- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Limiting File Size Upload using Custom Signature
- LIVEcommunity
- Discussions
- Custom Signatures
- Limiting File Size Upload using Custom Signature
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Limiting File Size Upload using Custom Signature
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2016 12:55 AM
Users in enterprise often use web based file hosting to upload big files. This creates concerns in the usage of networks bandwidth and server storage capacity, as the file can be bigger than 1GB. Below steps are usefull to control file size uploaded to a web server using HTTP Request Content-Length parameter.
PAN-OS version: 6.1.0-b43
- Create a custom signature vulnerability
Go to Objects Tab > Custom Objects > Vulnerability, then click “Add”,
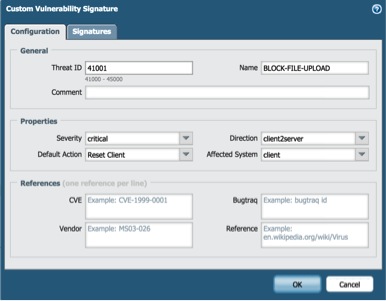
Fill-in required fields as shown below:
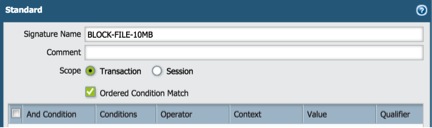
Click “Signatures” Tab, then click “Add”. In Standard window, type in the Signature Name:
At the bottom of “Standard” window, click “Add And Condition”:
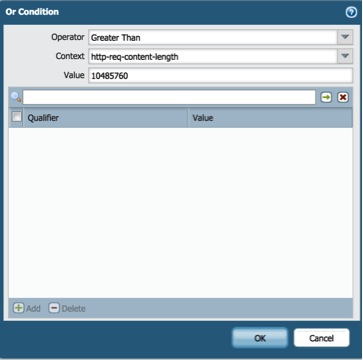
Inside “Or Condition” window, choose Operator to “Greater Than”, choose Context to “http-req-content-length”. To limit file size up to 10 MB, we need to fill-in the Value in bytes, 10MB equals to “10485760”
Then click “OK”, click “OK” again.
Or, you can just save below text as BLOCK-FILE-10MB.xml file and click “Import” in Objects Tab > Custom Objects > Vulnerability.
<vulnerability-threat version="6.1.0">
<entry name="41001">
<signature>
<standard>
<entry name="BLOCK-FILE-10MB">
<and-condition>
<entry name="And Condition 1">
<or-condition>
<entry name="Or Condition 1">
<operator>
<greater-than>
<value>10485760</value>
<context>http-req-content-length</context>
</greater-than>
</operator>
</entry>
</or-condition>
</entry>
</and-condition>
<order-free>no</order-free>
<scope>protocol-data-unit</scope>
</entry>
</standard>
</signature>
<default-action>
<reset-client/>
</default-action>
<threatname>BLOCK-FILE-UPLOAD</threatname>
<severity>critical</severity>
<direction>client2server</direction>
- Create a Vulnerability Protection profile
Go to Objects Tab > Security Profiles > Vulnerability Protection, then click “Add”,
You can name the profile as “VP-FILE-UPLOAD”:
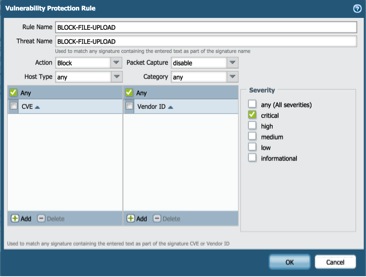
Then click “Add”, and fill-in Rule Name, Theat Name, and others similarly as below picture:
After finish, then click “OK”, click “OK”.
- Create Security Policy
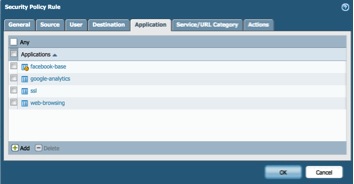
Go to Policies Tab > Security, then create security policy similarly as below:
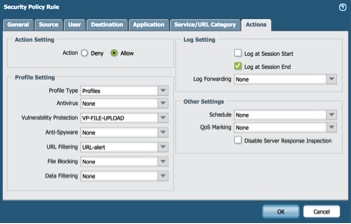
Don’t forget to assign vulnerability protection profile “VP-FILE-UPLOAD” under “Actions” tab:
Click “OK”, then click “Commit”.
- File Upload Testing
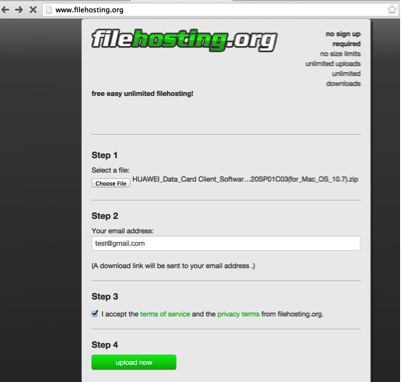
Open the browser, and type www.filehosting.org
Click “Choose File”, then find any file larger than 10MB:
When uploading a file with size more than 10MB (10485760 bytes), the firewall block and reset the connection.
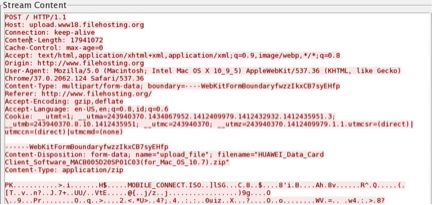
Below is the capture of the packet that show “Content-Length” value is more than 10MB:
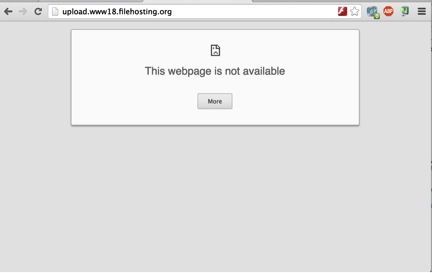
And the browser shows blank page:
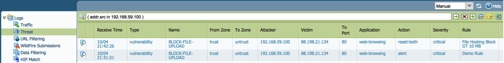
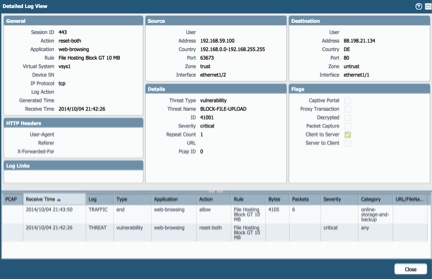
- Check Firewall Threat Logs
Threat Logs shows the firewall catch “Content-Length” parameter which is greater than allowable size.
- 5486 Views
- 0 replies
- 3 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- DNS req/res does not work with "transaction" scope in Custom Signatures
- How to specify multiple conditions for the "test custom-signature-perf" command in Custom Signatures
- Can Copilot help with writting of custom application or vunrability signatures on NGFW or Prisma Access? in Strata Copilot Discussions