
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
See what's new in Traps 6.0 and how these newly released features can help improve your security posture. New updates include Behavioral Threat Protection, Rich Data Collection for Cortex XDR, Response Actions, Traps for Linux Containers, and Malware Protection for Linux. Get your questions answered in the Live Community.
Introducing Traps 6.0
Traps has continually focused on protecting endpoints by looking at the behavior and techniques of threats used to attack and compromise endpoints. We have continued that theme in Traps releases over the past two years.
By introducing features such as the Kernel exploit prevention module, Child Process Protection module, and the ransomware protection module, Traps has been able to increase its prevention-first position. These features have helped stave off attacks from threats like WannaCry, Petya, NotPetya and many more without the need for signatures or prior knowledge of the threat.
As the threat landscape continues to evolve, we are seeing attacks become more sophisticated and evasive by leveraging OS capabilities and administrative tools, making these attacks difficult to detect and identify. The latest release of Traps extends the protection capabilities to protect endpoints across the most complete spectrum of threats. Below are highlights of these new features.
Features Introduced in Traps 6.0
Behavioral Threat Protection detects and stops attack activity by monitoring for malicious sequences across processes and terminating attacks when detected. When Traps detects these malicious events, it will present the timeline of actions taken in the event analysis tab in the Traps management console (See Figure 1).

Rich Data Collection for Cortex XDR™
To accelerate threat investigation and incident response, Traps can now collect detailed information about all active process, network, file, and registry activity on an endpoint. From the Cortex XDR app, you can view the activity details collected by Traps to understand the event context and gain insight on the event scope (See Figure 2). This includes all activities that took place during an attack, the endpoints that were involved and the damage.
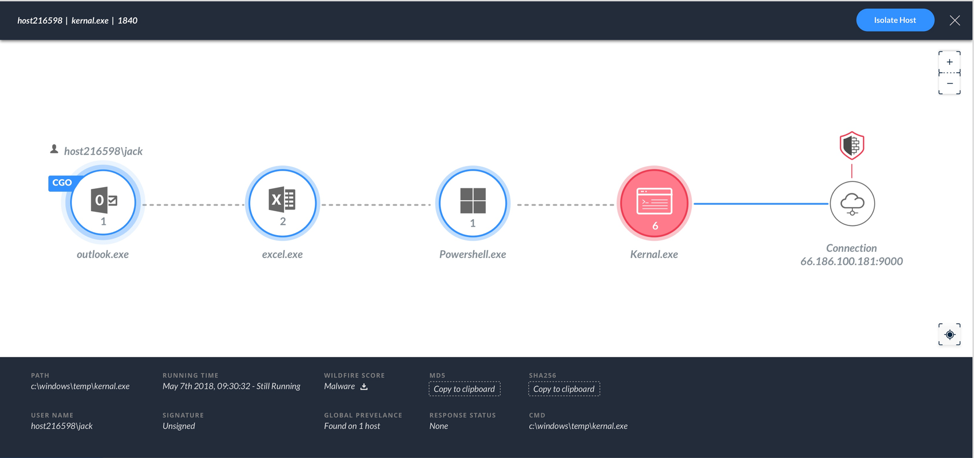
Response Actions
Traps uses the Cortex Data Lake to store all event and incident data captured, allowing a clean handoff to Cortex XDR for further investigation and incident response. Cortex XDR cloud-based detection and response is an app that empowers SecOps to stop sophisticated attacks and adapt defenses in real time. By combining rich network, endpoint and cloud data with analytics, Cortex XDR detects highly evasive attacks. Following an investigation, when remediation on the endpoint is needed, administrators have the option to do the following:
Traps for Linux Containers
Traps now extends Linux exploit and malware protection to processes that run in Linux containers. When you install Traps on a Linux server, Traps automatically protects any new and existing containerized processes regardless of the container solution (e.g., docker). Because the Traps management service issues the license per Linux server, each container does not consume any additional licenses (See Figure 3). For more information on Traps for Linux, see TRAPS AGENT 6.0 FOR LINUX.

Malware Protection for Linux
Traps can now prevent known and unknown malware from running on Linux servers by leveraging WildFire threat intelligence and local analysis to analyze ELF files. When an ELF file is executed on the host server or within a container on the Traps-protected-host, Traps automatically suspends the execution until a WildFire or local analysis verdict is obtained. When the verdict is malware, Traps prevents the process execution and reports the event to the Traps management service. If the ELF file is unknown to WildFire, Traps can also upload it to WildFire for further analysis. The number of malicious ELF files submitted to WildFire continues to grow as seen by the AutoFocus report below (See Figure 4).

See also:
For more information on these and other new features in Traps 6.0, please visit the Traps Documentation Page
Thanks for reading our blogs! Don't forget to Like (Thumbs Up) if you like this content, and, as always, we welcome all comments and questions below in the Comments section.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 4 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 7 | |
| 4 | |
| 2 | |
| 2 | |
| 2 |




