- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
MS RDP via GlobalProtect is not working in some cases
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- MS RDP via GlobalProtect is not working in some cases
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2023 11:25 PM - edited 03-09-2023 11:50 PM
Hello all,
we need to allow to access different machines via MS RDP.
I write here which accesses work/not work to get an idea of our problem:
Location 1 -> S2S -> Location 2 -> RDP working
Location 1 -> S2S -> Location 2 -> S2S -> Location 3 - RDP working
GlobalProtect -> Location 1 -> S2S -> Location 2 -> RDP working
GlobalProtect -> Location 1 -> S2S -> Location 2 -> S2S -> Location 3 - RDP not working
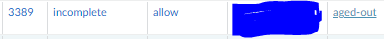
The only thing we see with the connection not working is that the TCP handshake is not working. It shows Application "incomplete". The firewall policies allow the traffic.
Test performed:
- client-side UDP disabled
- RDP NLA disabled
- Windows firewall disabled
It makes no difference.
Maybe someone here has an idea what else we could check.
Thanks,
Michael
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2023 04:48 AM
Hi @MichaelCL ,
Looking only at the session end reason and detected application will not give you the full picture of what is happening.
I strongly recommend to everyone when reviewing logs to always add the two columns - "Bytes Sent" and "Bytes Received"
By default log view include column Bytes, which is summary of sent and received traffic. When adding those two you can quickly identify if firewall receive return traffic.
In my experience incomplete is always explained with missing return traffic. Of course why there is no return could be cause by various reasons:
From the provided information it looks like Location 3 either does not have correct route for the GP pool or not allowing:
- Check the IPsec tunnel between Location 2 and Location 3. Is GP IP pool part of the encryption domain for IPsec phase2?
- Does Location 3 have correct route for GP IP pool pointing to tunnel to location 2?
- Any firewall rules in location 3?
- Any NAT being applied for the traffic over the tunnels?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2023 04:48 AM
Hi @MichaelCL ,
Looking only at the session end reason and detected application will not give you the full picture of what is happening.
I strongly recommend to everyone when reviewing logs to always add the two columns - "Bytes Sent" and "Bytes Received"
By default log view include column Bytes, which is summary of sent and received traffic. When adding those two you can quickly identify if firewall receive return traffic.
In my experience incomplete is always explained with missing return traffic. Of course why there is no return could be cause by various reasons:
From the provided information it looks like Location 3 either does not have correct route for the GP pool or not allowing:
- Check the IPsec tunnel between Location 2 and Location 3. Is GP IP pool part of the encryption domain for IPsec phase2?
- Does Location 3 have correct route for GP IP pool pointing to tunnel to location 2?
- Any firewall rules in location 3?
- Any NAT being applied for the traffic over the tunnels?
- 1 accepted solution
- 3939 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- A new comment has been added on a case [Case#: 03799775] - After upgrade serial number has change and HA is not working: New Serial : 007951000449149 in VM-Series in the Public Cloud
- Global Protect being interrupted by Copilot? in GlobalProtect Discussions
- VPN client failing with - Gateway DEV-VPN: Could not connect to gateway. The device or feature requires a GlobalProtect subscription license. in GlobalProtect Discussions
- Configure GlobalProtect to Facilitate Multi-Factor Authentication Notifications in GlobalProtect Discussions
- Redirecting from 3rd party auth provider back to GlobalProtect Clientless VPN application in GlobalProtect Discussions