
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

Palo Alto Networks dives into Cortex XSOAR to explain how you can auto-respond to insider threats with speed and scale using Cortex XSOAR and Code42 Integration. Find answers on LIVEcommunity.
Data exfiltration activities by malicious insiders have dramatically grown to become a major risk factor for organizations across the world, as they enforce remote work to maintain business continuity during the COVID-19 shutdown and its aftermath. High-value data that is often put at risk results in huge losses for victim organizations.
Data exfiltration activities either accidental, deliberate, or as a result of cybersecurity breaches require heightened attention by the SecOps teams, which means swift response measures along with incident context and evidence readily made available to the investigation team.
Palo Alto Networks Cortex XSOAR integration with Code42 helps security teams accelerate incident response and automate the remediation of insider threat activities. Security operation teams can streamline alerts by ingesting Code42 data into Cortex XSOAR for complete incident context on exfiltrated files, such as: user name, file name, exposure type, data source, and more.
Insider threat investigators can gain additional insights about users on and off network by adding users to Code42 via Cortex XSOAR. SecOps teams can search and investigate risky file movements across endpoints, email, cloud and SaaS apps without leaving Cortex XSOAR, and they can close incident tickets faster by automating response and remediation procedures.
Let’s examine one of the most challenging scenarios of data exfiltration activity associated with an employee leaving their organization to join a competitor. The looming economic uncertainty has forced several organizations to undergo restructuring and repurpose their staff as they respond by reinventing and repositioning themselves to meet new market demands amid changing government guidelines.
Meet John, who after four years at QRST Inc. was passed for a promotion and ended up accepting a lucrative job offer at a competitor but not before attempting to exfiltrate sensitive confidential information from QRST Inc.

John is a potential risk for the organization and there is a high chance that he may end up causing data theft. Security teams can add John to the Code42 departing employee lens directly from Cortex XSOAR incident war room to keep track of any intentional data exfiltration activity by John during the notice period.
Security analysts can alternately also edit the built in out-of-the-box “Employee Off-boarding” playbook in Cortex XSOAR and add a new Code42 task to automatically add selective or all departing employees to the Code42 “departing employee” lens.


The Cortex XSOAR war room has a built-in CLI (command line interface) that also doubles up as a ChatOps collaboration facility, unique for each investigation. Post-organization restructuring, the security admin uses the war room functionality to add John to the high-risk departing employee lens of Code42 and subsequently notifies and confirms to the team lead that John has been successfully added to the Code42 lens.

Based on the nature of the insider threat activity, QRST Inc. has specified an organization wide SLA with a corporate policy around insider threat investigation, that requires notifying all the stakeholders, including the employee’s manager, legal, HR, and compliance teams, in case of any data exfiltration activity.
One of the guidelines mandates further scrutiny in case the employee happens to be a part of the executive team with access to company’s sensitive confidential information such as product design, financial information, etc., and, in such cases, the investigation is narrowed down to select few members of the investigation team.
Based on this, the security operations team at QRST Inc. has used the out-of-the-box “Code42 Exfiltration” playbook in Cortex XSOAR and tweaked it to meet their corporate data security policy measures. The playbook performs the following actions:

Let's see how Cortex XSOAR playbook kicks in and comes to the aid of QRST Inc.’s security operations team, when John attempts to exfiltrate sensitive confidential information during his notice period. Code42 generates an alert “Exposure on an endpoint” that shows up on the incidents page of Cortex XSOAR as shown below.

The security analyst on the shift, who has expertise with insider threat investigation, receives the alert on his Cortex XSOAR app on his phone and takes ownership of this incident. This also triggers an active investigation in Cortex XSOAR, and the associated playbook automatically runs and completes the initial investigation within the SLA timeframe, populating the “Incident info” dashboard section with relevant information.
This reduces chances for any human error and saves time for the security team as the analyst doesn’t really have to perform any manual task related to the initial data gathering or even actively responding through manual operations.

