- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to block Crypto Miner (javascript)
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: How to block Crypto Miner (javascript)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2017 05:54 AM
This week I noticed a "CoinHive Javascript Detection" in the logs of our Palo Alto.
When reading on the subject I noticed that there are websites around that use Javascript to start mining Crypto coins on the users' computer.
Detailed description can be found here :
https://researchcenter.paloaltonetworks.com/2017/10/unit42-unauthorized-coin-mining-browser/
I noticed in the Palo Alto blog that : PANDB is able to block URLs hosting Coinhive JavaScript.
My question:
How does one actually block this?
When I visit for example https://coinhive.com/ and push the button "Start Mining" the CPU goes up to 100%.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 07:24 AM
Also found the solution how to decrypt a site that is in a category that should not be decrypted.
Problem solved.
The Crypto sites are now succesfully blocked.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 02:44 AM
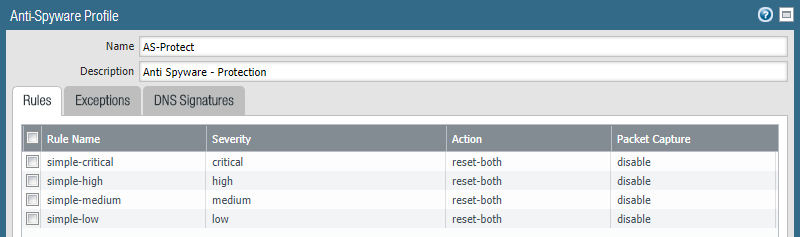
I have found how to block this in the AntiSpyware profile.
It appears that for many of the AntiSpyware actions the default setting is alert. Even for some of the critical ones.
Not sure why this is but I will play around with the settings to see if this can be set to block.
Unfortunately there is an additional challange.
This site is SSL encrypted and although there is SSL decryption enabled on the firewall, the site itself is classified as "Financial Services" which is excluded from SSL decryption due to regulations.
So if I find the solution on how to decrypt the site, I should be able to block this.
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 07:24 AM
Also found the solution how to decrypt a site that is in a category that should not be decrypted.
Problem solved.
The Crypto sites are now succesfully blocked.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-11-2017 05:12 AM
so do you block it by your spyware filters or it is blocked by PANDB filter?
because to me it is still unclear how Palo blocks it (if it does)
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-12-2017 02:18 AM
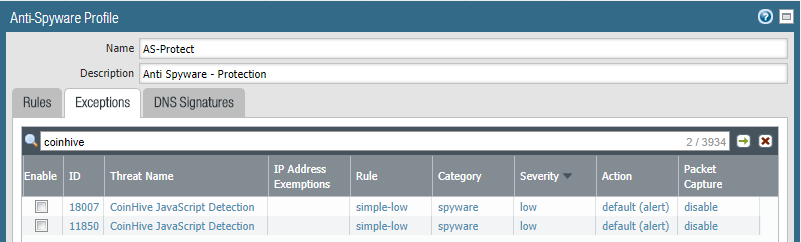
It is part of the Anti Spyware module.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-29-2017 11:13 AM
Thank you!
I'm really surprised this is classified as low severity? This can get onto servers and spike CPU to 100% to take down applications.
Also, I don't think these mining websites should be listed as
Category Financial Services
Auctions?? coinhive malware was going around injecting user's PCs......
Category Auctions
Category Computer and Internet Info
Category Malware
They're saying minexmr.com is malware because it was recently used in a malware mining injection incident, however couldn't you use any miner website with the injection?
Needs to be a new URL PAN-DB category for Cryptocurrency, in my opinon.
Clean this up PAN, this is going to be one of the biggest issues in 2018 against networks in my opinion. Make this a priority.
Thanks, -Rags
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2018 01:45 PM
I feel that the Palo Alto Networks response to crypto jacking is disappointing. There is a security reaseacher that is actively tracking cryptomining domains and (as of now) is maintaining up-to-date lists of these domains. You can add the first two lists "all domains" and "all optional domains" to an External Dynamic List and then edit your exsiting Anti-Spyware policies to sinkhole those domains. As of this post, there are 3,898 domains in those two lists (combined).
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2018 08:19 PM
I see the two CoinHive signatures have have had their severity increased to medium which is set to reset-both in our environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 07:21 AM
Thanks @kalakai for the links. Good stuff.
What is the advantage over using a sinkhole over just using a DBL and setting the rule to block completely?
Thanks, -Rags
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 10:27 AM
Sinkhole is meant to discover infected hosts when the only thing the firewall sees is queries sourced from an internal DNS server. (Internal DNS server obscuring real source IP's of hosts querying for malicious domains). The idea is that infected hosts may carry out a subsequent connection after resolving a malicious domain, and these will initiate new traffic to the *sinkhole ip* - therefore you would use the traffic logs to see which hosts are attempting to initiate traffic to the *sinkhole ip* (and discover which hosts are infected).
If that's not your topology, then it's better to block.
By the way, you can also set an EDL of type Domain to action 'sinkhole' in the Anti-Spyware profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 12:43 PM
It is my understanding that you cannot use a "Domain" type EDL in a security policy as there is no way to select it. Domain type EDL's only show up in anti-spyware DNS Signature settings. Upon double checking all the lists that are available on the link I provided earlier, I do see an IP list, which can be used in a security policy; so you can directly block that way in addition to sinkholing.
- 1 accepted solution
- 39342 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!