- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Vypr VPN
- LIVEcommunity
- Discussions
- General Topics
- Re: Vypr VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2016 03:17 AM
Hi,
Has anyone used VYPR VPN. We are seeing users use this quiet a lot and they are bypassing the firewall to get onto whatever they want.
We have submitted to PAN to create an application for this as one does not currently exist, but we need to block this in the mean time. I know we can create a custom application for this, but I am not experienced enough to put in the details for this so it only affects that application.
Is creating a custom application the best way to block this or would anyone recommend another way ?
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2016 08:58 AM - edited 01-22-2016 10:43 AM
While some of their VPN protocols are standards-based with corresponding AppIDs, I bet you're having problem with the "chameleon" variant.
If you can't block it by AppID, you should be able to tackle this via FQDN address objects. They've provided a complete list of their servers here:
- https://support.goldenfrog.com/hc/en-us/articles/203733723-What-are-the-VyprVPN-server-addresses-
The CLI will probably be the quickest way to get these entries in your firewall. Here's what the commands would look:
set address us1.vpn.goldenfrog.com tag vyprvpn
set address us1.vpn.goldenfrog.com fqdn us1.vpn.goldenfrog.com
set address us2.vpn.goldenfrog.com tag vyprvpn
set address us2.vpn.goldenfrog.com fqdn us2.vpn.goldenfrog.com
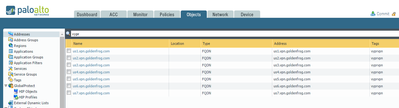
Lather, rinse, repeat for each of the server locations. When you're done it will start to look something like this:
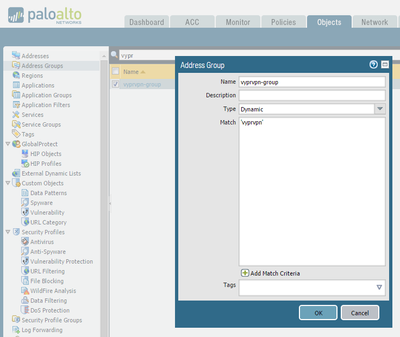
You're tagging each of these objects with a "vyprvpn" tag for a good reason. The above process will create one address object per server location. You then create an Address Group that includes all of the individual address objects tagged with 'vyprvpn' like this:
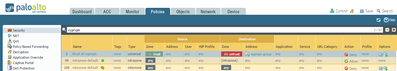
And finally, create a security policy that blocks traffic to 'vyprvpn-group' on any app and any port.
EDIT: I assumed that the VyprVPN server was hosted by goldenfrog.com in my above instructions. You may need to do something similar for VyprVPN through giganews, ie: us1.vpn.giganews.com, but the concept is the same.
Also, I did a couple of quick tests.. VyprVPN on iOS is detected as "ciscovpn" and "ipsec-esp-udp" from an AppID perspective. Block those Apps to shut this down on that platform. On Windows, the VyprVPN "Chameleon" protocol is detected as "unknown-udp" and can also be blocked. In my lab, blocking unknown-udp prevented VyprVPN from establishing a Chameleon VPN tunnel without worrying about destination IP addresses.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2016 08:58 AM - edited 01-22-2016 10:43 AM
While some of their VPN protocols are standards-based with corresponding AppIDs, I bet you're having problem with the "chameleon" variant.
If you can't block it by AppID, you should be able to tackle this via FQDN address objects. They've provided a complete list of their servers here:
- https://support.goldenfrog.com/hc/en-us/articles/203733723-What-are-the-VyprVPN-server-addresses-
The CLI will probably be the quickest way to get these entries in your firewall. Here's what the commands would look:
set address us1.vpn.goldenfrog.com tag vyprvpn
set address us1.vpn.goldenfrog.com fqdn us1.vpn.goldenfrog.com
set address us2.vpn.goldenfrog.com tag vyprvpn
set address us2.vpn.goldenfrog.com fqdn us2.vpn.goldenfrog.com
Lather, rinse, repeat for each of the server locations. When you're done it will start to look something like this:
You're tagging each of these objects with a "vyprvpn" tag for a good reason. The above process will create one address object per server location. You then create an Address Group that includes all of the individual address objects tagged with 'vyprvpn' like this:
And finally, create a security policy that blocks traffic to 'vyprvpn-group' on any app and any port.
EDIT: I assumed that the VyprVPN server was hosted by goldenfrog.com in my above instructions. You may need to do something similar for VyprVPN through giganews, ie: us1.vpn.giganews.com, but the concept is the same.
Also, I did a couple of quick tests.. VyprVPN on iOS is detected as "ciscovpn" and "ipsec-esp-udp" from an AppID perspective. Block those Apps to shut this down on that platform. On Windows, the VyprVPN "Chameleon" protocol is detected as "unknown-udp" and can also be blocked. In my lab, blocking unknown-udp prevented VyprVPN from establishing a Chameleon VPN tunnel without worrying about destination IP addresses.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2016 03:45 PM
@inzamam.shahid Ask and you shall receive. It appears "vyprvpn" is now a recognized application per content update 564.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2016 02:32 AM
I saw that today glad it got created it makes things much simpler!
- 1 accepted solution
- 8770 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!