As seen below, the investigation data has already captured specific information that provides complete context around John as well as the endpoint that he used to exfiltrate confidential information:

Similarly the “File events” section captures the following information:
This information on exfiltrated files is helpful in understanding the exact piece of information and its value to the organization. Additionally, this information is also readily documented in the war room and evidence board sections for cross functional team viewing.
Let’s now take a look at some of the actions that were automatically executed by the playbook in response to this alert.
 Task Details Sent Email to Manager
Task Details Sent Email to Manager Cortex XSOAR playbook
Cortex XSOAR playbook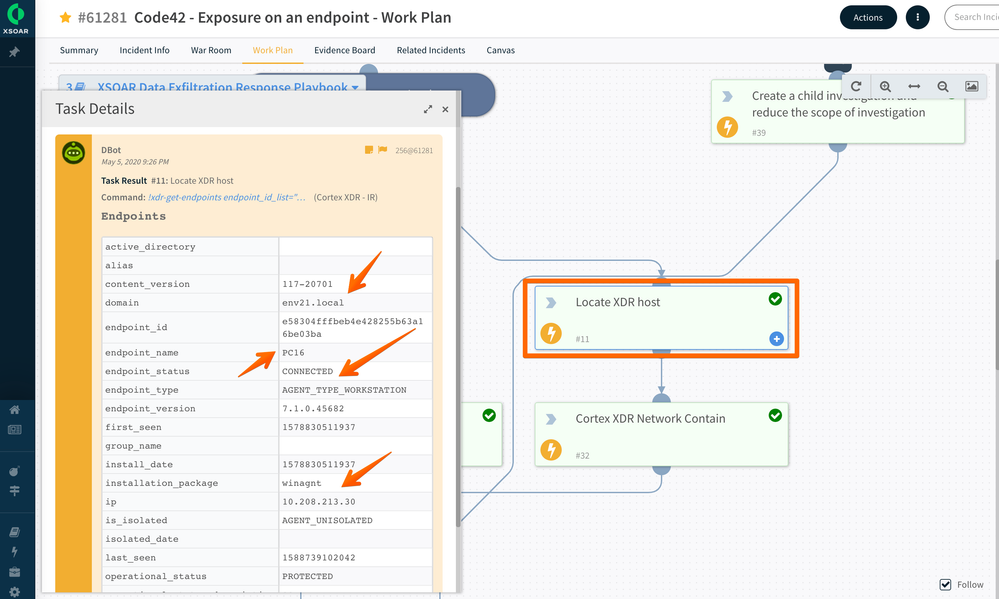 Code42 Exposure on Endpoint Task Details
Code42 Exposure on Endpoint Task Details Cortex XDR Network Contain
Cortex XDR Network Contain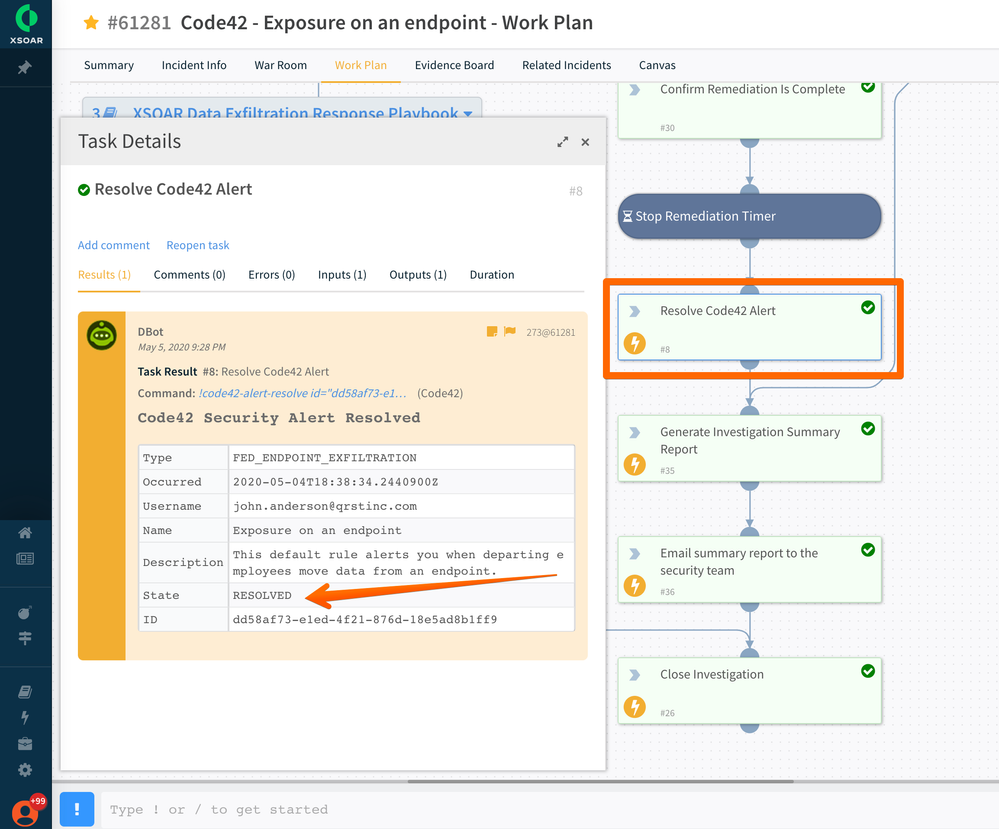 Resolved Code42 Resolved Alert
Resolved Code42 Resolved Alert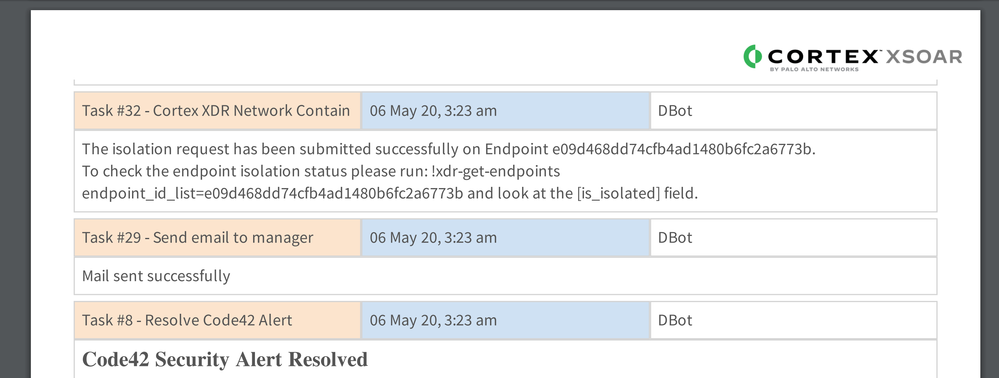 Cortex XSOAR view of Summary
Cortex XSOAR view of Summary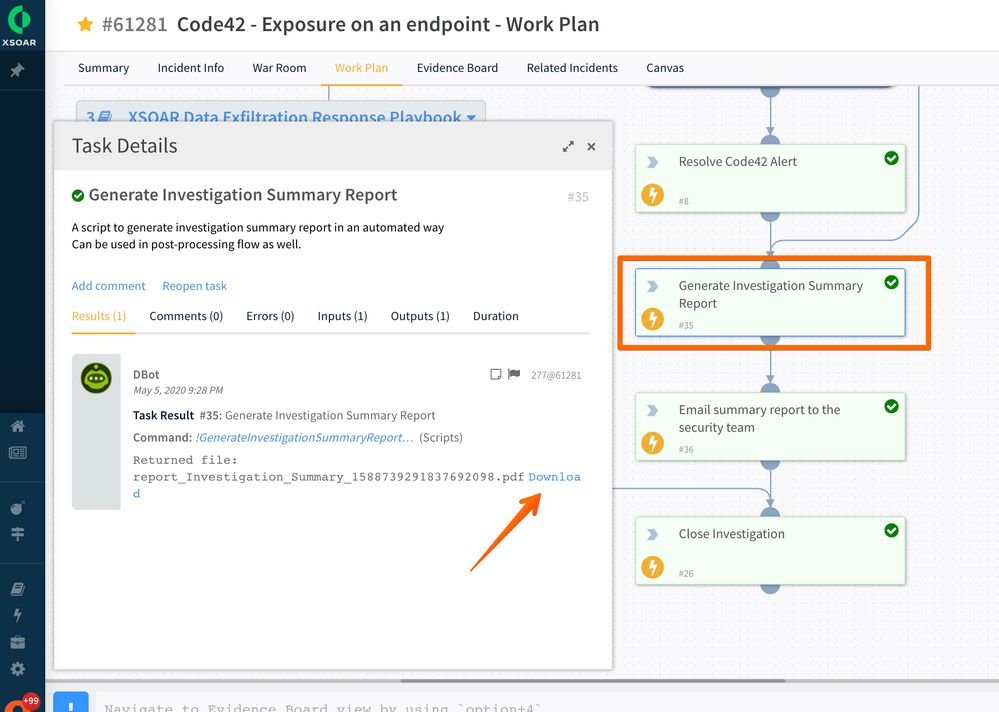 Task Details of investigation summary report
Task Details of investigation summary report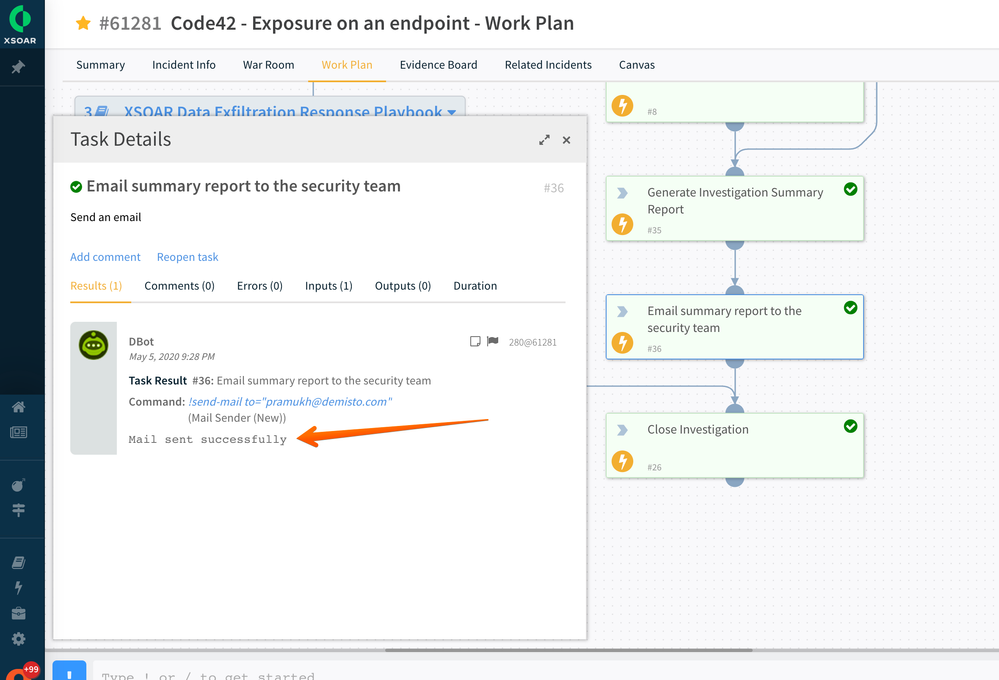 Email Example of investigation summary report
Email Example of investigation summary report
In summary, when an employee submits notice or when an organization is going through workforce changes, security teams can quickly identify potential file exfiltration activities across endpoints, email, cloud, and SaaS applications. Then when risky file activity occurs, such as an upload to a personal Dropbox or a transfer to a USB, the Code42 exfiltration playbook is triggered from within Cortex XSOAR, creating an incident.
The end result for security teams is complete incident context about exfiltrated files, including user, file and exposure type, and data source. Code42 together with Cortex XSOAR enables security teams to scale, standardize, and accelerate their overall response to insider threats.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like | |
| 1 Like |
| User | Likes Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |




