- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Add Vm 100 palo alto machin (dr site) to a Panorama to the same device group and template (main Site)
- LIVEcommunity
- Tools
- Integration Resources
- Integration Discussions
- Add Vm 100 palo alto machin (dr site) to a Panorama to the same device group and template (main Site)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Add Vm 100 palo alto machin (dr site) to a Panorama to the same device group and template (main Site)
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2021 04:59 AM
hey
so i have main site and dr site and they are connected in L2
i have in the main site 2 physical pa3220 that there are in cluster (active, passive) and they connected to Panorama and they work perfect
now i need to add the Palo Vm 100 machine that is in the dr site but i want that in the end every change that i will do in the main site
like add policy , add object, add Nat, add route and etc. will replicate to the dr site cause it "cold dr site"
how can i do it?
my problem here cause is 2 different model of machine and the interface are different
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 03:13 PM
Thank you for posting question @DinBarzilay
Since you have written you are facing an issue with interfaces, I will focus on Panorama Templates.
One way I can think of to go around this issue is to create 2 hierarchy of Templates. For example templates based on model of the Firewall:
template_pa3220
template_vm100
Then in each template you configure only interfaces that are exactly matching model of the Firewall. You can also add any other configuration that falls under Network/Device and is specific to particular model of Firewall.
then define one Template that has all other settings. For example:
template_global-configuration
In this template you can configure everything but interfaces.
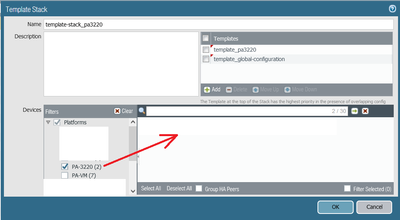
Then group Templates in Template Stack by placing template with interface specific configuration on the top. For example:
template_pa3220
template_global-configuration
template-stack_pa3220
template_vm100
template_global-configuration
template-stack-vm100
and associate each of the firewall to particular Template Stack.
Since interface configuration is likely one time task and you can re-use interface specific Template for new Firewalls, you will not have to re-visit this Template anymore. All the configurations that are meant to be pushed to all Firewalls will be done in this Template: template_global-configuration. By placing template that configures interfaces on the top in template stack, will have highest preference.
Below are a few screens for reference:
If you design Templates in this modular way, you will not lock yourself into an issue when you add yet another model of Firewall. There are possibly other ways around it. Please let me know whether this would work for you or not.
When it comes to Device Group, I am not aware of any configuration that falls under Device Group (Policies and Objects) and has dependencies on Firewall model. Also, all configuration under Device Group (Policies and Objects) except of a few setting has dependency on Templates.
I hope this helps.
Kind Regards
Pavel
- 2398 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!