- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SAML with ADFS and GP
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- SAML with ADFS and GP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SAML with ADFS and GP
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-17-2020 07:18 AM - edited 06-17-2020 07:29 AM
Hi Everyone
We are currently using GP with LDAP as an authentication method. This works like charm.
Now, we want to start using the AZURE MFA option that we have configured on our ADFS servers.
I’ve managed to setup the SAML between the ADFS servers (2016) and the palo alto but I can’t seem to get the VPN working.
I’ve followed this guide to setup the SAML authentication.
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/authentication/configure-saml-authenticati...
Unfortunately, after following this guide, it didn’t work. I didn’t get any assertation values. I then removed the certificate from the ADFS server in the relaying party trust.
Now I’m seeing the incoming claims but still no luck.
Then I found this article: https://www.reddit.com/r/paloaltonetworks/comments/8gsp9b/saml_sso_with_microsoft_adfs/
and this: https://live.paloaltonetworks.com/t5/general-topics/adfs-saml-configuration/td-p/144886/page/2
I added the 5 claims and set my user attributes.
Hooray I’m able to login to the portal now. However, if I try to login with the global protect client, I get the question to login to my ADFS but then the client hangs on connecting. If I check the authd log, I see that it uses a username consisting of letters and numbers.
Next step. I removed the all the claims and I’m now sending samaccountname as a claim and I changed the username attribute also to samaccountname on the palo alto.
I see the username name now in the authd log, but login does not work. The reason was that on the gateway, I configured to only allow only certain groups to be able to login to the gateway. If I set those users to any, the logon works!
The bad news is, now I’m unable to login to the portal.
I guess I’m having a problem setting the correct claims but I’m not sure to what exactely.
Anyone that has a similar setup that wants to share their configuration please? 😊
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-17-2020 06:59 PM
Hi,
Would it possible to pass the SAML attribute as domain\username? Where the domain will be the NetBIOS domain of your AD and username will be sAMAccountName
If you're connected to a root domain controller via LDAP, we should retrieve a domain-map for all the Parent and child domains configured in the environment. Below you will see the example from my domain.
You can check the domain-map with the following command:
> debug user-id dump domain-map
sus.sos.local : sus
vsys1 dc=sus,dc=sos,dc=local
sos.local : sos
vsys1 dc=sos,dc=local
Here my AD dns domain is 'sos.local' and Netbios domain is 'sos'
You can check the user-id database to see what attributes are being pulled and normalized by the firewall, using the following command
> show user user-attributes user all
An example would be:
Primary: sos\testuser1 Email: testuser1@sos.local
Alt User Names:
1) sos\testuser1
2) testuser1@sos.local
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 01:51 AM - edited 06-18-2020 01:52 AM
Hi
thank you for the reply!
I setup the settings again as in the reddit post above.
if I do:
> debug user-id dump domain-map
I get: wich is indeed our AD domain
my.domain.com : my
vsys1 dc=my,dc=domain,dc=com
if I do:
> show user user-attributes user all
Primary: global\test1
Alt User Names:
1) domainname2.com\test1
2) test1@domainname2.com
--> this is the user that I logged in with on the gp portal (with success)
if I check another user (one that I'm not testing with):
Primary: my\user2
Alt User Names:
1) my\user2
2) yuri.lupinov@domainname2.com
the thing is, we have the my.domain.com as our AD domain
but next to that, we have other domains the we use in our UPN
so user will logon with username@domainname2.com or username@domainname3.com depending on where they work.
so portal logon works.
if i want to connect with the gp client, it just hangs on connecting
authd last message is: find domain for auth profile: SAML; vsys vsys1
I also see:
Sent PAN_AUTH_SUCCESS SAML response:(authd_id: 6792859029119963731) (return username 'dh9FF4rL/1jWq/Pg+UoU6kqL10m3qVX8Qd5lEuZHq2w=') (auth profile 'SAML') (NameID 'dh9FF4rL/1jWq/Pg+UoU6kqL10m3qVX8Qd5lEuZHq2w=') (SessionIndex '_ca94283d-5144-49de-8602-31eccb617157') (Single Logout enabled? 'Yes')
so it's not sending me any domain\user info
I guess the next step would be to have the adfs send domain\user info?
any idea's on how to setup the claims then in ADFS?
I've tried testing with samaccountame, but it then send me test1,my\test1
so both versions while I was sending only 1 claim.
kind regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 11:57 AM
Thank you for the information.
So if you look at the authd logs it is picking the username from the Subject NameID, which tells me that no username attribute is being picked from the SAML response, so NameID is being used. Below is an example where no username attribute returns, so the Subject Name ID is being used.
2020-06-17 19:19:32.817 -0700 debug: _parse_sso_response(pan_authd_saml.c:1037): SAML SSO response from "http://www.okta.com/exk3ot73ubmw1MhEn357" has no username attribute
2020-06-17 19:19:32.817 -0700 debug: _parse_sso_response(pan_authd_saml.c:1040): SAML SSO response from "http://www.okta.com/exk3ot73ubmw1MhEn357": Use saml:Subject NameID "sahmed@sos.local" as username
In your case, the same thing is occurring, but Subject NameID format is most likely transient, hence it has a randomly generated username and the username attribute is not being picked.
Sent PAN_AUTH_SUCCESS SAML response:(authd_id: 6792859029119963731) (return username 'dh9FF4rL/1jWq/Pg+UoU6kqL10m3qVX8Qd5lEuZHq2w=') (auth profile 'SAML') (NameID 'dh9FF4rL/1jWq/Pg+UoU6kqL10m3qVX8Qd5lEuZHq2w=') (SessionIndex '_ca94283d-5144-49de-8602-31eccb617157') (Single Logout enabled? 'Yes')
What is the username attribute configured in the authentication profile? the default should be the "username"
I would suggest installing the SAML Devl Tool for chrome and then authenticating to the Portal via the browser to analyze the SAML response and checking to see what attributes are returned from your idP. See the KB link for SAML intro and where you download the SAML DevTools
SAML DevTools Extension
https://chrome.google.com/webstore/detail/saml-devtools-extension/jndllhgbinhiiddokbeoeepbppdnhhio?h...
Introduction to SAML:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVvCAK
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2020 12:33 AM - edited 06-24-2020 02:31 AM
Hi
just wanted to update that I'm doing some more testing, so for it's either portal or gateway that's working, not both 🙂
I'll post the solution when I've found it
kind regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-02-2020 04:21 AM
Hi all
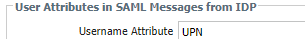
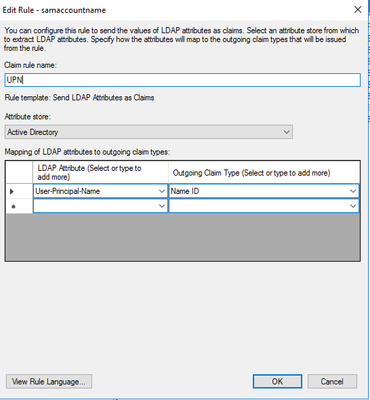
this is how we got it to work:
Thank you Sakhan for the help!
good luck
Roel
- 12919 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- User ID mapping works on DC but not/intermittent on branches for Intune internal users. in GlobalProtect Discussions
- global protect connection failed authentication failed !!! in GlobalProtect Discussions
- GlobalProtect Cert+SAML in GlobalProtect Discussions
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions