- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PAN-VM x-forwarded-for feature question in gcp cloud
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: PAN-VM x-forwarded-for feature question in gcp cloud
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2021 11:25 PM
Hello.
I have built a simple sandwich structure test environment on GCP Cloud.
ALB
↙ ↘
FW1 FW2
↘ ↙
NLB
↙ ↘
SV1 SV2
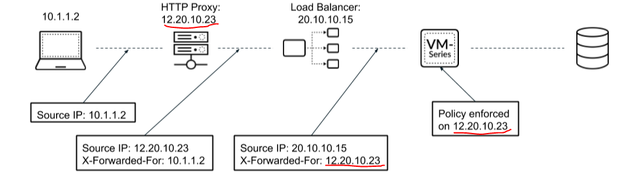
However, in the PAN traffic log, XFF IP is only the IP of the upper ALB.
GCP's official documentation confirmed that the XFF header contains both the client IP and the LB IP.
I actually did a packet capture from the PAN, both IPs are in the XFF header.
Below is a capture of only the XFF part of the captured packet.
(By capturing the packet, both the real client IP and the ALB IP can be checked.)
Below is the XFF IP seen by the PAN.
Only the IP of the ALB that is checked in packet capture is recorded in the log.
The detailed log only checks the IP of the ALB.
The point is, if the XFF IP is simply an ALB IP in the PAN traffic log, then the XFF function doesn't seem to have any meaning.
Is there any way to see in the log the client IP and not the ALB IP?
Or am I doing something wrong?
Please help me...
Regards,
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2021 08:49 PM
Hi @ttak87,
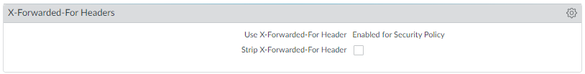
There are a couple of options around XFF in PAN-OS:
- If the requirement is to enforce security on XFF IP, the option you are currently using is the right one. However, with this PAN-OS feature, the policy enforcement and the corresponding logs will apply only to the last IP in the XFF list. In GCP, ALB inserts the source IP of the packet received followed by the ALB's IP. So the last IP in this case always happens to be ALB IP. So, unfortunately in GCP's ALB case, this feature is limited in its application.
- If the requirement is only to log the original client IP (and not policy enforcement), then another option is to use the attached PAN-OS feature. With this feature though, the 'first' IP address in the XFF list is logged in the URL filtering logs. If the packet traverses multiple proxies on the path, there could be multiple IP addresses (comma separated) in the XFF header. And this feature will use the first IP address in the list to add to the URL filtering log.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2021 05:14 AM
Hi @ttak87
You need to do settings on firewall to enable these logs. Its not enabled by default on Palo Alto.
Kindly refer below article.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClIVCA0
Hope it helps!
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2021 06:29 PM
Hi, @SutareMayur
Thanks for your reply.
However, I have already set the settings you taught me.
I want to check the Client IP and not the ALB IP in the log.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2021 10:35 PM
Hi @ttak87
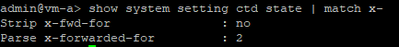
Could you please share PA o/p of below cli command -
show system setting ctd state | match x-
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2021 06:18 PM
Additionally, I looked at Palo Alto's document, and it seems that only the LB's IP is checked for the XFF IP in the proxy type LB.
If so, I think that GCP is limited in practically using XFF when using ALB.
Am I right?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2021 08:03 PM
The issue is that the firewall is using the last IP in the list and not the first. Please open a TAC case to push the fix through to engineering.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2021 08:49 PM
Hi @ttak87,
There are a couple of options around XFF in PAN-OS:
- If the requirement is to enforce security on XFF IP, the option you are currently using is the right one. However, with this PAN-OS feature, the policy enforcement and the corresponding logs will apply only to the last IP in the XFF list. In GCP, ALB inserts the source IP of the packet received followed by the ALB's IP. So the last IP in this case always happens to be ALB IP. So, unfortunately in GCP's ALB case, this feature is limited in its application.
- If the requirement is only to log the original client IP (and not policy enforcement), then another option is to use the attached PAN-OS feature. With this feature though, the 'first' IP address in the XFF list is logged in the URL filtering logs. If the packet traverses multiple proxies on the path, there could be multiple IP addresses (comma separated) in the XFF header. And this feature will use the first IP address in the list to add to the URL filtering log.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2021 10:17 PM
I understood the content.
Be able to explain well to customers.
Thanks everyone for the replies. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2023 11:03 PM
We Enabled for User-ID, still we are not receiving client real ip address.
- 1 accepted solution
- 10165 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- How to create a support case without a TCF file in Next-Generation Firewall Discussions
- How to Patch Vulnerability - Plugin 43160 (CGI Generic SQL Injection) on GlobalProtect in Next-Generation Firewall Discussions
- Question on "default" VLAN Interface in Next-Generation Firewall Discussions
- Performance impact of using higher DH group for site-to-site VPNs in Next-Generation Firewall Discussions
- SCM Essentials Questions in Strata Cloud Manager