- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cortex XDR has Blocked a Malicious Activity but No Program Listed
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Cortex XDR has Blocked a Malicious Activity but No Program Listed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Cortex XDR has Blocked a Malicious Activity but No Program Listed
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 10:08 AM
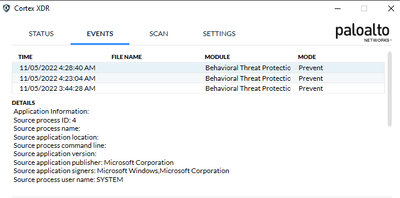
Attached images show the pop-up that is going around our network this morning. Unlike before where it would list the program Cortex blocks there is nothing there and is pointing at Microsoft for the cause.
Is this a false positive? A windows service is triggering Cortex to block the behavioral threat?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 11:09 AM
Hi,
We're seeing the same here as well. End users are shown no application name, but digging through the incidents in the console shows that it's killing of Smss.exe, which is the System Center Configuration Manager agent.
All endpoints generating alerts are running 7.7.0.60725 here.
Looking through the timeline there seems to be no evidence of foul play.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 11:20 AM
We have a Support ticket opened (High Severity) and also are working with an inside (Palo) engineer associated with our Sales team. So hopefully we will learn more soon.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 11:48 AM
@KMcKenna Please let us know if they provide a workaround or a fix for the issue.
Fingers crossed the update either get fixed or pulled tonight, so I won't have to deal with this when each endpoint boots tomorrow.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 11:59 AM - edited 05-10-2022 12:01 PM
Getting this too. It occurs after the latest content & policy update. I can manually trigger it but clicking check-in now button, so its like the process that applies the policy update is triggering itself lol.
You can verify this in the endpoint log on portal, it triggers same time as the policy
update.
Support case logged also:
CASE #: 02191983
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 12:21 PM
@adminBandE I also clicked Check In Now on a completely isolated host (off site). Had same response as you in that the Alert triggered.
Will add that to our support case. Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 12:25 PM - edited 05-10-2022 12:34 PM
Update from my Case:
From the case description, I understand that you are receiving BTP alerts for smss.exe for the rule other.malware_gen_task.105
I would like to inform you that it is a false positive BTP alert and multiple customers where reported the same. We are working on the fix and will update you as soon as available.
As a workaround please create an alert exception for now reference.
I just created the (temporary) exception, lets see if it takes effect!
Edit: It does work. Apply the alert exception from the incident under alerts & insights, right-click the alert and select manage alert - create alert exception. It will then appear under your global BTP rules.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 12:39 PM
We are being told this is a False Positive and the Palo Support team is working on it. They say to create an exclusion in the meantime. Some general info on doing that...
This is a general Docs page. So if you are not familiar with doing this, you may need more info. This is linked info not specific to this alert.
That's all I have at the moment.
- 30916 Views
- 20 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Blocking Intel process in Cortex XDR Discussions
- Can Cortex XDR fully substitute for Microsoft Defender Attack Surface Reduction (ASR) rules? in Cortex XDR Discussions
- Disable notification in user agent in Cortex XDR Discussions
- Alert "Script Activity - 245655498" in Cortex XDR Discussions
- After pushing content from Dev to Prod, we are seeing lot of errors in XSOAR in Cortex XSOAR Discussions