- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Twilio
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-08-2017 10:59 AM - edited 08-08-2017 01:49 PM
Disclaimer
This document is intended as an easy example on how to leverage action oriented and selective log forwarding in PAN-OS 8.0, not as a comprehensive solution document.
Goal
In this document I’ll summarize the information and relevant steps to integrate Palo Alto Networks Next Generation Firewalls with Twilio to send SMS mssages based on something detected by the firewall (use of an application, access to a honeypot, C&C, vulnerability exploits, etc).
Action‐Oriented Log Forwarding using HTTP
To enable better integration between your firewall and IT infrastructure, PAN‐OS 8.0 gives you the ability to trigger an action or initiate a workflow to an external HTTP‐based service, when a log is generated on the firewall. You can now forward logs from the firewall or Panorama to an HTTP(S) destination to accomplish the following task more easily.
Send an HTTP‐based API request directly to a third‐party service to trigger an action based on the attributes in a firewall log. You can configure the firewall to work with any HTTP‐based service that exposes an API, and modify the URL, HTTP header, parameters, and the payload in the HTTP request to meet your integration needs. This capability when used with the Selective Log Forwarding Based on Log Attributes allows you to forward logs that match a defined criteria so that you can automate a workflow or an action; you do not need to rely on an external system to convert syslog messages or SNMP traps to an HTTP request.
Getting Started with Twilio
Twilio allows you to add capabilities like voice, video and messaging to our applications. Through a native REST API, Twilio can send messages that we generate from our firewall to network adminstrators.
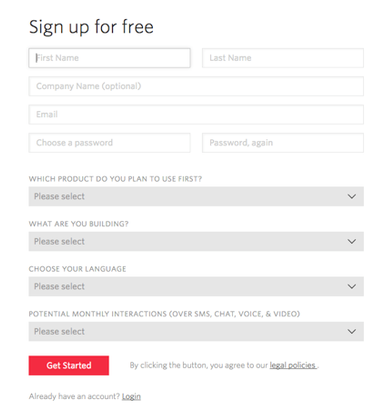
First, sign up with an account on twilio.com.
Under “Which product do you plan to use first?” choose SMS.
Under “Choose your language” choose Python.
Under “What are you building?” choose IT Service Alerts.
Under monthly interactions choose “Not a production app”.
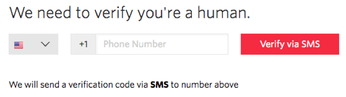
Once you have completed the signup page, Twilio will now prompt you to enter your phone number. Make sure this is a number that can receive text messages.
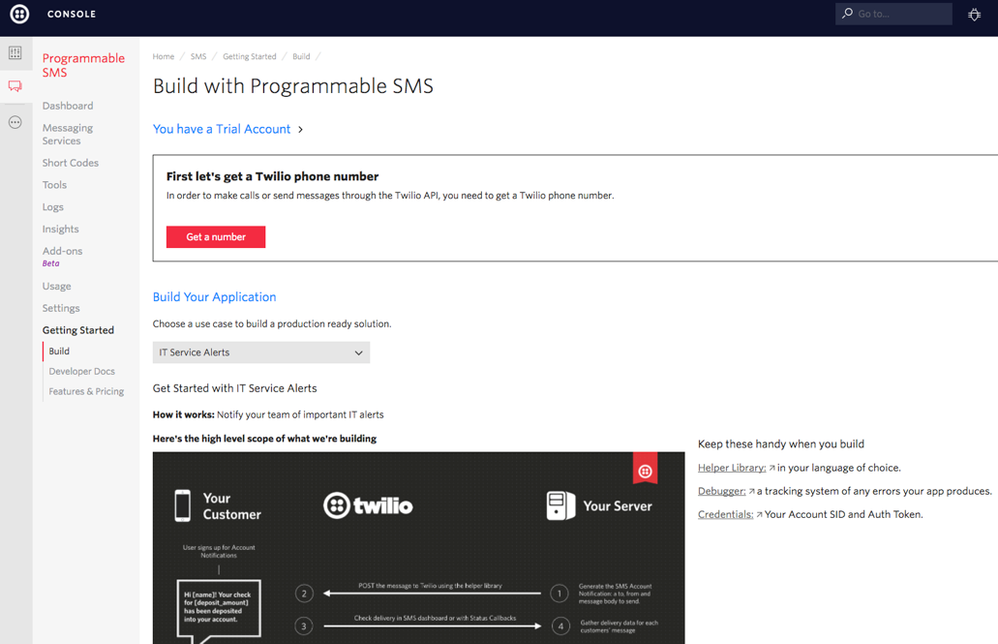
Once you have completed the sign-up, your screen should now look like this.
Select “Get a number” or if that’s not available, go to this URL: https://www.twilio.com/console/phone-numbers/trial-number/modal?capability[]=sms
Twilio will suggest a number for you, if you don’t like it, click “Search for a different number”.
Once you have your number, note it down. In this guide, I’ll be using my number +16693337828, but whenever you see that number replace it with yours.
