
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Every once in a while, there's a returning question on why SMB traffic is so slow. In this blog, I'll highlight a couple of solutions. Proposed by both community members and TAC engineers, several community members have found these useful and they've helped solve issues in the past.
Searching the LIVE community will already provide you with a couple of links featuring some related discussions and KB articles. These might already provide you a solution or give you some guidance to troubleshoot if you're experiencing this issue:
Allow me to first explain why SMB is a bit of a special protocol and why it's behaving the way it is:
SMB content is inspected differently compared to other protocols, like HTTP or FTP for example. The SMB decoder is unable to implement suspend since file transfers are done in a block-based manner, requiring continuous CTD inspection to follow the protocol on each block. Suspending only for one file could allow evasion for all subsequent files in the same session. ForSMB, every payload is scanned for content inspection and there is no offload mechanism to increase speed. This generally leads to a decreased throughput.
Reading the above already hints to a possible solution/workaround. You can disable content inspection by adding an app-override for this specific traffic, this will allow the session through using fast-path. This approach should be used only if other fail safes are in place, and only between trusted hosts:
Policies > Application Override
Tips & Tricks: How to Create an Application Override
In case an App Override is not possible because L-7 inspection is required, an alternative workaround would be to disable server response inspection (DSRI). SMB traffic is very chatty by nature. By default, traffic in both directions from client-to-server (C2S) and from server-to-client (S2C) will be inspected. With DSRI, the firewall will only inspect C2S traffic !
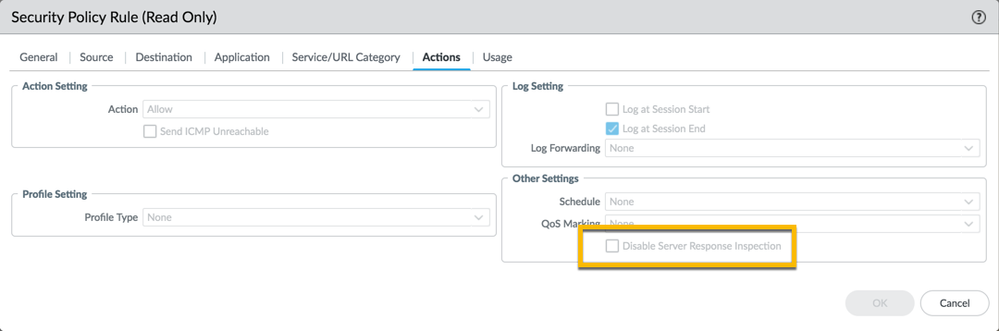
Typically, DSRI is used in environments where internal servers are trusted !!
Note that DSRI is not limited to SMB traffic and can be used on other scenarios as well:
DotW: Using DSRI with the Palo Alto Networks firewall
Improving Performance of HTTP with DSRI
Make sure you're on a recommended PAN-OS release to ensure any issues encountered are not caused by software. So check out the PAN-OS Software Release Guidance to confirm you're running the recommended PAN-OS release or if you are in need of an upgrade to rule out eventual bugs from previous software versions.
Sometimes you might have to dig somewhat deeper or even have Palo Alto Networks Support look into the issue. Here are some additional debugging steps or troubleshooting tips you can look into:
Can you think of additional debugging/troubleshooting steps or workarounds for this popular topic? Please share your experience and possible solutions in the comments section below!
Thanks for taking time to read this blog.
If you enjoyed this, please hit the Like (thumb up) button, don't forget to subscribe to the LIVEcommunity Blog area.
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 5 Likes | |
| 3 Likes | |
| 3 Likes | |
| 3 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 12 | |
| 4 | |
| 3 | |
| 3 | |
| 2 |




