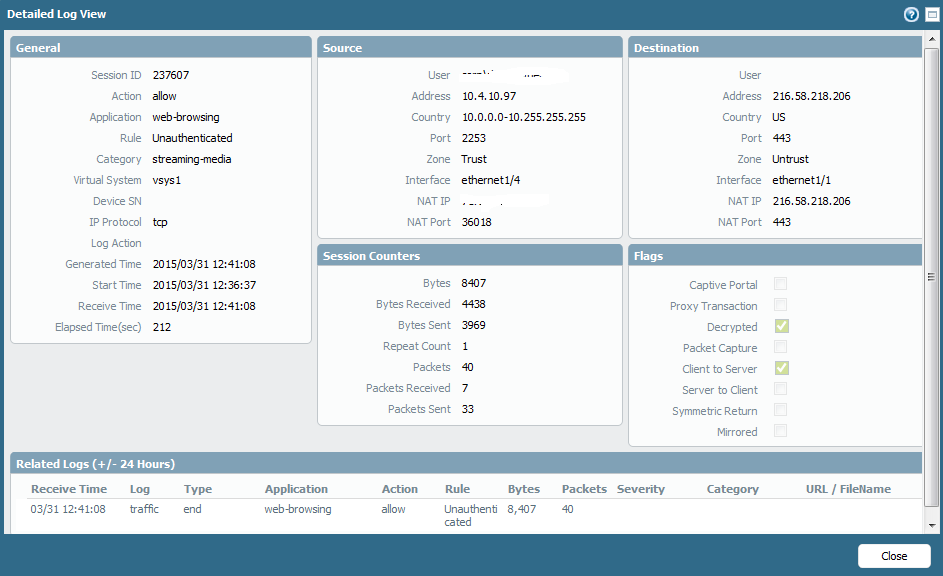
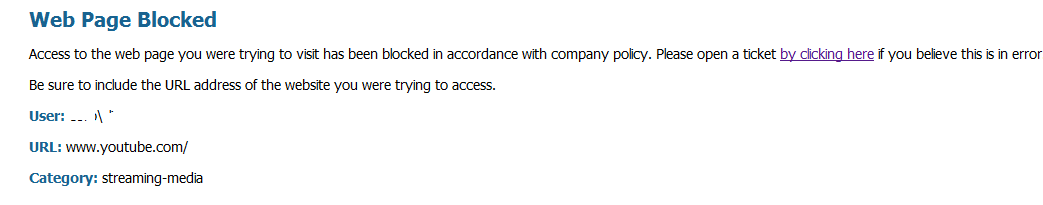
I am testing out SSL decryption on a few categories. For now I am using a system generated certificate and it works in decrypting the categories I have selected. The problem is that once it is decrypted, it doesn't use the proper security policy. We have AD integration and URL filtering set up between certain groups. My user ID has elevated browsing privileges but after the session is decrypted it uses the policy I have set up when the firewall doesn't know who the user is so I am getting blocked. Any idea why it wouldn't use the correct security policy when the log view and blocked page are showing my user ID?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2015 08:27 AM
My guess is that the app is now "web-browsing" due to decryption, but the port is still 443. You're using application-default as the service for the first rule (and I'm assuming "web-browsing" is included in that filter) so that would only match if web was on 80, but I'm guessing that you have port 443 included in the "service-web" service group on the other rule, and "web-browsing" included in "web-services".
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2015 05:28 AM
Hi Clint
Can you also include a screenshot of the security policy?
The security policies are processed top to bottom with the first match (not "best" match) being the rule that is used to pass traffic, so if your top rule does not have a source user restriction this would be normal.
have you set that rule to use source user "unknown" or "any" ?
regards
Tom
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2015 06:06 AM
Here you go. The rules work fine with no decryption but when it is turned on for some reason it jumps over "Netit".


- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2015 08:27 AM
My guess is that the app is now "web-browsing" due to decryption, but the port is still 443. You're using application-default as the service for the first rule (and I'm assuming "web-browsing" is included in that filter) so that would only match if web was on 80, but I'm guessing that you have port 443 included in the "service-web" service group on the other rule, and "web-browsing" included in "web-services".
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2015 08:28 AM
I think you may be correct, sir. I'll give it a try here shortly and let you know.
Edit: That was it. Thanks!
- 1 accepted solution
- 5520 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- web file blocking in Next-Generation Firewall Discussions
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- possibility of secure MQTT's decryption at Palo alto firewall in Next-Generation Firewall Discussions
- URL citrix.rsieh.com is inaccessible through firewall in General Topics



