
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
 Protecting Kubernetes and IaaS Workloads in AWS
Protecting Kubernetes and IaaS Workloads in AWSIn addition to securing traditional IaaS workloads, Palo Alto Networks is excited to offer protection for your Elastic Kubernetes Workloads in AWS using the Palo Alto Networks Virtual firewall.
In AWS, customers leverage the VM-Series as an ingress security gateway for traditional IaaS workloads. In addition to the native security functionality offered by AWS, the VM-Series augments native cloud security by delivering first-class application visibility, control, and threat prevention. VM-Series support for Kubernetes further strengthens our capabilities in cloud security and will help customers accelerate their journey to the cloud with consistent and comprehensive protection across EKS workloads.
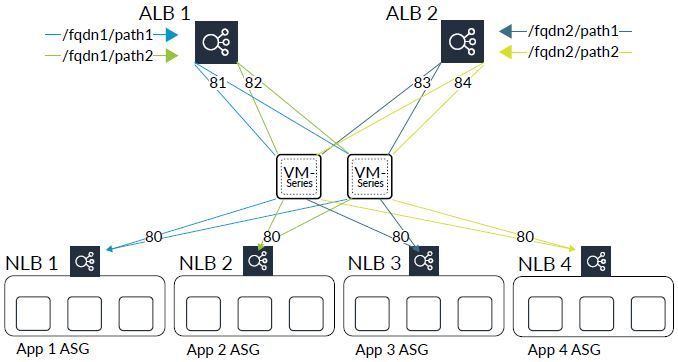 Load balancers in a hub-and-spoke architecture.
Load balancers in a hub-and-spoke architecture.
The plugin uses the Kubernetes Python SDK to retrieve information related to services deployed in your cluster. The plugin queries for services that are labeled panw-tg-port and are assigned a valid port value. The plugin uses the port to create an inbound NAT rule on the VM-Series firewall. When traffic hits the firewall on that specified port, Panorama applies the inbound NAT rule for that port and routes the packet to its destination.
For both the AWS Auto Scale and AWS EKS architecture, the cloud formation templates automate the deployment. For the autoscaling template, Lambda configures the static information needed to automatically route traffic. For Kubernetes deployments, the Panorama plugin for EKS configures the static route in the VM-Series firewall set to route traffic to the desired destination. NAT rules are added to perform address translation on inbound packets, ensuring that the initial traffic, as well as the return traffic, passes through the firewall. This deployment model provides a seamless cloud-centric approach to using the VM-Series to secure IaaS and EKS workloads in the cloud.
You can download the AWS Auto Scale and EKS templates on GitHub using the following links:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 1 Like | |
| 1 Like | |
| 1 Like | |
| 1 Like | |
| 1 Like |
| User | Likes Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |




