- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
XQL Query for CVE-2021-1675 exploitation attempts (printnightmare)
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- XQL Query for CVE-2021-1675 exploitation attempts (printnightmare)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
XQL Query for CVE-2021-1675 exploitation attempts (printnightmare)
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 11:40 AM
Hi Community
I need some help in creating an XQL query for a BIOC which detects exploitation attempts for CVE-2021-1675 (printnightmare). So far I have the following two queries:
1. A query that detects incoming connections on port 445
dataset = xdr_data
| filter event_type = NETWORK and event_sub_type = NETWORK_STREAM_ACCEPT and (action_local_port = 139 or action_local_port = 445)
| fields event_type, agent_hostname as Hostname, action_local_ip as Local_IP, action_remote_ip as Remote_IP, action_external_hostname as Remote_Host, action_local_port as Local_Port, actor_process_image_name as Process_Getting_Connection2. a query to view driverinstallations done by the print spooler service
dataset = xdr_data
| filter causality_actor_process_image_path = "C:\Windows\System32\spoolsv.exe" and actor_process_image_path = "C:\Windows\System32\drvinst.exe"
| fields agent_hostname as host_name, causality_actor_process_image_name as CGO_Name, causality_actor_process_image_path as CGO_Path, causality_actor_process_command_line as CGO_CMD, causality_actor_primary_username as Username, actor_process_image_path as child_path, actor_process_command_line as child_cmd, actor_process_os_pid as child_pid, actor_process_image_sha256 as child_sha256, actor_process_execution_time as start_date, event_idNow I'd like to combine them somehow in order so get an alert for incoming connections over SMB which result in a driverinstallation done by the print spooler service. Has anyone done something similar or is able to help me with this XQL query?
Thanks in advance,
Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 12:27 PM
Hi Remo! If it helps, take a look at our blog post on PrintNightmare for suggested XQL queries: https://www.paloaltonetworks.com/blog/security-operations/hunting-printnightmare/
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 02:35 PM
Hi @kcross
Thanks for sharing that link. This definately helps already.
Even if there are already some queries shared by Paloalto, I am still interested if my initial query is possible with this combination.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-02-2021 11:43 AM - edited 07-02-2021 12:37 PM
@Remo wrote:Hi Community
I need some help in creating an XQL query for a BIOC which detects exploitation attempts for CVE-2021-1675 (printnightmare). So far I have the following two queries:
1. A query that detects incoming connections on port 445
dataset = xdr_data
| filter event_type = NETWORK and event_sub_type = NETWORK_STREAM_ACCEPT and (action_local_port = 139 or action_local_port = 445)
| fields event_type, agent_hostname as Hostname, action_local_ip as Local_IP, action_remote_ip as Remote_IP, action_external_hostname as Remote_Host, action_local_port as Local_Port, actor_process_image_name as Process_Getting_Connection
2. a query to view driverinstallations done by the print spooler service
dataset = xdr_data
| filter causality_actor_process_image_path = "C:\Windows\System32\spoolsv.exe" and actor_process_image_path = "C:\Windows\System32\drvinst.exe"
| fields agent_hostname as host_name, causality_actor_process_image_name as CGO_Name, causality_actor_process_image_path as CGO_Path, causality_actor_process_command_line as CGO_CMD, causality_actor_primary_username as Username, actor_process_image_path as child_path, actor_process_command_line as child_cmd, actor_process_os_pid as child_pid, actor_process_image_sha256 as child_sha256, actor_process_execution_time as start_date, event_id
Now I'd like to combine them somehow in order so get an alert for incoming connections over SMB which result in a driverinstallation done by the print spooler service. Has anyone done something similar or is able to help me with this XQL query?
Thanks in advance,
Remo
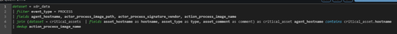
Hello Remo,
You can combine both queries with an union statement. Here is an example union statement;
XQL Helper Screenshot:
Also, I've taken the liberty of combining your queries using the union statement
dataset = xdr_data
| filter event_type = NETWORK and event_sub_type = NETWORK_STREAM_ACCEPT and (action_local_port = 139 or action_local_port = 445)
| fields event_type, agent_hostname as Hostname, action_local_ip as Local_IP, action_remote_ip as Remote_IP, action_external_hostname as Remote_Host, action_local_port as Local_Port, actor_process_image_name as Process_Getting_Connection
| union (dataset = xdr_data
| filter causality_actor_process_image_path = "C:\Windows\System32\spoolsv.exe" and actor_process_image_path = "C:\Windows\System32\drvinst.exe"
| fields agent_hostname as host_name, causality_actor_process_image_name as CGO_Name, causality_actor_process_image_path as CGO_Path, causality_actor_process_command_line as CGO_CMD, causality_actor_primary_username as Username, actor_process_image_path as child_path, actor_process_command_line as child_cmd, actor_process_os_pid as child_pid, actor_process_image_sha256 as child_sha256, actor_process_execution_time as start_date, event_id)
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2021 05:54 AM
Hi @yalonso
Thank you for your reply. I tried this command shortly but unfortunately this gives way too much results. Mainly because it simply shows all results from both queries in one resulttable. My goal still somehow is to search for driverinstallations by spoolsv.exe that are triggered from a remote host.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2021 06:36 PM
You may have to tweak your queries to combine by using "join". Here's a sample of join
- 7070 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can Cortex XDR fully substitute for Microsoft Defender Attack Surface Reduction (ASR) rules? in Cortex XDR Discussions
- Exploits Protection interfering with browser launch in Cortex XDR Discussions
- LDAPNightmare: SafeBreach Labs Publishes First Proof-of-Concept Exploit for CVE-2024-49112 in Cortex XDR Discussions
- high priority 'Behavioral Threat' alert for smss.exe (system)? in Cortex XDR Discussions
- Help with Memory corruption exploitation event in excel.exe in Cortex XDR Discussions