- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cobalt Strike Potential Command and Control Traffic(18927)
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Cobalt Strike Potential Command and Control Traffic(18927)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2019 04:07 AM
Anyone seeing this new signature as FP prone?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2019 06:10 AM
This has been fixed by removing the signature for "Cobalt Strike Potential Command and Control Traffic (18927)" in content version 1840 due to the reason it creates lot of false positives and Paloalto decided to rework on this signature
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2019 10:58 AM
We haven't seen any reported at this point.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2019 03:50 PM - edited 03-28-2019 03:51 PM
The signature is meant to detect an empty space in "HTTP/1.1 200 OK " (right after the OK) in HTTP responses, which may indicate a connection with a NanoHTTPD server, which is 'typically' used in Cobalt Strike's team server.
If you see other HTTPD implementations inserting the "extraneous space", do let us know.
More information available at:
https://blog.fox-it.com/2019/02/26/identifying-cobalt-strike-team-servers-in-the-wild/
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2019 04:00 PM
Hi, yes, I guessed that might be what you defined the signature for.
We are seeing hits on this, obviously hoping that it’s a false positive.....
It seems to be triggering on valid websites as far as we can tell, and it’s not just one, so either there are a lot of compromised commercial websites or it’s too sensitive. I can provide the packet captures as necessary.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2019 06:09 PM
As a FYI here are three domains we're seeing hits on:-
Rgds
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2019 08:40 AM
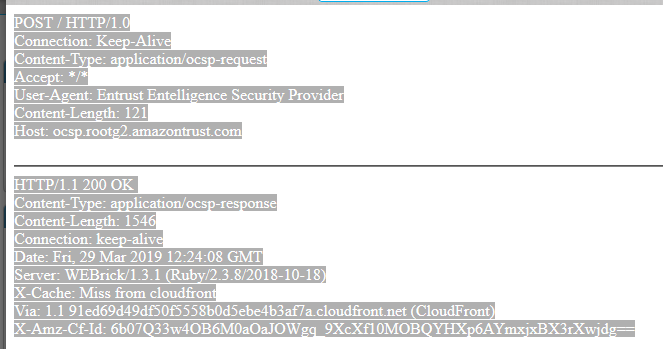
We are seeing what we think are false postives with this signature. We see lots of OCSP traffic from Amazon and others that has space after the 200 OK.
POST / HTTP/1.0
Connection: Keep-Alive
Content-Type: application/ocsp-request
Accept: */*
User-Agent: Entrust Entelligence Security Provider
Content-Length: 121
Host: ocsp.rootg2.amazontrust.com
0w0u.....0N0L0J0...+.......}.D^g.|.wNC..>...s...._.....0+8...mJ..........J*'.....+.........0.0.. +.....0...
0.. +.....0..HTTP/1.1 200 OK
Content-Type: application/ocsp-response
Content-Length: 1546
Connection: keep-alive
Date: Fri, 29 Mar 2019 09:56:06 GMT
Server: WEBrick/1.3.1 (Ruby/2.3.8/2018-10-18)
X-Cache: Miss from cloudfront
Via: 1.1 048de604b26de968a1aa2fe5dd1a0085.cloudfront.net (CloudFront)
X-Amz-Cf-Id: xuBEvyqfYSM9Hr0TcWIUJ-CL-n_a8enx3EmVPtId3MItOJgncm_6ew==
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-31-2019 11:48 PM
We are also see ing lots of hits for this signature on ocsp.rootca1.amazontrust.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-01-2019 08:56 AM - edited 04-02-2019 02:15 AM
Hello community,
We have also the same threats traffic detected on our Palo devices and watching to the traffic itself it seems to be ocsp traffic on serveral legitimate servers around amazon, cloudfront...
Can we safely consider this traffic as false positive detection?
Thank you in advance,
Guillaume
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-01-2019 09:32 AM - edited 04-01-2019 09:42 AM
I believe that's the reason why this was named "Potential" with "informational" severity. Its definition hints you that the signature is lose enough to be FP prone.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2019 08:09 AM
Here's a few domains that have been triggering the FP for us:
store.moma.org
www.saucony.com
www.bcbg.com
The common denominator seems to be shopping (apparently all our users do) and that all the IPs are hosted on Cloudflare.
Thanks,
- Steve
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2019 06:10 AM
This has been fixed by removing the signature for "Cobalt Strike Potential Command and Control Traffic (18927)" in content version 1840 due to the reason it creates lot of false positives and Paloalto decided to rework on this signature
- 1 accepted solution
- 24459 Views
- 10 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions
- Threat ID: 31671 - SCADA ICCP Unauthorized COTP Connection Established in Advanced Threat Prevention Discussions
- Threat ID 31671 - SCADA ICCP Unauthorized COTP Connection Established in Advanced Threat Prevention Discussions
- critical control points in Advanced Threat Prevention Discussions
- Translate Suricata IPS signatures into custom Palo Alto Networks threat signatures in Advanced Threat Prevention Discussions