- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Sliver Framework Command and Control Traffic Detection - ThreatID 86680
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Sliver Framework Command and Control Traffic Detection - ThreatID 86680
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Sliver Framework Command and Control Traffic Detection - ThreatID 86680
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2023 03:49 AM
Hi all,
has anyone see this critical threat which is correlated in our environment with google mail?
This event started with content-8770-8365.
I can see that PaloAlto did some changes in Modified Anti-Spyware Signatures in release notes.
It simply breaks gmail web-based email client.
I attach example pcap file.
I assume it is a false-positive, but ...
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2023 06:03 PM
Palo Alto Networks is currently working on the false positive issue with the signature (Threat ID: 86680).
Please monitor the content release notes and look for the signature update.
Please create a threat exception in the meantime as needed.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/threat-prevention/create-threat-exceptions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2023 07:33 AM - edited 10-27-2023 07:34 AM
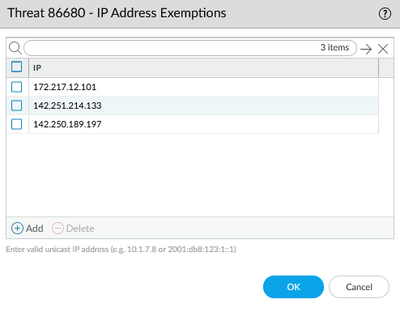
Same here. I have added IP exceptions as @ymiyashita stated. So far, I have only had to make an exception for three IPs.
172.217.12.101
142.251.214.133
142.250.189.197
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2023 07:56 AM
Hi, IPs exception and The Treat ID is OK but it's highly depended on the area where you came from.
Especially in terms of Google's cloud.
I am personally waiting for PA's the new "Application and Threats" version.
I hope they will find solution and we wouldn't have to do exceptions by ourself.
Cheers,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2023 03:01 PM
I'm also seeing this, and am about to create a support case. Hopefully it gets resolved in the next App and Threat update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 12:06 AM
How do you know PA is working on it?
Still no progress. New definition has ben deployed last night but broblem still exist.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 06:38 AM - edited 10-31-2023 06:39 AM
Looks like App&Threats 8773 was released, but nothing in the release notes about 86680. I did an exception for this, but can't change the severity from Critical, and we have a rule that sends emails on all Critical events, so our emails are getting blasted with this false positive. Is there a case ID about this so I can enter a case and tag it, so they know about how this is affecting others? I'm also going to loop in our SE.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 08:09 AM
@MarcinWSTD - would you be able to share your Case number? I reached out to our SE and this would be helpful in escalating this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 01:52 PM
Raising a support case assumes they are working on it, although I haven't heard much back on mine. Out of interest, what version of PAN-OS are you all on? I'm on 11.01-h2 and am wondering if it is only affecting a smaller number of customers because of a specific PAN-OS version. Otherwise there would be more activity on this community discussion.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 02:20 PM
We are using 11.0.2-h1. The low number of customers reporting this issue may also be due to the Trusted Traffic to Google policy being configured in the firewall.
We only see this behavior when traffic to Google is processed through SSL interception. When the traffic is defined as trusted (undecrypted), the firewall is silent about this ThreatID 86680. I'm not an expert, but I think the definition of a threat depends on the characteristics of the network packets. So I can't imagine that different wersion of OS could detect this traffic in different ways, especially from the same manufacturer.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 06:12 PM
I just received the email for Content Update Version 8774, and it makes mention of this specific issue. I've downloaded and installed the update but am still seeing the false positives in my threat log.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 06:12 PM
The fix was released in content version 8774.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 06:23 PM
Oh, if you are still seeing the issue with content 8774, please kindly open a support case and report the issue to get it fixed..
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2023 07:24 PM
Actually, it looks like it has fixed. It just took a while to take effect.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2023 05:49 AM
11.0.2-h2 here. We're on 1410's which only support 11.x and greater. We decrypt everything thats possible.
- 16509 Views
- 16 replies
- 3 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Network in Advanced Threat Prevention Discussions
- Spyware Detections in Advanced Threat Prevention Discussions
- Sliver Framework Command and Control Traffic Detection - ThreatID 86680 in Advanced Threat Prevention Discussions
- ThreatID 81845 - Generic PHP Webshell File Detection false positives in Advanced Threat Prevention Discussions