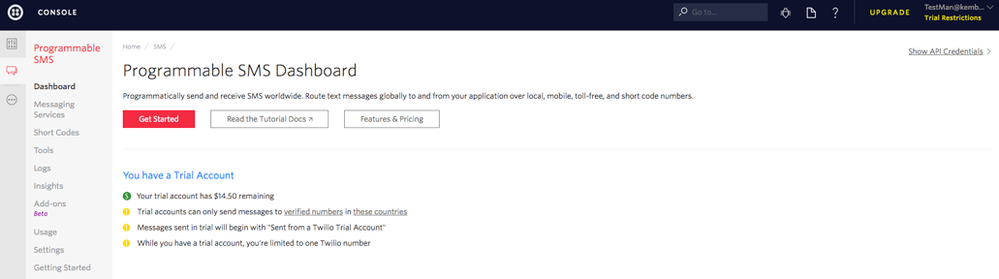
Note that Twilio starts you off with a trial account with $14.50 in credit. While you are on a trial account, Twiio can only send messages to numbers verified on Twilio. In addition, Twilio prepends all messages sent by trial accounts with “Sent from your Twilio trial account - ”.
In your twilio console, navigate to the dashboard (https://www.twilio.com/console/sms/dashboard). Here’s how mine looks:
If you can’t see your API credentials don’t worry! On the top right, below the black bar, click “Show API Credentials”.
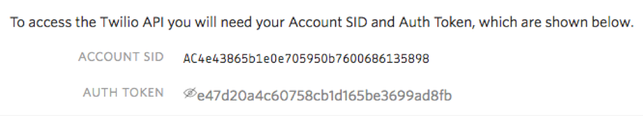
Click the eye to unhide your Auth Token. Now your console should display both your SID and your Auth Token, here’s how mine looks.
Note both of these down. By now you should have stored your Account SID, Auth Token, and Twilio Phone Number somewhere safe.
Palo Alto Networks Next Generation Firewall Configuration Steps
- Follow the firewall quick start guide to get a working environment where traffic from users is traversing the firewall and logs are being generated.
- Create a HTTP Server Profile, use address “api.twilio.com”, protocol “HTTPS”, port “443” and HTTP Method “POST”. Use your account sid and auth token for username and password respectively. Test Server Connection should return “https://api.twilio.com:443 succeeded”.
- Define the payload format for whichever logs you’d like to forward. I want to forward threat logs to Twilio so, I’ll just edit the Threat Log Payload.
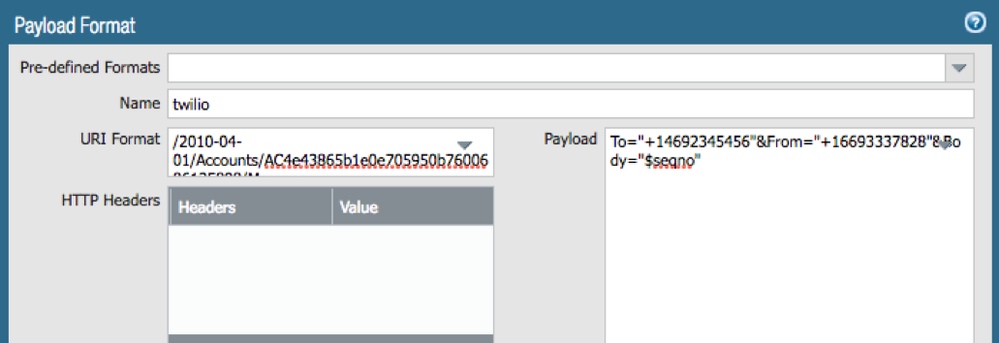
In URI format, copy and paste the following string “/2010-04-01/Accounts/{YOUR SID}/Messages”, except where it says YOUR SID, post the SID you got from Twilio before. For example, my SID was “AC4e43865b1e0e705950b7600686135898” so my URL becomes:
/2010-04-01/Accounts/AC4e43865b1e0e705950b7600686135898/Messages
Next, in Payload, copy and paste:
To="YOUR NUMBER"&From="TWILIO NUMBER"&Body=”Body Format Here"
except replace YOUR NUMBER with your personal number and TWILIO NUMBER with the number Twilio gave you. Note that you must prepond the numbers with +1, otherwise this won’t work. In the body, you can choose what you want Twilio to send, here I just want to send the sequence number of the log. Here’s how my completed Payload looks like:
To="+14692345456"&From="+16693337828"&Body="$seqno"
Here are some payload formats you can use for each log type:
Note: Change the {RECEIVER} with your phone number(prepend 1), ex: +14669134345 Change the {TWILIO#} with your twilio number(prepend 1), ex: +15421341368
System
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated $severity $module $opaque”
Threat
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated $severity $threatid $thr_category From: $src $srcuser To:$dst"
Traffic:
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated From: $src $srcuser To: $dst $app"
URL
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated $category $url_idx From $src $srcuser To: $dst $dstuser with $app"
Data
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated $category $filedigest $filetype From: $src $srcuser To:$dst $app"
Wildfire
To=“{RECEIVER}”&From=“{TWILIO#}”&Body="$time_generated $severity $action $filedigest From:$src To:$dst $dstuser thru: $app"
Once this is all finished, click ok and commit this to panorama. Once it’s finished committing, go back to the HTTP profile you created, select the log type you were just editing in Payload Format. Your URI and payload should pop up. Click “Send Test Log”. If everything was set up correctly, you can expect a text message on your phone!
Now you can create a Log Forwarding Profile with a match list and select the HTTP server profile(in my case “Twilio”) created earlier.
Create a filter and assign it to the Log Forwarding Profile. I used a URL match to simplify the testing. Once it is working you can define an appropriate filter to match what is required on your environment.
Apply the log forwarding profile to the rule/s you want.
- 9333 Views
- 0 comments
- 0 Likes
-
Automation
1 -
HTTP
2 -
ifttt
1 -
Log Forwarding
4 -
NGFW Configuration
1 -
notifications
1 -
PAN-OS
2 -
Panorama Configuration
1 -
slack
1 -
twilio
1