- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Why there are no related alerts on scanned malicious files.
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: Why there are no related alerts on scanned malicious files.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Why there are no related alerts on scanned malicious files.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2023 12:45 AM - edited 06-10-2023 12:54 AM
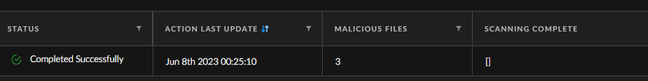
Hi, we have recently malware scanned an endpoint and upon checking the results, it appears that there were 3 malicious files on the host.
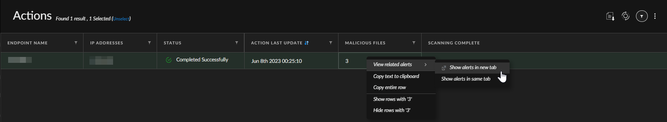
Now, I tried to right click and view related alerts on the 3 malicious files and it just shows nothing. What's weird about this is it showing MD5 hashes on External ID field. I checked those hashes via ThreatVault and VirusTotal and it doesn't give any results.
Now my question is how are we suppose to track the 3 malicious files as per malware scan when we have no idea what it is and Cortex showing not enough insight. Checking the historical incidents on this host in regards of malicious files, I only see one WildFire related incident for the past few months.
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2023 05:14 AM
Hi @aaronquiamco ,
Thank you for writing to live community.
By default the Cortex XDR will generate alerts with action Detected(Scanned) whenever it scans a malicious file. As a result, you should have the alerts present there. It seems that you have a filter applied on External ID which is not clear enough to describe whether you received the alert or not. You can use the filter for endpoint name and alert action for the use case as shown below:
| Host= <Hostname> AND Alert Source= XDR Agent AND ACTION =Detected(Scanned) |
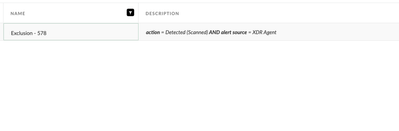
If the above still does not yield any output for you, it is probable that there is an Alert Exclusion rule created for the parameters which will exclude and suppress alerts either from the endpoint or for the scanned as an action. Example of an alert exclusion configuration could be as shown below in the image.
Hope this helps. Please mark the response as "Accept as Solution" if it answers your query.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2023 07:02 AM
Hello,
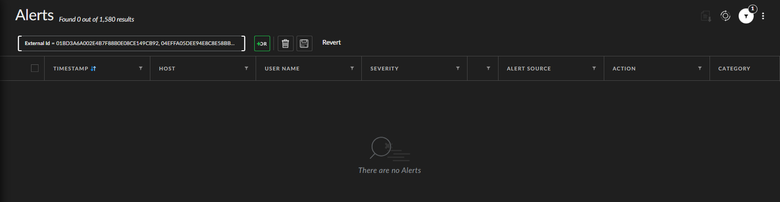
I really need help on this one as we have no idea where we can pull out the 3 malicious files via Malware Scan option.
I highly doubt there was alert exclusions made on the host as this is a workstation and needs to be monitored always. I have also checked alert exclusions page and there were none related to the endpoint we malware scanned.
I have checked through this:
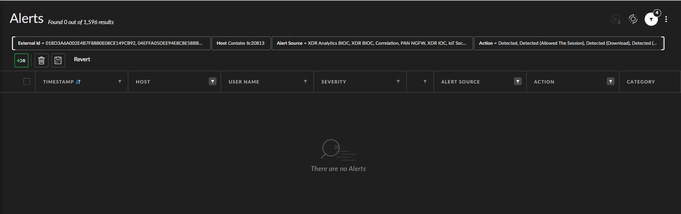
And set additional search parameters but it still did not show anything:
Now may I ask what is the best way for us to approach this kind of scenario? We don't know if the malware scan result is a false positive or there's a legitimate malicious files on the host itself.
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2023 07:19 AM
Hi @aaronquiamco ,
Please remove the External ID from the filter and try using the filter mentioned in the previous response. Simply use:
Host=<Endpoint Name> AND and action= Detected(Scanned)
Please see if it gives you results. I am assuming that there could be issue in the External ID filter.
If none of the above works, please retrieve the Tech Support files from the endpoint and provide the tenant information from the About page and open a case with Palo Alto networks support for break fix.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-13-2023 02:23 PM
May I get the link for the open a case section with Palo Alto networks support.
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2025 10:53 PM
Hi @aaronquiamco , hope you are doing well.
I encounter the same as well. By any chance, can you share the solution if you opened a case with TAC?
- 3540 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Repeated False Incidents with Unknown Verdicts in Cortex XDR Discussions
- On-demand file Examination policy in Cortex XDR Discussions
- XQL Query - Machine Custom Reports in Cortex XDR Discussions
- Kandji MDM in Cortex XDR Discussions
- Why there are no related alerts on scanned malicious files. in Cortex XDR Discussions