- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Policy Rules for BFD, OSPF , DHCP and DHCP relay
- LIVEcommunity
- Discussions
- General Topics
- Policy Rules for BFD, OSPF , DHCP and DHCP relay
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Policy Rules for BFD, OSPF , DHCP and DHCP relay
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2018 09:46 PM
Hi
So do I have to setup policy rules to allow OSPF, I have OSPF on the PA . But when i don't have the rules in place OSPF fails, when i have them it doesn't log anything
DHCP, do I need it if the PA is running DHCP. what is the source and destination ?
DHCP-relay, source is the input zone and the destination is the dhcp server I am relaying to. But it looks like I have to have 2 polies 1 for request and 1 for replies
BGP, is it the same i policy rules in place even if its that PA ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2018 08:36 AM
Hello,
I'll do my best here:
So do I have to setup policy rules to allow OSPF, I have OSPF on the PA . But when i don't have the rules in place OSPF fails, when i have them it doesn't log anything
Do you have logging enabled on the policy?
DHCP, do I need it if the PA is running DHCP. what is the source and destination ?
If you are using the builtin 'Intrazone' policy, then no. If you are like some and have a DENY ALL policy above those predefined policies, then possibly.
DHCP-relay, source is the input zone and the destination is the dhcp server I am relaying to. But it looks like I have to have 2 polies 1 for request and 1 for replies
Correct, this is how DHCP works since its not a tcp conection and the traffic gets generated both ways. ie the Clients send traffic to request and IP, the DHCP server then sends traffic with the IP info. This should not be required if the client and server are in the same zone.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2018 05:51 PM
Yep I have my own intrazone drop rule
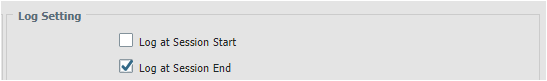
Yes I have logging on OSPF policy start and end
I don't see anything nor in monitor session
dhcp/dhcprelay .... so my issue with this is ... it supposed to be a new firewall with smarts. it should be expecting a reply..
🙂
So I know on my old cisco's once for example once I turned on snmp service i didn't need to allow access via acl it just worked.
Thanks
- 1593 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Insufficient data but still allowed the returning traffic to pass in Next-Generation Firewall Discussions
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions
- Panorama REST API policy creation error with ' 'message': 'Invalid Body', in Panorama Discussions
- Query related to import export config in General Topics
- Should I override the intrazone-default to deny? in Next-Generation Firewall Discussions