- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
syn without window-scale option
- LIVEcommunity
- Discussions
- General Topics
- syn without window-scale option
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
syn without window-scale option
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2018 06:20 AM
Hi community,
i am trying to access a website from LAN side of palo alto, even though correct policy is configured, tcp handshake was not complete. after packet capture i am able to find below points
- client sending syn packet
- but i am not able to get syn-ack packet from server,
- able to see one ack packets from server
- server is using 3-way handshake only
- server is sending syn-ack, but tcp window-scaling option is not available.
i have seen firewall will drop packet if window scaling information is not available in syn packet. can anybody tell whether i am hitting on same issue, if yes, how to solve it in palo alto
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2018 09:42 AM
Hello,
Was the pcap performed from the PAN or from the client? I honestly suspect a routing issue since you are not getting any ack's.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2018 09:58 PM
Hi klier,
No routing issue is involved, i am able to acces other sites, only this particular site is is not accessible. when i bypass firewall, i was getting syn-ack packet in my PC. when i access through firewall, firewall is dropping that particular packet.
for other sites, bypassing firewall or accessing through doesn't make any difference.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 11:18 AM
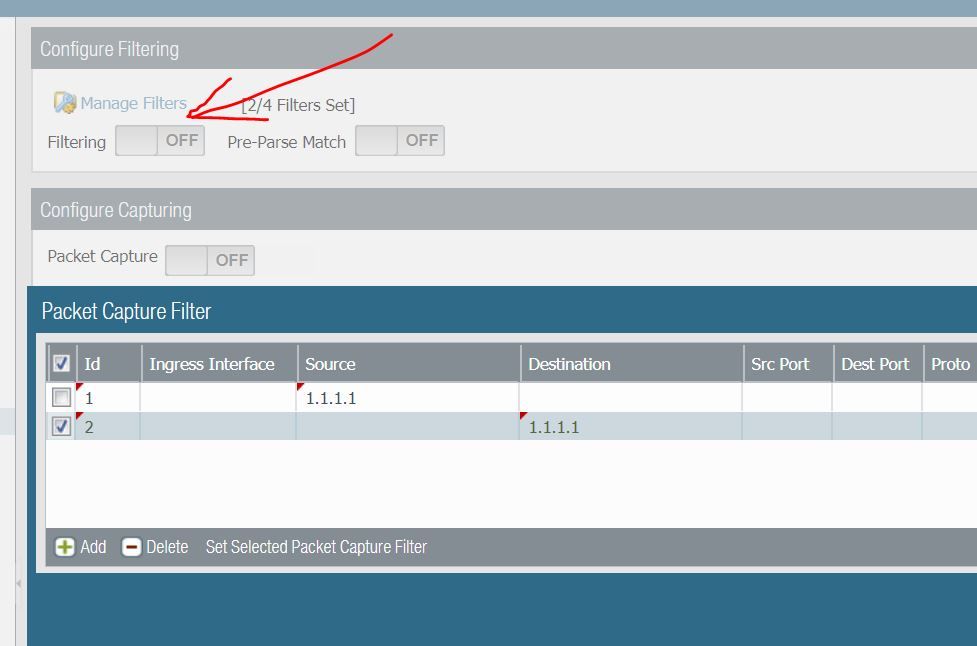
Add filter.
Assuming that website IP is 1.1.1.1
Monitor > Packet Capture
Enable filter.
Go to cli and run command.
> show counter global filter delta yes packet-filter yes
Try to visit website and run command again.
> show counter global filter delta yes packet-filter yes
Do you see any where severity is drop?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 11:08 PM - edited 11-16-2018 11:15 PM
Hi Radio,
Thanks for your input.
the counter was increasing in my case because of out-of-window packets. after putting 'set deviceconfig setting tcp asymmetric-path bypass' command, the website is accessible. it solved my issue. but it does look like an workaround only as the command is designed for assymetric routing. as of my understanding, in my case, definitly the issue is not assymetric but because of firewall doesnt have window information.
if i put this command, will i get any security risk as replay attack?
- 7129 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- ServiceNow CMDB data to XSIAM in Cortex XSIAM Discussions
- Strata Cloud Manager UI language and translations in Strata Cloud Manager
- Migration problem from PA220 to PA540 - Virtual Router in Next-Generation Firewall Discussions
- Cortex XDR Device Control Violation Alerts in Cortex XDR Discussions
- looking to block google ai mode in Advanced URL Filtering Discussions