- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Analytic BIOC Rules, right click open in query builder, informational severity not available
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Analytic BIOC Rules, right click open in query builder, informational severity not available
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Analytic BIOC Rules, right click open in query builder, informational severity not available
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 07:04 AM
We have a support ticket open for "informational" analytic BIOC rules that are not alerting.
These do not show up in the incidents or alert table, but the number of alerts in that column has more than 0
Support has indicated there is not a way to view the hits of the rule
Does anyone know a way to view these analytic bioc rule alerts
When viewing normal bioc rules, you can right click and open in query builder.
This option isn't available when looking at analytic bioc rules.
Is there a place or way to view how the rule is structured...what the xql query is?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2022 09:45 PM - edited 05-11-2022 09:46 PM
The below article can best explain you the logic behind all the ABIOC rules setup in Cortex.
In general, informational alerts will only show up when an incident is triggered and get stitched with other alerts as part of insights in an incident to help better understand the incident.
Speaking for myself, if we start investigating into informational alerts then we will end up chasing false positives but there might be cases where your investigation might lead to a possible suspicious activity.
In order to find the suspicious activity you will first need to know some start point. For example:
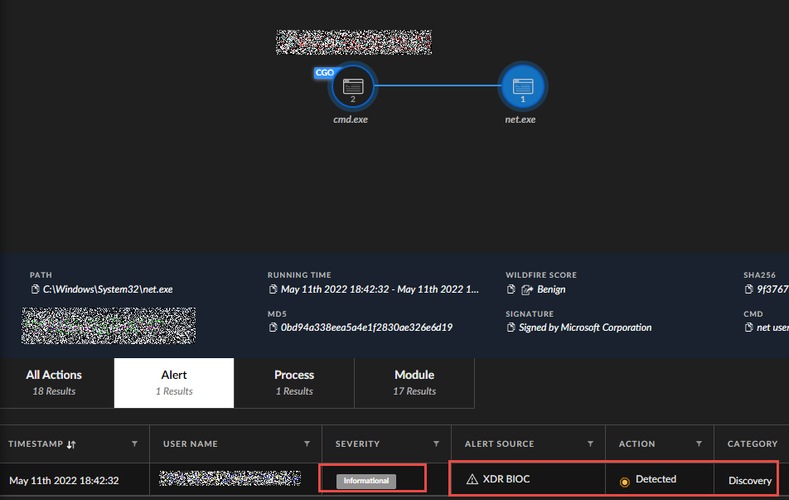
In this cases we are looking for a command called "net user" (we created a BIOC rule to detect this command as informational). So lets say the query returned a result from there on we dig into the causality chain and then click on the process itself and then see the activity for alert as informational. (Not the best way to look for informational alert but does the trick.) You can use a similar logic to find ABIOC informational alerts.
Thank You.
KS
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2022 07:05 AM
Im looking for a way to either see the events that caused the analytic bioc to fire
or a way to view the query behind the rule
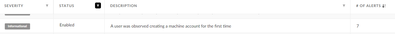
For example the rule below has 7 alerts
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2023 02:05 PM
Wondering how I can hunt for BIOC "elevation of privilege" events, for example pertinent to "CVE-2023-21674 "
- 3753 Views
- 3 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Request for Query to Retrieve Endpoint Security Details. in Cortex XDR Discussions
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- How do you handle Low Severity alerts/issues? in Cortex XSIAM Discussions
- Cortex XDR - Automation Rules in Cortex XDR Discussions
- Regarding the End of Life for Broker VM in Cortex XDR Discussions