- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Detect and Restrict Powershell cmdlets
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: Detect and Restrict Powershell cmdlets
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2024 07:57 AM
Hello everyone,
I would like to know if any of you have struggled with support and technical cases with the need I show below.
I would like to know what you can tell me or give me your opinion about taking action against powershell cmdlets.
After several cases and meetings with support, I can't get a solid answer to my needs about restricting some powershell cmdlets.
I hope to find a solution that fits my needs, thanks anyway.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2024 07:25 AM - edited 04-24-2024 07:27 AM
Hi @agirones, I believe that this could work for you.
- Create a new custom BIOC rule going to Detection Rules - BIOC
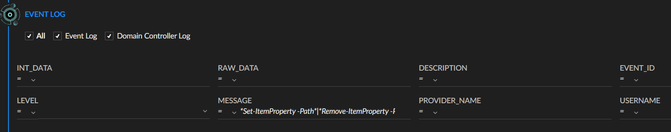
- Select the Event Log type. The powershell cmdlets details are taken from the windows event log.
- Set a name, and put all the required commands in the "Message" field in this format:
*Set-ItemProperty -Path*|*Remove-ItemProperty -Path*|*Invoke-AADintReconAsOutsider*|*Remove-DomainObjectACL*
Use the "|" character as an OR separator, and the "*" as wildcard.
- Before save it you can test it to check if you have some matching events.
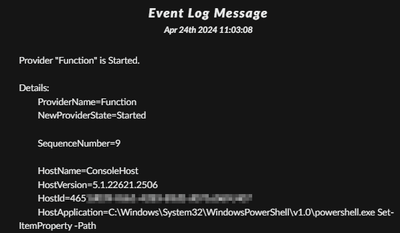
- You will see the command details by opening the "View event log message" from the results.
- This is how you will see the details:
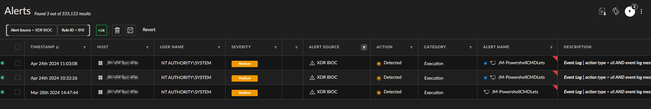
- Alerts generated:
This works for cmdlets running in a live powershell console in the host, and it will also detect this commands running from scripts.
The "Event log" type BIOC Rules can't be used to block, only for notifications.
If this post answers your question, please mark it as the solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2024 10:37 AM
Hi @agirones, thanks for reaching us using the Live Community.
Can you share more information about what cmdlets you are trying to detect or block? Do you have some example?
Maybe I can do some test in my lab and try to help you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2024 11:25 PM
Hi @jmazzeo, thaks for your interest and trying to help!
Example, I want to restrict cmdlet like:
Set-ItemProperty -Path
Remove-ItemProperty -Path
Invoke-AADintReconAsOutsider
Remove-DomainObjectACL
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2024 07:25 AM - edited 04-24-2024 07:27 AM
Hi @agirones, I believe that this could work for you.
- Create a new custom BIOC rule going to Detection Rules - BIOC
- Select the Event Log type. The powershell cmdlets details are taken from the windows event log.
- Set a name, and put all the required commands in the "Message" field in this format:
*Set-ItemProperty -Path*|*Remove-ItemProperty -Path*|*Invoke-AADintReconAsOutsider*|*Remove-DomainObjectACL*
Use the "|" character as an OR separator, and the "*" as wildcard.
- Before save it you can test it to check if you have some matching events.
- You will see the command details by opening the "View event log message" from the results.
- This is how you will see the details:
- Alerts generated:
This works for cmdlets running in a live powershell console in the host, and it will also detect this commands running from scripts.
The "Event log" type BIOC Rules can't be used to block, only for notifications.
If this post answers your question, please mark it as the solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2024 09:09 AM
Hey @jmazzeo,
Thanks, I know this detection functionality, together with an automation with "terminate casuality chain" that kills the powershell process can be a "solution".
This feature requires XTH - Xtended Threat Hunting license (which I don't have).
The only drawback I see to this solution is that it is an asynchronous solution (it works after executing the command, in this case the cmdlet).
- 1 accepted solution
- 2411 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!